At Praetorian, we’re constantly exploring how emerging technologies can strengthen security programs. Today, we’re sharing insights from our work building AI-powered vulnerability discovery capabilities within Praetorian Guard — finding critical security issues across the open-source ecosystem before they become public exploits.
Using a multi-stage AI pipeline — automated discovery, validation, and exploit verification — we’ve identified high-severity vulnerabilities across widely used projects including OpenClaw, Node.js, React, and Deno. This post explains how the technology works, shares real findings with confirmed CVEs, and explores what AI-driven vulnerability discovery means for your software supply chain.
The Challenge: Security Can't Keep Pace with Development
Modern software evolves rapidly. Open-source projects ship thousands of code changes daily, each potentially introducing security vulnerabilities. Security teams face an impossible task: manually reviewing every change while attackers only need to find one exploitable flaw.
Traditional security tools haven’t solved this problem:
- Static analyzers generate overwhelming false positives that waste researcher time
- Manual code review doesn’t scale to modern development velocity
- Existing automation lacks the contextual understanding to catch sophisticated vulnerabilities
The gap between development speed and security validation continues to widen. According to the 2024 Synopsys Open Source Security and Risk Analysis (OSSRA) report, 96% of commercial codebases contain open-source components, and 84% contain at least one known vulnerability. The National Vulnerability Database (NVD) processed over 28,000 new CVEs in 2023 alone — a volume that no manual process can keep pace with.
A Different Approach: AI That Thinks Like a Security Researcher
We developed our AI-powered platform to approach vulnerability discovery the way expert security researchers do — but at machine scale. Rather than relying on pattern matching or known signatures, the system uses advanced AI models to understand code semantically, reason about security implications, and validate findings through automated testing.
How It Works
Our platform operates through an intelligent, multi-stage pipeline:
Stage 1 — Discovery: The system analyzes code changes between software versions, focusing specifically on security-relevant modifications while filtering out benign changes like documentation updates or formatting.
Stage 2 — Validation: Potential vulnerabilities undergo rigorous automated verification. The AI traces data flows, evaluates exploitability conditions, and eliminates false positives through contextual reasoning — dramatically reducing noise before human review.
Stage 3 — Verification: Findings are tested through automated exploit development. The system generates working proof-of-concepts to confirm real-world impact, ensuring researchers receive validated vulnerabilities — not theoretical possibilities.
This end-to-end automation transforms weeks of manual work into hours of machine analysis.
How Accurate Is AI-Powered Vulnerability Detection?
Before deploying our platform broadly, we conducted extensive benchmarking to optimize detection accuracy. We evaluated different AI model configurations against known vulnerabilities, measuring how reliably each approach identified real security issues.
The benchmarking revealed several key insights:
Hybrid architectures work best: Combining fast initial triage with deep analysis on promising findings achieves better results than either approach alone.
Context matters: The more code context the AI can analyze together, the better it performs at identifying complex vulnerability chains.
Balance is critical: Pure accuracy isn’t enough — detection speed and cost efficiency matter for practical, continuous deployment.
Our optimal configuration achieved 70% detection accuracy against a benchmark set of known vulnerabilities. While not perfect, this significantly outperforms traditional static analysis tools while providing much richer context about exploitability and impact.
Real-World Impact: From Theory to Practice
We’ve deployed our platform across dozens of open-source projects, discovering security vulnerabilities that span multiple severity levels and vulnerability classes.
Findings in OpenClaw
As part of our continuous monitoring of the open-source ecosystem, we analyzed OpenClaw, an increasingly popular AI agent framework. Our platform identified several high-severity issues:
Authentication Bypass in Browser Control (GHSA-h9g4-589h-68xv)
- Severity: High (CVSS 7.1)
- Impact: Missing authentication allowed local attackers to control browser sessions and exfiltrate credentials.
- Patched: Version 2026.2.14
Path Traversal in Browser Control API (GHSA-gq9c-wg68-gwj2)
- Severity: High (CVSS 7.5)
- Impact: User-supplied paths in browser trace/download endpoints allowed arbitrary file writes outside intended directories.
- Patched: Version 2026.2.13
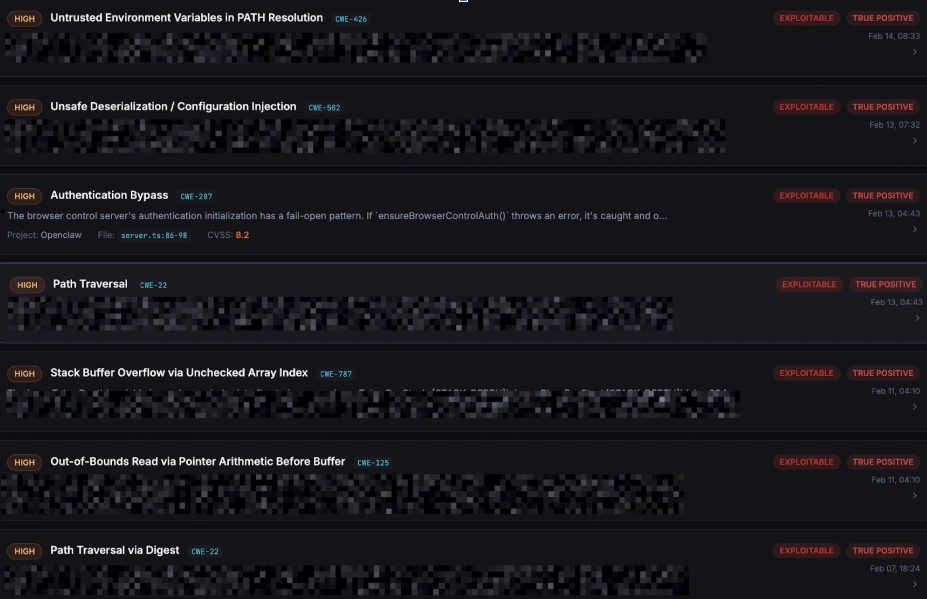
Broader Discoveries: Material Risk Across the Ecosystem
These represent initial examples from a much broader discovery effort. Our platform has identified vulnerabilities across widely used projects including Node.js, React, Deno, and others in the JavaScript, Python, and Rust ecosystems. Many of these findings are currently under coordinated disclosure with project maintainers.
