Screenshotting: Can You See What I See?
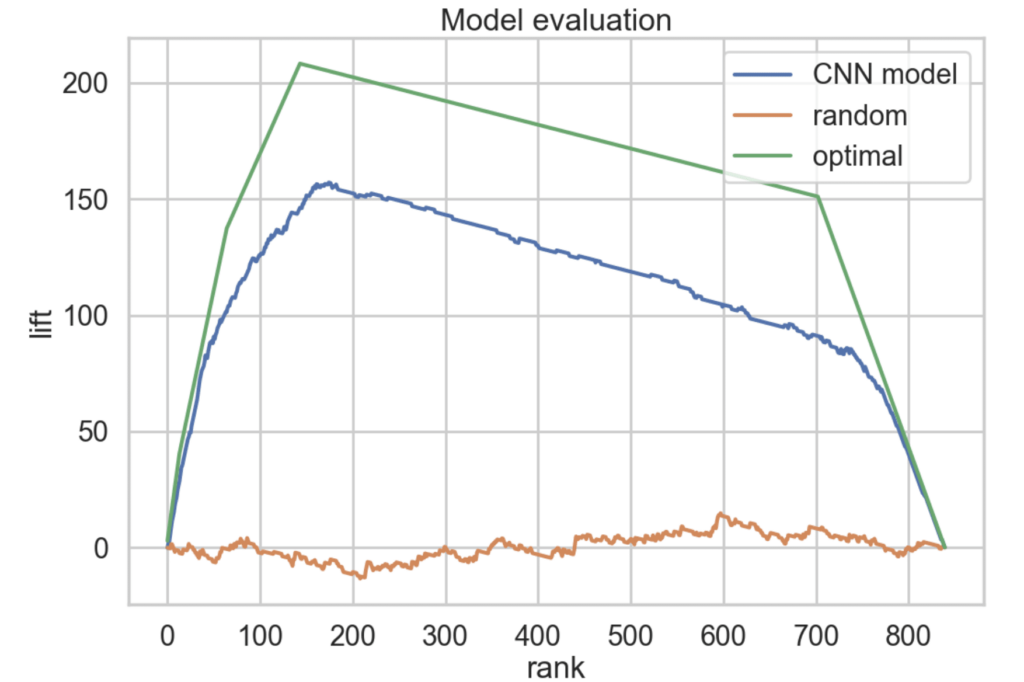
At Praetorian, we firmly believe that the most effective way to secure your systems is to look at them through an offensive lens. After all, when you view yourself the same way an attacker does, you get a better understanding of which defenses are likely to be effective. When building Chariot, our External Attack Surface […]
Dynamic Linking Injection and LOLBAS Fun
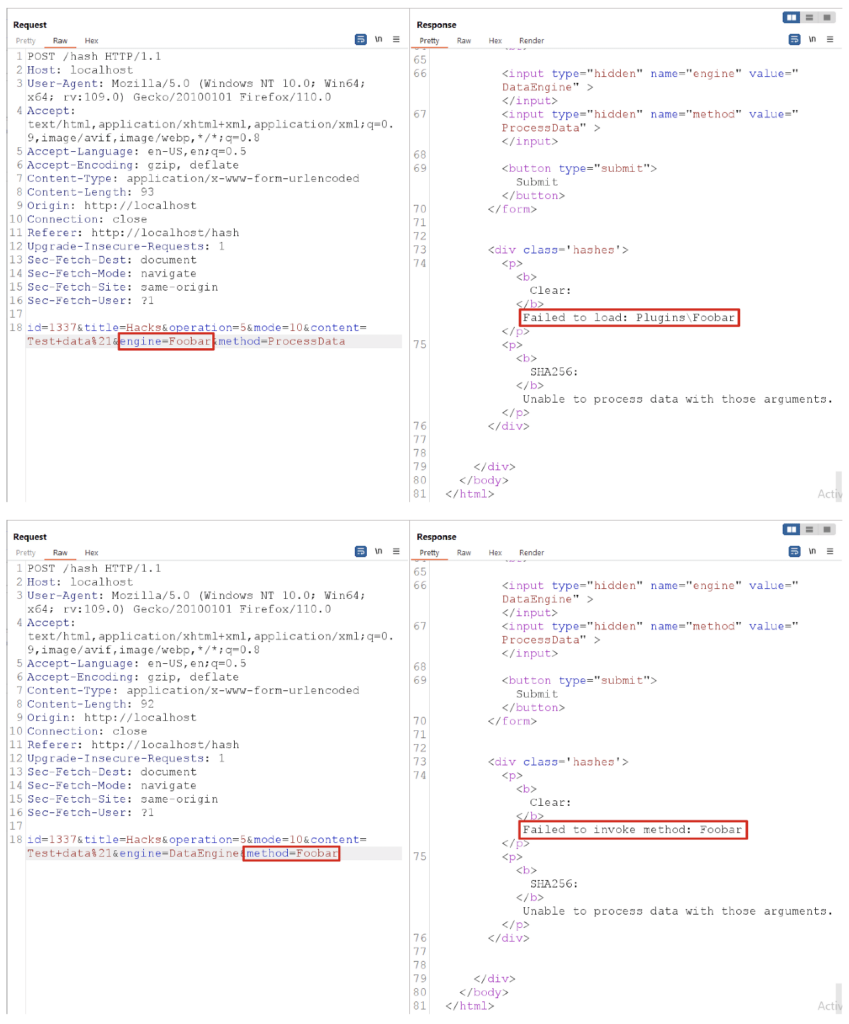
Introduction LoadLibrary and LoadLibraryEx are how Windows applications load shared libraries at runtime. Praetorian recently tested a .NET web application that unsafely passed user input into LoadLibrary. In this article, we discuss this vulnerability class, dubbed dynamic-linking injection. We begin with an explanation of the vulnerability. We then walk through a simple recreation of the […]
Find More Secrets with Nosey Parker v.0.12.0

On March 2, 2023, we issued some updates to our secrets sniffing tool, Nosey Parker, which has been available as an Apache 2-licensed open-source project since December 2022. We originally developed the full version to embed in Chariot, our Attack Surface Management solution, because we needed a secrets detection tool that was as fast as […]
Bypassing Akamai’s Web Application Firewall Using an Injected Content-Encoding Header
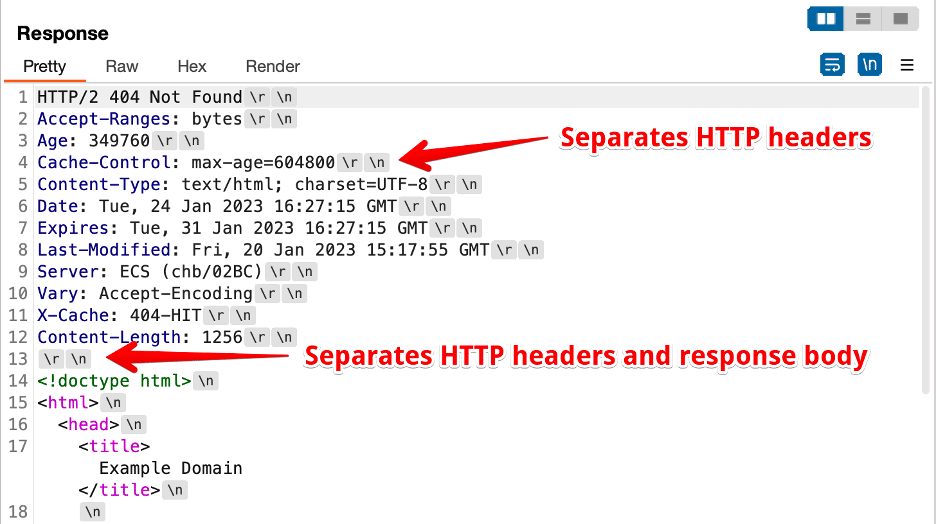
