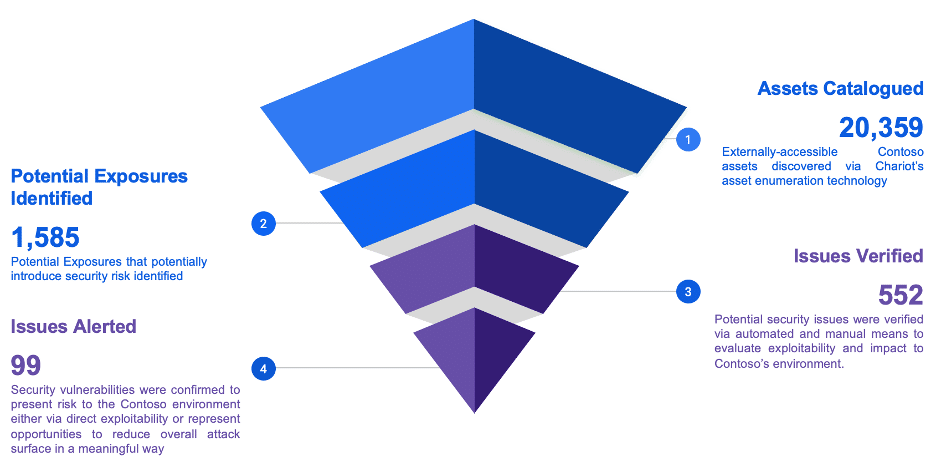
The Power of Chariot Managed Service
The landscape of cybersecurity is one of constant, rapid change, challenging organizations to keep pace with emerging threats. Organizations search for a tool or product that holistically enhances their cybersecurity program and gives them peace of mind – a silver bullet. Unfortunately, no single vendor offers silver bullets. With budgets tightening, cybersecurity leaders may face […]
MOVEit! An Overview of CVE-2023-34362
On May 31st, 2023, Progress disclosed a serious vulnerability in its MOVEit Transfer software. The vulnerability is remotely exploitable, does not require authentication, and impacts versions of the software that are 2023.0.1 (15.0.1) or earlier. We are aware of multiple reports of active exploitation of this vulnerability in the wild, and attackers are already mobilizing […]
Content Discovery: Understanding Your Web Attack Surface
Attack Surface Management (ASM) tools find quite a lot of vulnerabilities on the Web. This really isn’t surprising, given that HTTP/S is by far the most common and broadest of all the services comprising the Internet. In fact, Web-based issues represent the majority of the findings about which our Managed Service Providers (MSPs) inform our […]
Cyber Cartography: Mapping a Target
As Phil Venables has said, “at some level, cyber defense is a battle over whether the attacker or defender has better visibility of the target. Action is key, yes, but without good ‘cyber cartography’ it can be hard to act in the right way.” An attacker’s first step is enumeration, or identifying what looks hackable. […]
ASM: The Best Defense is a Good Offense
About 10 years ago, security was relatively simple because everything occurred on premises. Change releases were tightly controlled by a change ticket and review process. In contrast, current networks consist of auto-scaling containers that run in Kubernetes clusters and even serverless clusters like AWS Lambda. We have transitioned from constrained environments that humans closely scrutinized […]