The vulnerabilities we’ve discovered span multiple high-severity categories, representing significant material risk to organizations relying on these open-source components. While not exhaustive, notable examples include:
Authentication and Authorization Bypasses: Multiple projects contained flaws allowing attackers to circumvent access controls, potentially exposing sensitive data or administrative functions. These issues are particularly critical in frameworks and platforms where security boundaries are fundamental to their architecture.
Remote Code Execution: Several findings enable attackers to execute arbitrary code on affected systems — the highest severity class of vulnerability. RCE vulnerabilities in widely deployed infrastructure components put thousands of downstream organizations at immediate risk.
Path Traversal and Arbitrary File Operations: Discovered flaws allowing attackers to read, write, or delete files outside intended directories. In cloud and containerized environments, these vulnerabilities can lead to container escape, credential theft, and lateral movement across infrastructure.
Server-Side Request Forgery (SSRF): Identified multiple SSRF vulnerabilities that could be leveraged to bypass network segmentation, access internal services, and exfiltrate sensitive data from cloud metadata endpoints.
Command Injection: Found injection points allowing attackers to execute system commands, often leading to full system compromise. These are particularly dangerous in CI/CD pipelines and automated build systems.
The common thread: these aren’t theoretical vulnerabilities requiring complex exploit chains. They’re straightforward, high-impact flaws that attackers actively seek out. Organizations using affected versions are exposed to real risk until patches are deployed.
All findings have been responsibly disclosed to project maintainers through coordinated disclosure processes, with patches available or in development.
Why Does This Matter for Your Organization?
- Scale: Continuous monitoring of dozens of projects simultaneously, keeping pace with development velocity that no manual process can match.
- Quality: Automated verification eliminates false-positive noise, delivering validated findings with working proof-of-concept exploits — ready for disclosure or remediation.
- Proactive defense: Organizations can identify vulnerabilities in their dependencies before they become public CVEs and active attack vectors.
- Supply chain visibility: With 96% of codebases depending on open source, knowing what’s vulnerable in your dependency tree is no longer optional — it’s a security requirement.
Looking Forward: AI-Augmented Security Research
This work demonstrates that AI can handle sophisticated security analysis tasks that previously required expert human researchers. However, AI augments rather than replaces human expertise — researchers remain essential for disclosure coordination, patch validation, and strategic security guidance.
As AI capabilities continue to advance, we expect detection accuracy to improve beyond the current 70% benchmark. But even today, this technology is already transforming how we approach security research at scale.
Part of Praetorian Guard
Our AI-powered vulnerability discovery platform is one capability within Praetorian Guard, our comprehensive security platform. By combining AI-powered vulnerability discovery with traditional penetration testing, continuous monitoring, and threat intelligence, we help organizations maintain security at software development speed.
Whether you’re concerned about vulnerabilities in your software supply chain, need continuous security validation for your applications, or want proactive monitoring of your open-source dependencies — Praetorian Guard provides the tools and expertise to protect your organization.
Note: Many findings referenced in this post are currently under coordinated disclosure. Additional details will be shared as patches become available.
Frequently Asked Questions
What is Praetorian Guard’s AI vulnerability discovery platform?
It’s an AI-powered system that automatically analyzes open-source software for security vulnerabilities. It uses a three-stage pipeline — discovery, validation, and verification — to find, confirm, and generate proof-of-concept exploits for real vulnerabilities at machine scale.
How is this different from traditional static analysis (SAST)?
Traditional SAST tools rely on pattern matching and known signatures, producing high false-positive rates. Our AI understands code semantically, reasons about exploitability, and validates findings with working proof-of-concepts — achieving 70% detection accuracy with significantly lower false positives.
What programming languages and ecosystems are supported?
The platform currently analyzes projects across the JavaScript, Python, and Rust ecosystems, including widely used projects like Node.js, React, Deno, and OpenClaw. Language support continues to expand.
Does the platform replace human security researchers?
No. AI augments human expertise by handling volume and velocity challenges. Human researchers remain essential for coordinated disclosure, patch validation, strategic security guidance, and handling findings that require nuanced judgment.
How are vulnerabilities disclosed?
All findings go through coordinated disclosure with project maintainers. We follow responsible disclosure practices, giving maintainers time to develop and release patches before details are published. GHSAs are filed for confirmed vulnerabilities.
References
- GHSA-h9g4-589h-68xv — OpenClaw Authentication Bypass — https://github.com/advisories/GHSA-h9g4-589h-68xv
- GHSA-gq9c-wg68-gwj2 — OpenClaw Path Traversal — https://github.com/advisories/GHSA-gq9c-wg68-gwj2
- Synopsys 2024 Open Source Security and Risk Analysis Report — https://www.synopsys.com/software-integrity/resources/analyst-reports/open-source-security-risk-analysis.html
- National Vulnerability Database (NVD) — https://nvd.nist.gov/
- Praetorian Guard — Comprehensive Security Platform — https://www.praetorian.com/
- MITRE CVE Program — https://cve.mitre.org/
- Contact Praetorian — https://www.praetorian.com/contact/