TLDR: We are releasing Vulcan, a tool to make it easy and fast to test various forms of injection. All of the techniques included are already public. Vulcan brings them together in a single tool to test endpoint detection and response (EDR) coverage so that you can quickly identify detection gaps. This tool can be used as a test-harness to identify gaps so that efforts can be focused on detecting holes.
What is Purple Teaming? Purple Teaming is the process by which our team will measure detection coverage within an environment mapped to MITRE ATT&CK.
Download Code: https://github.com/praetorian-code/vulcan
When working with clients to test detection coverage, Praetorian uses benign payloads. This is critical to ensure detection control alerts are behavior-based and NOT specific to signatures. Detection strategies based solely on payload specific usage are incomplete since the behaviors in MITRE ATT&CK are what defenders should be measuring themselves against. Attackers can evade signature-based detection by recompiling a payload or making other superficial changes, but evading behavioral detection requires the attacker to change their underlying methodology. Therefore, detection coverage mappings need to be payload agnostic. It’s great to know a product can detect Metasploit or Cobaltstrike, but what value does that provide when real attackers uses their own custom malware?
Two common behaviors clients are often curious about are Process Injection and Process Hollowing, which are a set of techniques and methods to bootstrap execution on a target by inserting code into a specific process. For example, Process Hollowing includes creating a process in a suspended state, adding code to the process, and then resuming it to spawn the execution of the code. Additionally, there are many different Process Injection techniques to inject code into a running process, which can be shellcode, a DLL, or both.
Praetorian invests significant time and research into choosing tools that maximize the effectiveness of our testing coverage. One of the more popular tools we found for injection testing is called injectAllTheThngs, which supports 7 different injection techniques. However, we found it didn’t completely suit our needs as it doesn’t support shellcode injection and has not been updated since July 2017.
We thought it would be useful to expand our toolset to include more techniques, support shellcode and DLL injection within a single tool, and make it easy to automate.
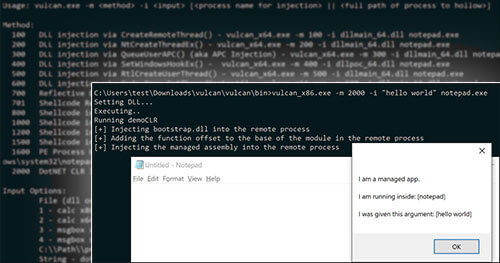
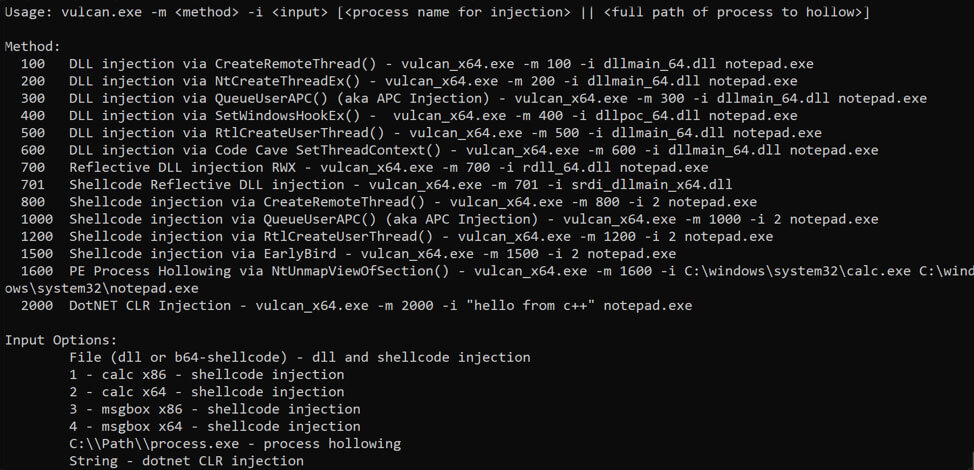
Therefore, we built Vulcan to address these issues. It’s designed to support both DLL and shellcode injection in a manner that is easy to use and automate. Basic usage is shown below which include examples for all supported methods.
