Doing the Work: How to Architect a Systematic Security Program, Part 3

Building a security program from the ground up is a complicated, complex undertaking that can pay massive dividends down the road. We firmly believe that “the devil is in the details,” in that the more thought an organization invests in organizing their framework (see Part 1 of this series) and planning how to measure against […]
Web3 Trust Dependencies: A Closer Look at Development Frameworks & Tools
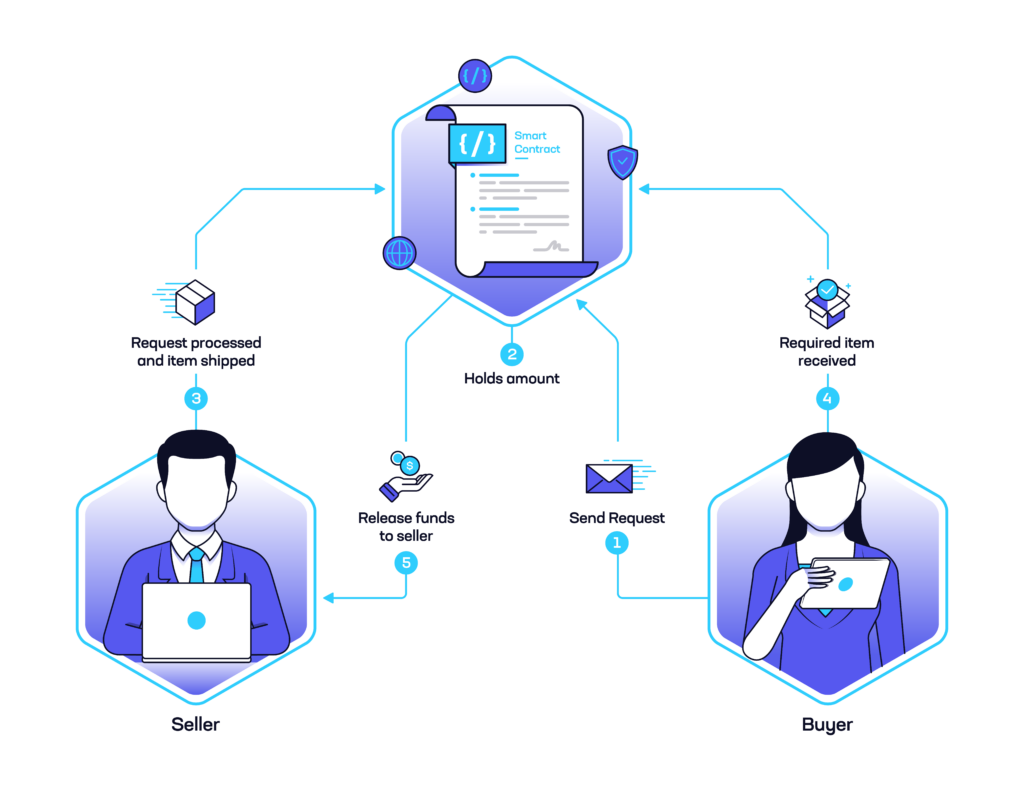
In the world of headline-grabbing smart contract exploits, developers and other stakeholders often skew their security attention in one direction; namely, they tend to focus on on-chain code, yet often neglect framework security. When writing smart contracts, this oversight can have significant negative security implications. Insecure frameworks or languages can subtly introduce vulnerabilities when compiling […]
Measuring Up: How to Architect a Systematic Security Program – Part 2
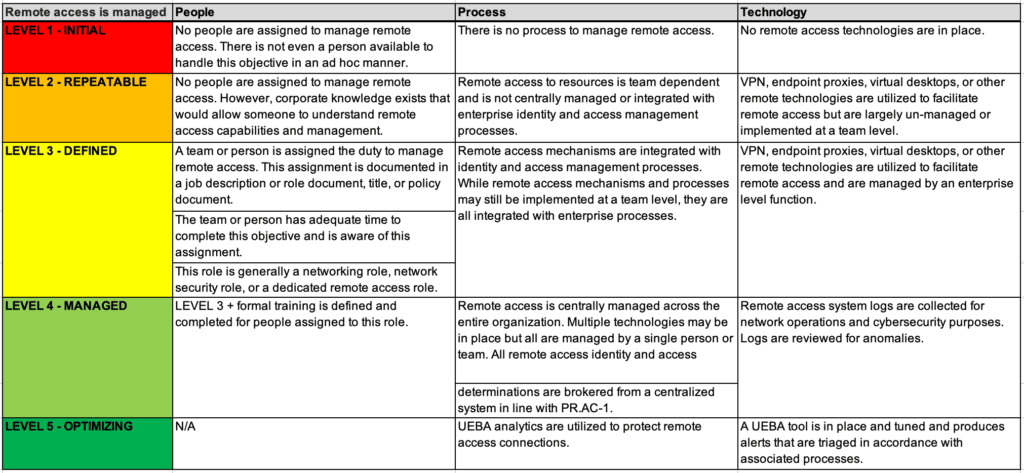
In Part 1 of this series , we discussed how organizations can go about selecting a framework for implementation. In order to effectively measure your organization against the selected framework, the organization must take five crucial steps before doing any assessment or analysis. Define the rating scale Define the rating criteria Determine how to address […]
Framework Selection: How to Architect a Systematic Security Program – Part 1
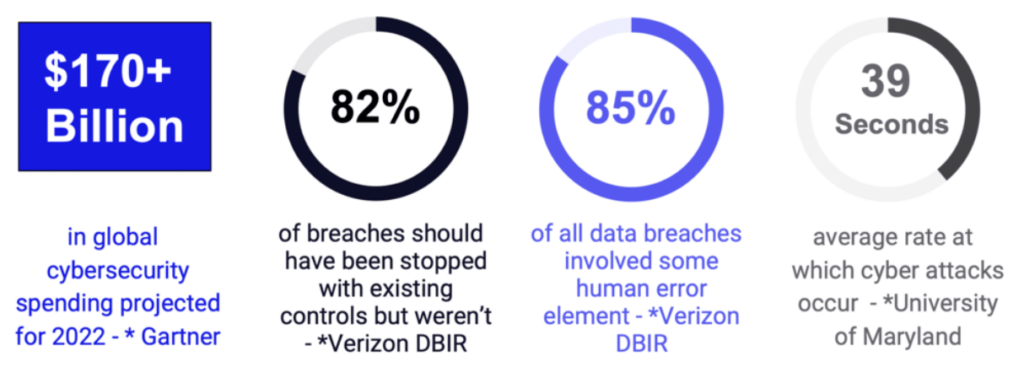
A need for public trust in information systems has driven continuous technological advances and new regulatory requirements, which have in turn made the global cyber threat landscape more complex and connected (see figure 1). As Boards of Directors, regulators, and the public become more aware of this interplay, organizations will need to evolve to address […]