North Korean Lazarus APT phishing defense contractors

A new cyber attack campaign launched by North Korean APT Lazarus Group is targeting the military defense industry. Lazarus weaponized two documents related to job opportunities from Lockheed Martin in the spear phishing attack. The discovery was made January 18, 2022. Here’s what you need to know: What might the hackers be looking for? North […]
Red Team Tooling: Writing Custom Shellcode

Overview This article discusses our recently open-sourced tool Matryoshka [1], which operators can leverage to bypass size limitations and address performance issues often associated with Visual Basic for Applications (VBA) macro payloads. Because Microsoft Office restricts the size of VBA macros, operators can run into size limitations that restrict their ability to include larger payloads […]
Red Team Privilege Escalation – RBCD Based Privilege Escalation – Part 2

Overview In part one, we covered a Windows local privilege escalation method we have leveraged during red team engagements that is particularly prevalent on multi-user systems with many installed applications, such as Citrix. In part two, we cover another common local privilege escalation vulnerability we have leveraged within Windows domain environments to escalate privileges on […]
Reproducing the Microsoft Exchange Proxylogon Exploit Chain

Introduction In recent weeks, Microsoft has detected multiple 0-day exploits being used to attack on-premises versions of Microsoft Exchange Server in a ubiquitous global attack. ProxyLogon is the name given to CVE-2021-26855, a vulnerability on Microsoft Exchange Server that allows an attacker to bypass authentication and impersonate users. In the attacks observed, threat actors used […]
Red Team Local Privilege Escalation – Writable SYSTEM Path Privilege Escalation – Part 1

Overview In this two-part series we discuss two Windows local privilege escalation vulnerabilities that we commonly identify during red team operations. These issues are of particular interest due to their prevalence within organizations with mature security programs. Furthermore, exploitation of the issue is unlikely to trigger a detection within commonly used endpoint and network monitoring […]
Building a Domain Specific Language for Red Team Payload Generation

This article shares how Praetorian developed a customer YAML-based domain-specific language (DSL) to specify red team dropper behavior.
Inside the Mimikatz Pass-the-Hash Command (Part 2)

Second in a two-part series providing an overview of how the Mimikatz pass-the-hash command works.
Inside the Mimikatz Pass-the-Hash Command (Part 1)

First in a two-part series providing an overview of how the Mimikatz pass-the-hash command works.
Red Team Infrastructure Tooling: Command Line Utilities and U2F
This article shares observations and best practices for red team infrastructure tooling, with a focus on command-line applications to manage server infrastructure.
Praetorian’s Approach to Red Team Infrastructure
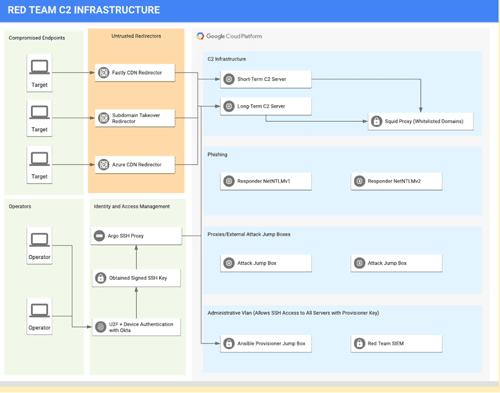
Praetorian provides a best practices approach to Red Team Infrastructure using a Google BeyondCorp architecture