In Brief: Chariot Alignment with FDA Section 524B.1

Chariot is more than a product; it’s a partnership that combines automated monitoring and human analysis to identify externally-accessible security risks. In light of the FDA’s latest requirements for in-market device security (summarized in Section 524B), Praetorian’s customers are having success leveraging the Chariot Managed Service as a cost-effective and scalable approach to satisfying Section […]
Cyber Cartography: Mapping a Target
As Phil Venables has said, “at some level, cyber defense is a battle over whether the attacker or defender has better visibility of the target. Action is key, yes, but without good ‘cyber cartography’ it can be hard to act in the right way.” An attacker’s first step is enumeration, or identifying what looks hackable. […]
Open Source Tools: From Our Lab to Your Fingertips
One of the core decisions we’ve made at Praetorian is to maximize efficiency and effectiveness. In pursuit of this, we carefully select and implement automation and technical solutions for tasks that don’t need human attention. The key is choosing thoughtfully developed tech and tools; when we can’t find what we need, we create it ourselves! […]
ABAC in Lambda
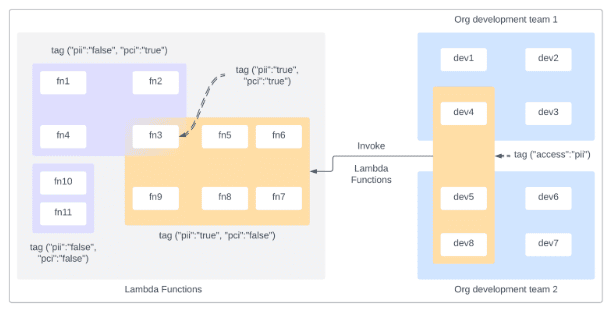
During August 2022 we published a blog discussing AWS Security Trends of 2022 , one of which was ABAC in Lambda. AWS allows administrators to use tags to designate attributes for both IAM and AWS resources. Attribute Based Access Control, or ABAC, is a strategy to allow permissions assignment based on the value of such […]
Six Months of Finding Secrets with Nosey Parker
Earlier this year we announced Nosey Parker, a new scanner that uses machine learning techniques to detect hardcoded secrets in source code with few false positives. Since then we’ve continued its development and expanded its use in security engagements at Praetorian. In a few cases Nosey Parker has contributed to critical-severity findings, such as complete […]
Part I – CyberSecurity is Adversarial, and What that Means for Security Strategy
I have an impression that in the course of the day to day grind, many security leaders have lost sight of a core tenant of cybersecurity: that it is adversarial. Ultimately, the core of most cybersecurity risks is defenders trying to stop attackers. Both sides are seeking to outwit each other. This contest is mediated […]