The landscape of cybersecurity is one of constant, rapid change, challenging organizations to keep pace with emerging threats. Organizations search for a tool or product that holistically enhances their cybersecurity program and gives them peace of mind – a silver bullet. Unfortunately, no single vendor offers silver bullets. With budgets tightening, cybersecurity leaders may face the need to consolidate their tools and vendors, which inevitably leads to difficult tradeoffs between solutions. Most of these tools create lots of noise, need constant tuning and monitoring, and ultimately still rely on in-house analysts to make the call whether something is a material threat or not. Finding the right third party managed service vendor to take on this task can be a force multiplier for organizations whose internal teams already find themselves stretched thin.
At Praetorian, we hire and retain the top talent in the industry to continually monitor and analyze attack surfaces using the Chariot platform. Expert analysts leverage years of expertise, powerful automation, and contextual awareness to identify the most impactful cyber issues that matter to your organization. As a result, your teams can focus on other priorities.
A Managed Service Cuts the Noise…
Praetorian’s Managed Services team continually cycles through four stages of work, leveraging the Chariot platform to enable comprehensive and rapid analysis. The Funnel (see Figure) shows the volume of findings each stage involves, based on the following definitions:
- Assets Cataloged: We create a comprehensive inventory that spans your entire digital ecosystem through cloud integrations and proactive discovery for real time insights into ephemeral assets, information and resource sharing, and open source intelligence gathering.
- Potential Exposures Identified: With an understanding of your digital footprint, we identify potential vulnerabilities and misconfigurations, leveraging both automated scanning and expert manual investigation.
- Issues Verified: We evaluate potential exposures, verifying which issues are valid and require immediate attention. This ensures efficient resource allocation and eliminates the escalation of false positives.
- Issues Alerted: We alert you to the verified issues that meet your specific alerting criteria, keeping you informed and enabling you to make knowledgeable decisions about your cybersecurity strategy. Our engineers work collaboratively with your team to ensure thorough comprehension of vulnerabilities and tailor remediation guidance to your environment.
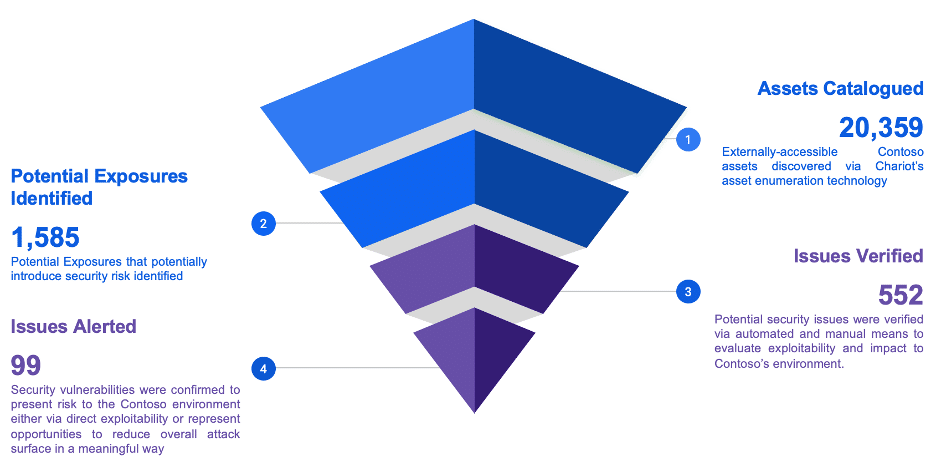
Figure: A sample Funnel of Analysis, which demonstrates the behind-the-scenes work that our team did for a single client before alerting them of material risks.
…By Factoring Context…
Praetorian’s engineers apply client-specific context to gauge the exploitability and potential impact of verified issues before assigning priority labels and escalating to in-house remediation teams. This analysis yields a more practical assessment of the risk present from vulnerabilities in an attack surface, which typically correlates to a significant reduction in the quantity and severity of issues raised for remediation. On average, large enterprise clients using Chariot can expect to see a 10- to 100-fold reduction in the number of assessed medium or higher severity issues.
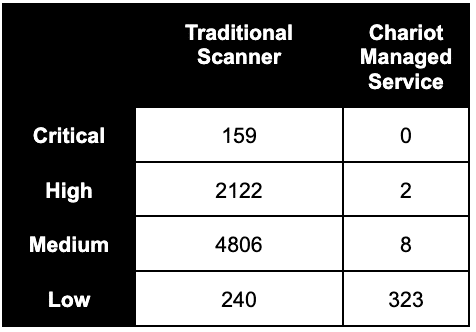
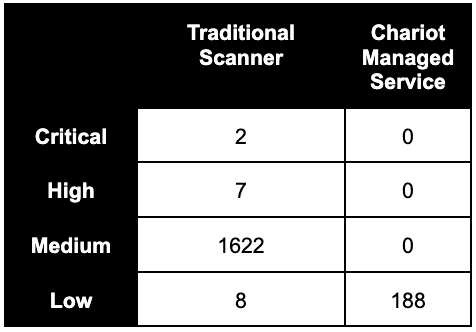
Tables 1 and 2 show a point-in-time view of the number of issues Praetorian’s Managed Service escalates to client teams compared to a traditional vulnerability scanner:
Table 1: Client A, a large enterprise with a diverse attack surface.
Table 2: Client B, a mid-sized enterprise with a homogenous attack surface.
…So Findings Only Escalate When They Matter
A key distinction to note is that, while we see a remarkable reduction in the number and severity of issues flagged for remediation, this doesn’t indicate any overlooking of critical vulnerabilities. On the contrary, we see that the vulnerability validation step allows our engineers to more accurately rate risk according to the clients’ specific risk profile. The platform’s automation and risk analysis capabilities allow our managed services engineers to spend more time examining the nooks and crannies of our clients’ attack surfaces, ensuring that legitimately high-risk issues do come to light. By leveraging the expertise of Praetorian’s security engineers and applying client-specific context, Chariot enhances the signal-to-noise ratio, allowing organizations to focus their resources on addressing the most significant threats with confidence and precision.
Choosing Praetorian’s managed service means opting for an agile, responsive, and proactive approach to your cybersecurity needs. It means embracing a solution that is always ready and equipped to face the ever-changing landscape, maintained by expert offensive security engineers. Chariot Managed Service cuts out the noise while still providing you insight to the continuous process of ensuring your security posture is as robust and responsive as possible.