Understanding the Recent Confluence Vulnerability (CVE-2023-22515) and Digging into Atlassian Bamboo

Overview Recently, Rapid7 disclosed a vulnerability within Confluence that allowed a remote unauthenticated attacker to create a new administrative user account by bypassing the XWork SafeParameterFilter functionality. Our vulnerability research team decided to take a look at another Atlassian product, Atlassian Bamboo, to determine if a similar vulnerability existed within that application. In this post, […]
Technical Advisory: Vulnerabilities Identified within ListServ

Overview In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities that are likely to impact the security of leading organizations. Our ultimate goal when performing our research is to identify unauthenticated remote code execution vulnerabilities which could be reliably exploited across a wide variety of […]
DoubleQlik: Bypassing the Fix for CVE-2023-41265 to Achieve Unauthenticated Remote Code Execution
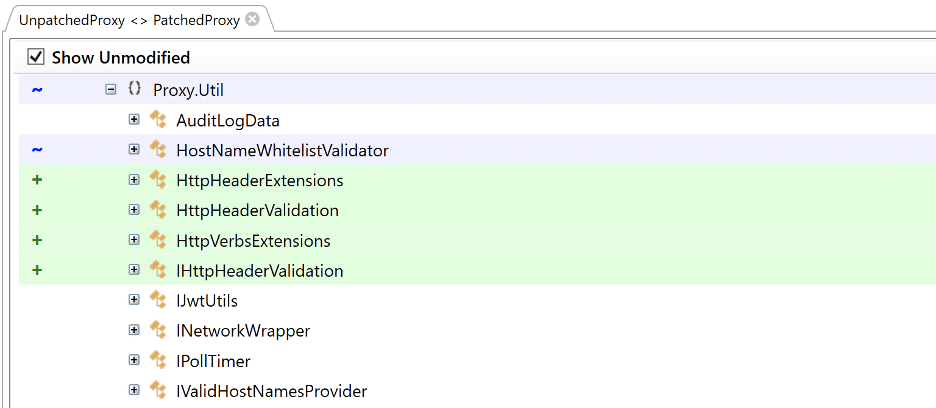
Overview On August 29th, 2023, Qlik issued a patch for two vulnerabilities we identified in Qlik Sense Enterprise, CVE-2023-41265 and CVE-2023-41266. These vulnerabilities allowed for unauthenticated remote code execution via path traversal and HTTP request tunneling. As part of our standard operating procedure, we performed a diff of the issued patch to identify potential bypasses […]
Advisory: Qlik Original Fix for CVE 2023-41265 Vulnerable to RCE
Overview On August 29th, 2023 Qlik issued a patch for two vulnerabilities we identified in Qlik Sense Enterprise, CVE-2023-41265 and CVE-2023-41266. These vulnerabilities allowed for unauthenticated remote code execution via path traversal and HTTP request tunneling. As part of our standard operating procedure, we performed a diff of the issued patch to identify potential bypasses […]
Back to the 90s: Fujitsu “IP series” Real-time Video Transmission Gear Hard Coded Credentials
Overview In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities that are likely to impact the security of leading organizations. Exposed embedded devices are a particular area of concern because they typically do not have host-based security controls such as EDR or Antivirus, but still […]