Safeguarding Memory in Higher-Level Programming Languages
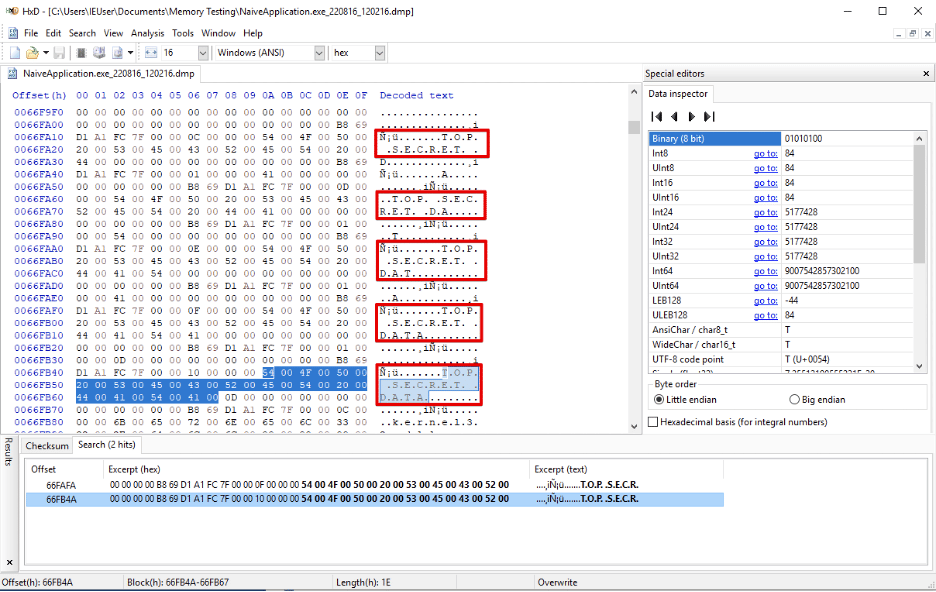
Consider an application written in a higher-level language like Python, NodeJS, or C#. This application must handle sensitive data such as banking credentials, credit card data, health information, or network passwords. The application developers have already hardened the application against malicious users and are confident that it is not vulnerable to database injections, account takeovers, […]
Multi-Step Attack Vectors: When Vulnerabilities Form an Attack Chain
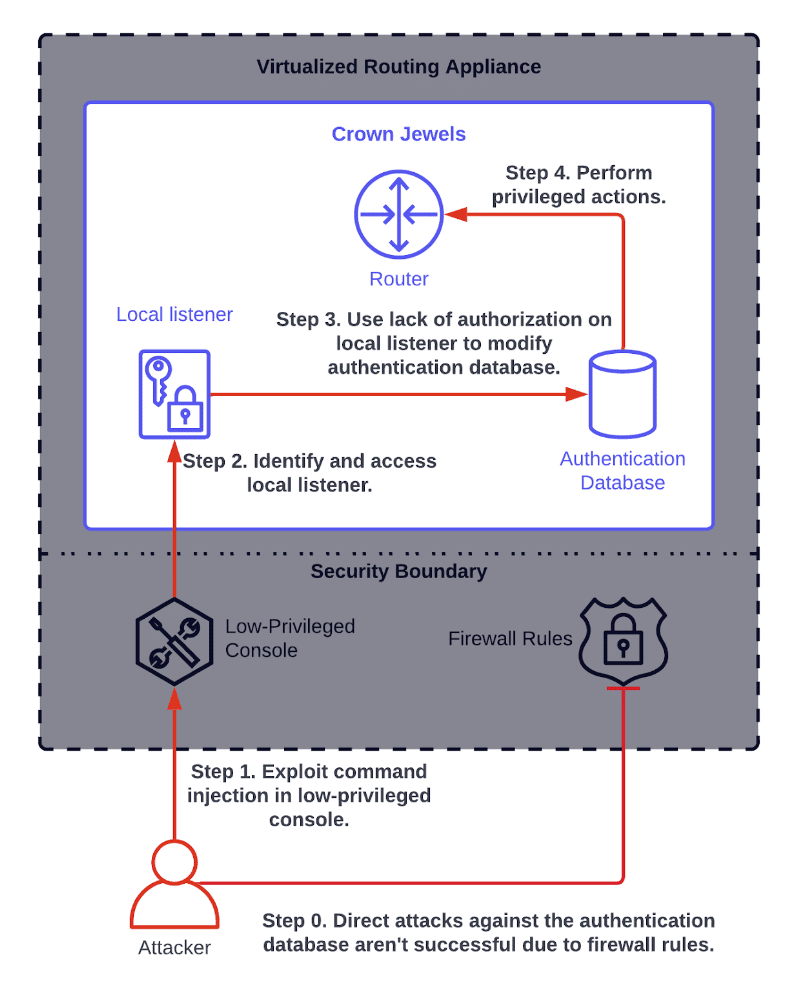
Praetorian’s approach to cybersecurity centers around a core belief that combining innovative technologies and the best people in the business leads to real results. In our experience, neither can fully solve cybersecurity challenges on its own. We therefore have designed our services organization and offerings to blend them seamlessly. We applied the same philosophy when […]
Spring Core on JDK9+ is vulnerable to remote code execution

Update: March 31, 2022 A patch has officially been released. https://spring.io/blog/2022/03/31/spring-framework-rce-early-announcement https://tanzu.vmware.com/security/cve-2022-22965 Overview Spring Core on JDK9+ is vulnerable to remote code execution due to a bypass for CVE-2010-1622. At the time of writing, this vulnerability is unpatched in Spring Framework and there is a public proof-of-concept available. As we have remediation advice for customers […]
Ides of March – Chariot’s Launch Day

Advances in SaaS and DevOps that transform your business also expand the attack surface—all the ways adversaries can exploit your connections to the internet or cloud. Knowing the unknowns is the first step, but the attack surface keeps changing and your risks are multiplied by ransomware and talent shortages. It’s time security goes on offense. […]