During a recent Chariot customer pilot we identified an interesting method to bypass the cross-site scripting (XSS) filtering functionality within the Akamai Web Application Firewall (WAF) solution. Chariot had identified a Carriage Return and Line Feed (CRLF) injection vulnerability during an automated scan, and we discovered the bypass during our exploitation phase. In this article, […]
Technical Advisory – Azure B2C – Crypto Misuse and Account Compromise
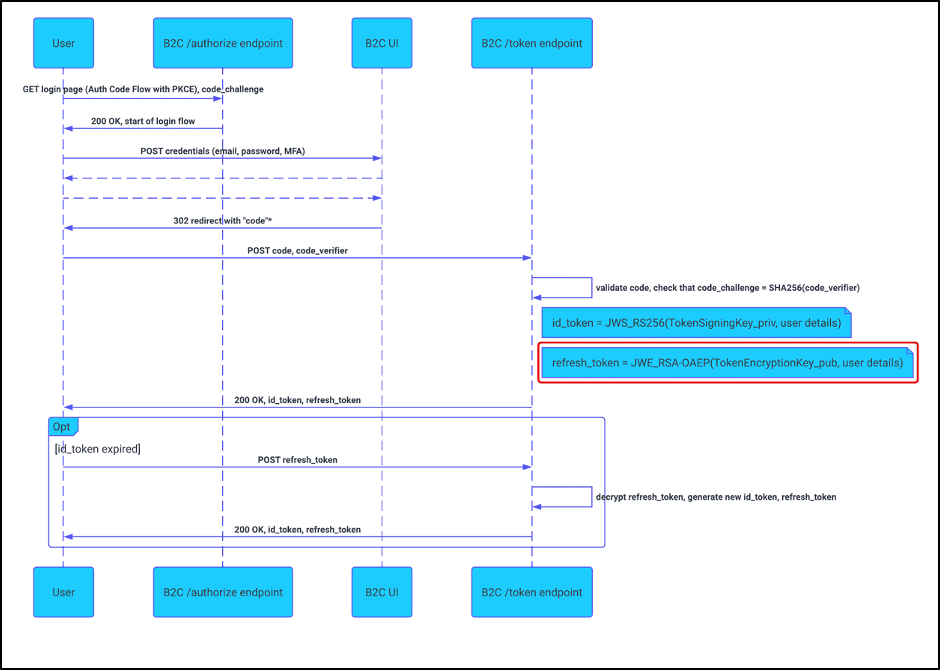
Microsoft’s Azure Active Directory B2C service contained a cryptographic flaw which allowed an attacker to craft an OAuth refresh token with the contents for any user account. An attacker could redeem this refresh token for a session token, thereby gaining access to a victim account as if the attacker had logged in through a legitimate […]
ASM: The Best Defense is a Good Offense
About 10 years ago, security was relatively simple because everything occurred on premises. Change releases were tightly controlled by a change ticket and review process. In contrast, current networks consist of auto-scaling containers that run in Kubernetes clusters and even serverless clusters like AWS Lambda. We have transitioned from constrained environments that humans closely scrutinized […]
Open Source Tools: From Our Lab to Your Fingertips