ZeroQlik: Achieving Unauthenticated Remote Code Execution via HTTP Request Tunneling and Path Traversal
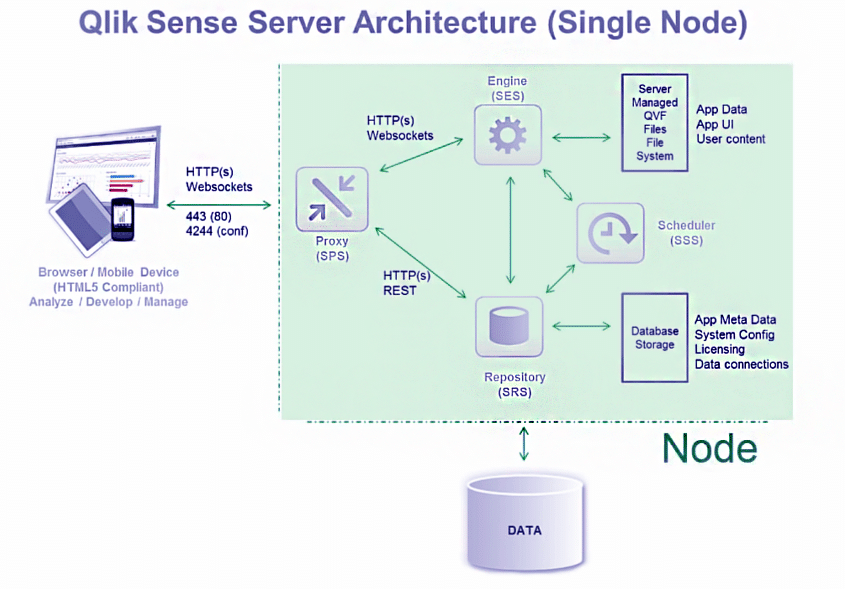
Overview In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities that are likely to impact the security of leading organizations. Recently, we decided to take a look at Qlik Sense Enterprise, a data analytics solution similar to Tableau. The recent exploitation of vulnerabilities in the […]
Advisory: Qlik Sense Enterprise for Windows Remote Code Execution Vulnerabilities
Advisory: Qlik Sense Enterprise Remote Code Execution In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities in applications that are likely to impact the security of leading organizations. Recently, we discovered two vulnerabilities which can be chained together to achieve unauthenticated remote code execution on […]
MOVEit! An Overview of CVE-2023-34362
On May 31st, 2023, Progress disclosed a serious vulnerability in its MOVEit Transfer software. The vulnerability is remotely exploitable, does not require authentication, and impacts versions of the software that are 2023.0.1 (15.0.1) or earlier. We are aware of multiple reports of active exploitation of this vulnerability in the wild, and attackers are already mobilizing […]
Dynamic Linking Injection and LOLBAS Fun
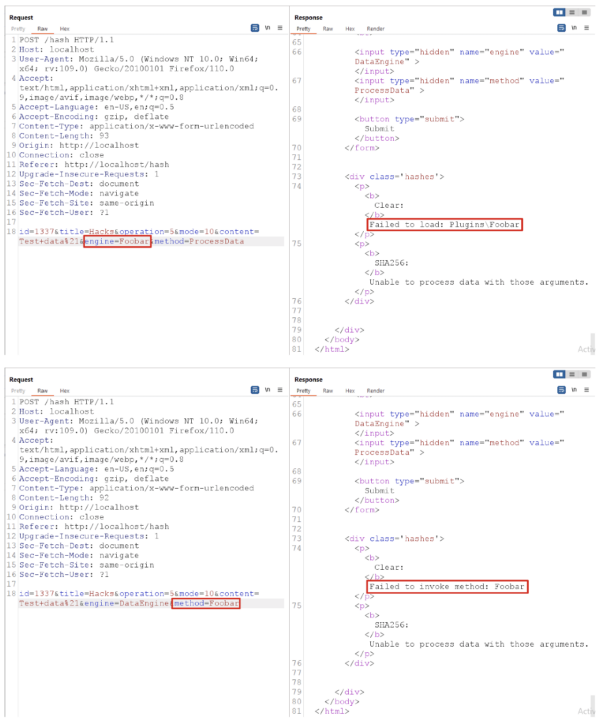
Introduction LoadLibrary and LoadLibraryEx are how Windows applications load shared libraries at runtime. Praetorian recently tested a .NET web application that unsafely passed user input into LoadLibrary. In this article, we discuss this vulnerability class, dubbed dynamic-linking injection. We begin with an explanation of the vulnerability. We then walk through a simple recreation of the […]
Web3 Trust Dependencies: A Closer Look at Development Frameworks & Tools
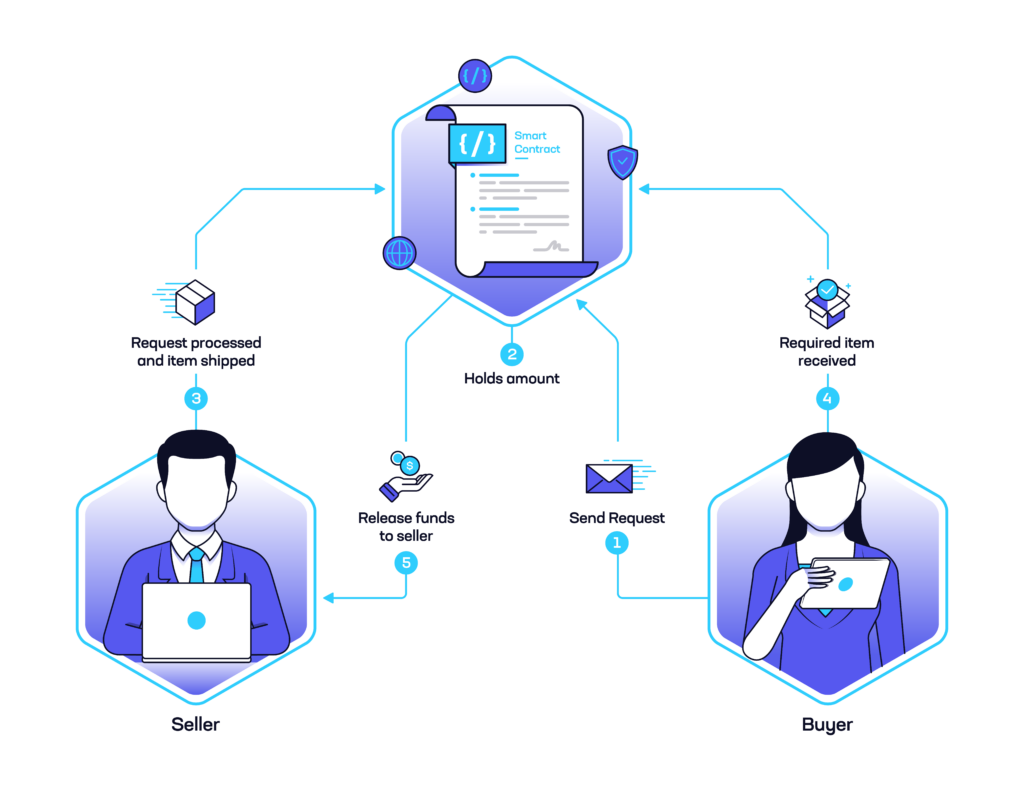
In the world of headline-grabbing smart contract exploits, developers and other stakeholders often skew their security attention in one direction; namely, they tend to focus on on-chain code, yet often neglect framework security. When writing smart contracts, this oversight can have significant negative security implications. Insecure frameworks or languages can subtly introduce vulnerabilities when compiling […]