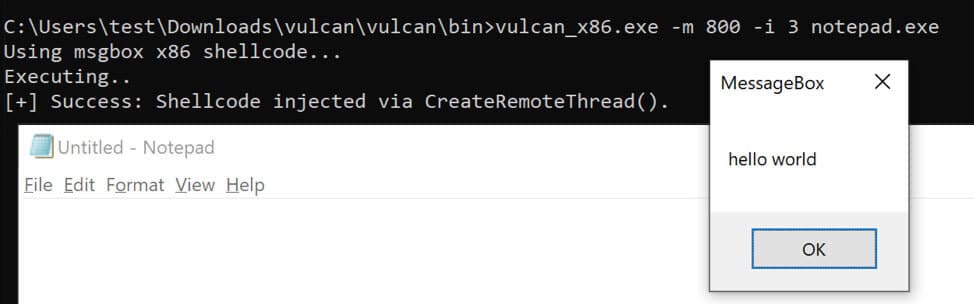
The tool includes shellcode for running the calculator and creating message-box pop-ups. Below is an example of using the message-box popup with CreateRemoteThread().
We can replace the shellcode in the tool if desired. The example below uses msfvenom from Metasploit, but Vulcan supports any self-loading position-independent shellcode.
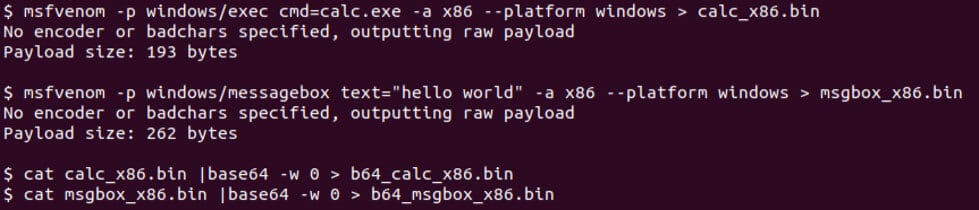
Vulcan also supports using a Base64-encoded shellcode file as an input.
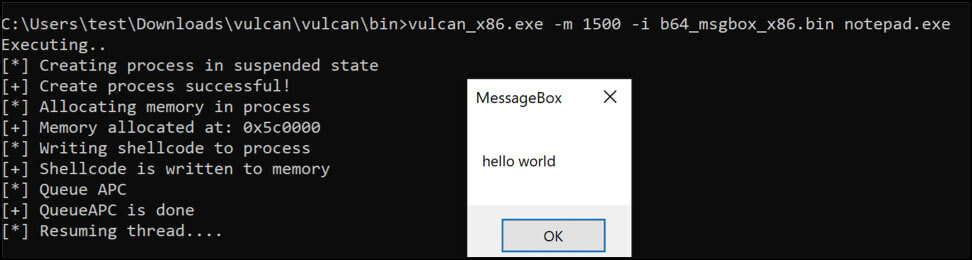
We added the ability to inject C# code into any process.
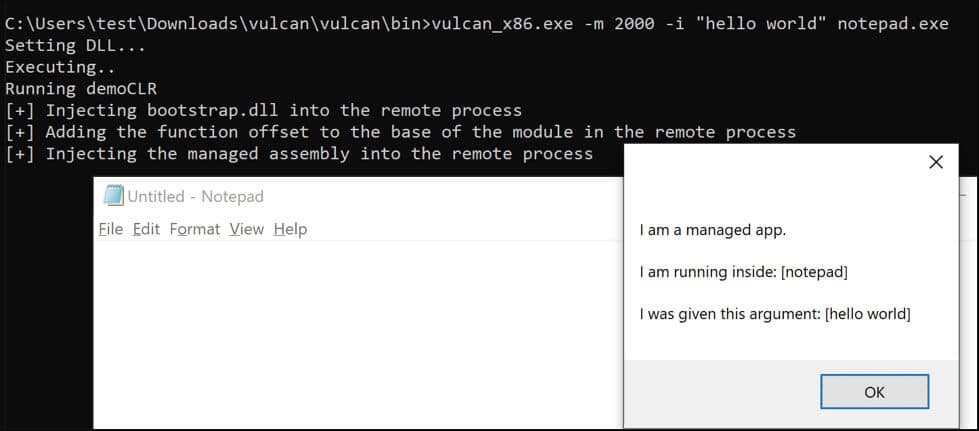
We hope this helps you improve and test your detection controls.
Enjoy!
Download Code: https://github.com/praetorian-code/vulcan
References
- https://attack.mitre.org/techniques/T1055/
- https://attack.mitre.org/techniques/T1093
- https://github.com/fdiskyou/injectAllTheThings