One of the core decisions we’ve made at Praetorian is to maximize efficiency and effectiveness. In pursuit of this, we carefully select and implement automation and technical solutions for tasks that don’t need human attention. The key is choosing thoughtfully developed tech and tools; when we can’t find what we need, we create it ourselves! […]
Phantom of the Pipeline: Abusing Self-Hosted CI/CD Runners

Introduction Throughout numerous Red Teams in 2022, a common theme of Source Control Supply Chain attacks in GitHub repositories has emerged. After many hours manually hunting for and exploiting these attack paths, we’ve built an all-in-one toolkit called Gato (Github Attack Toolkit) for finding and attacking repositories where these misconfigurations are present. We released the […]
ABAC in Lambda
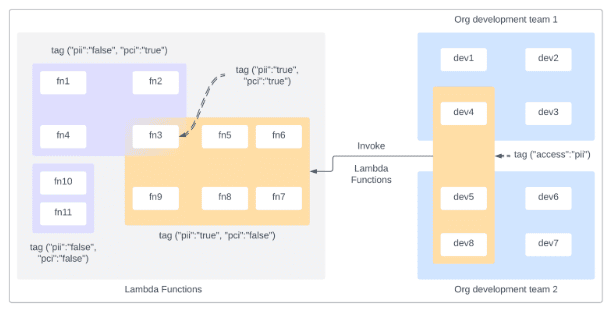
During August 2022 we published a blog discussing AWS Security Trends of 2022 , one of which was ABAC in Lambda. AWS allows administrators to use tags to designate attributes for both IAM and AWS resources. Attribute Based Access Control, or ABAC, is a strategy to allow permissions assignment based on the value of such […]
Doing the Work: How to Architect a Systematic Security Program, Part 3

Building a security program from the ground up is a complicated, complex undertaking that can pay massive dividends down the road. We firmly believe that “the devil is in the details,” in that the more thought an organization invests in organizing their framework (see Part 1 of this series) and planning how to measure against […]