ASM: The Best Defense is a Good Offense
About 10 years ago, security was relatively simple because everything occurred on premises. Change releases were tightly controlled by a change ticket and review process. In contrast, current networks consist of auto-scaling containers that run in Kubernetes clusters and even serverless clusters like AWS Lambda. We have transitioned from constrained environments that humans closely scrutinized […]
Doing the Work: How to Architect a Systematic Security Program, Part 3

Building a security program from the ground up is a complicated, complex undertaking that can pay massive dividends down the road. We firmly believe that “the devil is in the details,” in that the more thought an organization invests in organizing their framework (see Part 1 of this series) and planning how to measure against […]
Framework Selection: How to Architect a Systematic Security Program – Part 1
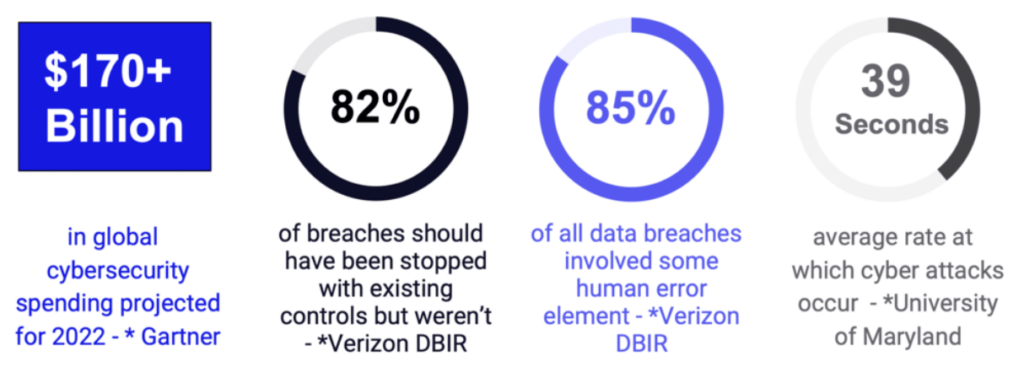
A need for public trust in information systems has driven continuous technological advances and new regulatory requirements, which have in turn made the global cyber threat landscape more complex and connected (see figure 1). As Boards of Directors, regulators, and the public become more aware of this interplay, organizations will need to evolve to address […]
Part 3 – Trends in the Cybersecurity Talent Marketplace in the Face of Sustained Shortages
I’ve written previously about how I believe a team’s expertise and talent are the most important factors in determining the success of a cybersecurity program. I’d like to elaborate a bit more on how I think that is affecting the marketplace for cybersecurity expertise and what it means for people operations. To summarize my previous […]
Part 2 – Adapting Security Strategy to the Rise of Opportunistic Attacks
Over the past two years, we’ve seen a number of our clients’ security programs re-orient to prepare for potential ransomware incidents. Much of these preparations have focused on the controls and processes that would specifically help prevent and respond to a ransomware infection. While this is often effort well-spent, I’d like to suggest that many […]
Part I – CyberSecurity is Adversarial, and What that Means for Security Strategy
I have an impression that in the course of the day to day grind, many security leaders have lost sight of a core tenant of cybersecurity: that it is adversarial. Ultimately, the core of most cybersecurity risks is defenders trying to stop attackers. Both sides are seeking to outwit each other. This contest is mediated […]