With the recent high-profile attacks on Sony and Anthem, it’s clear that cyber risks continue to grow and that organizations need to do more to strengthen their cybersecurity defenses.
Security frameworks exist to guide the implementation and management of security controls, and they should be used by any organization looking to intelligently manage cyber risk. A security framework helps prevent a haphazard approach to information security, and reduces potential gaps in the organization’s security efforts.
The ideal framework provides a complete guide to current information security best practices while leaving room for an organization to customize its implementation of controls to its unique needs and risk profile. Several existing and well-known cybersecurity frameworks include COBIT 5, ISO 27000, and NIST 800-53. Recently, a new framework has come into play: NIST’s “Framework for Improving Critical Infrastructure Cybersecurity.”
NIST Cybersecurity Framework Overview
The Cybersecurity Framework was created in response to Executive Order 13636, which aims to improve the security of the nation’s critical infrastructure from cyber attacks. While directed to “critical infrastructure” organizations, the Framework is a useful guide to any organization looking to improve their cyber security posture.
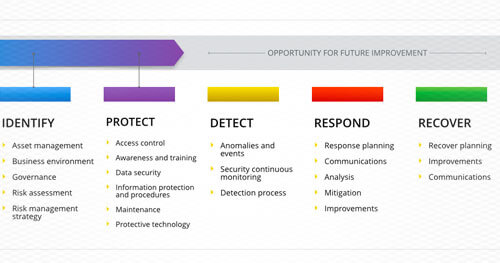
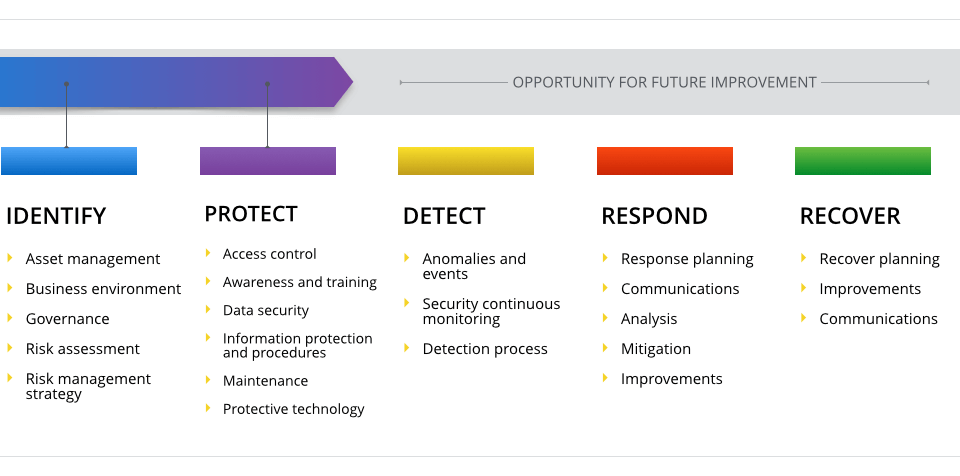
The document is divided into the framework core, the implementation tiers, and the framework profile. The framework core describes 5 functions of an information security program: identify, protect, detect, respond, and recover. The Framework references other documents like NIST 800-53 and COBIT 5 for specific controls and processes needed to implement these functions.
CYBERSECURITY FRAMEWORK CORE
The Framework defines four implementation tiers: partial, risk-informed, repeatable, and adaptive. These tiers are meant for self-analysis by the organization and allow tailored implementation of the framework to their risk tolerance and resources.
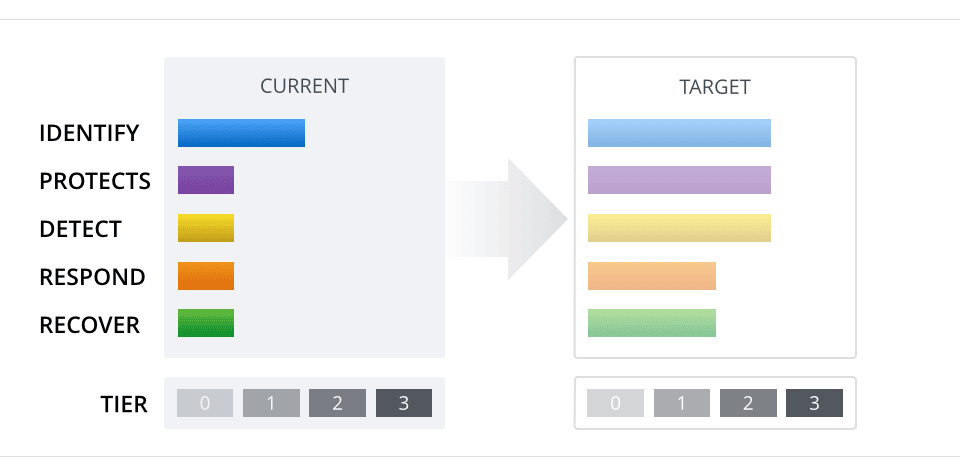
Finally, the Framework recommends creating a current state and target state profile based on the analysis of the organization’s alignment with the Framework core. These profiles will guide the organization’s efforts to improve its cyber security posture.
CYBERSECURITY FRAMEWORK PROFILE AND TARGET
Are you ready to adopt a cybersecurity framework? The security experts at Praetorian can help your organization better determine current and target security profiles and work with your team to develop a roadmap for modeling your cybersecurity maturity over time.
Learn more about our NIST Cybersecurity Framework Benchmark services.
Differences from NIST 800-53 and Other Frameworks
While the Framework was written primarily by NIST, the same organization behind 800-53, there are several differences between them. The Framework is concise, voluntary in nature and builds on existing frameworks.
The Framework is more high-level in its scope compared to existing frameworks like NIST 800-53. It focuses on how to access and prioritize security functions, and references existing documents like NIST 800-53, COBIT 5, and ISO 27000 for more detail on how to implement specific controls and processes. This allows the Framework to be a much more concise document at 40 pages as opposed to NIST 800-53’s 460 pages.
Due to its high-level scope and clear language, the Framework is also more suitable for reading by executives of an organization who may not have a technical background. The Framework could be more useful to achieve the buy-in of C-level executives necessary for the success of a cyber-security initiative.
NIST 800-53 is a regulatory document, encompassing the processes and controls needed for a government-affiliated entity to comply with the FIPS 200 certification. In contrast, the Framework is voluntary for organizations and therefore allows more flexibility in its implementation.
The Framework builds on and does not replace security standards like NIST 800-53 or ISO 27001. It’s a great starting point for organizations looking to improve their cyber security.
Final Thoughts
The Cybersecurity Framework was created with the realization that specific controls and processes have already been covered and duplicated in existing frameworks, and that organizations needed high-level guidance for improving their cyber security defenses. This makes the Framework well suited for any organization worried about ever evolving cyber threats.
Security specialists like Praetorian can help such organizations better determine their current and target security profiles by leveraging our expertise in cyber-security assessment.