NIST Cybersecurity Framework Vignettes: Backups
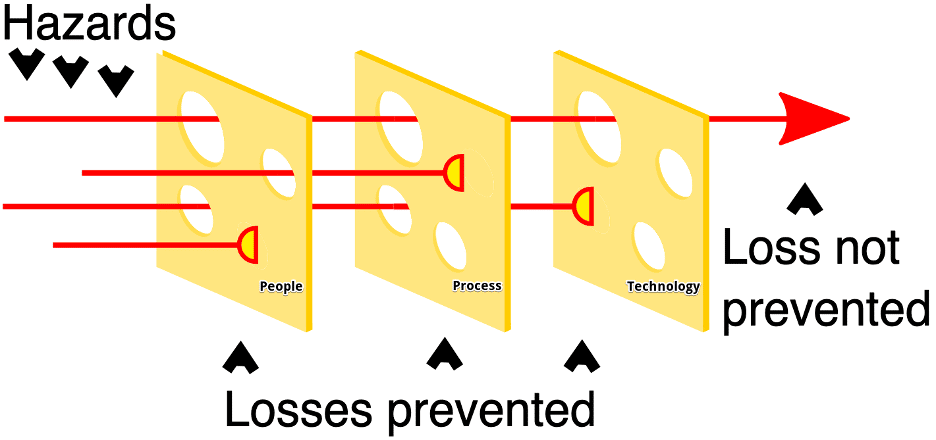
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) Vignettes series focuses on findings from recent security assessments that highlight the importance of different NIST CSF objectives. The NIST CSF provides a comprehensive framework for complex organizations to close gaps and add layers to the “Swiss Cheese Model.” The series seeks to demonstrate how the correct application of NIST CSF can prioritize and mitigate real risks to your organization. In our first post of the series, we examine how organizations apply resources to better combat phishing. In our second post, we explored how CSF objectives can help to defend against broadcast name resolution poisoning (BNRP). In this article, we discuss how NIST CSF can be applied to organizational backup strategies to defend against data loss, manipulation, and destruction.
Discovery
During a recent internal penetration test, a Praetorian engineer discovered virtual machine snapshots hosted on an unprotected file share. The share included snapshots from the organization’s domain controllers and the snapshots were not encrypted.
Using open source tools, our engineer was able to mount the snapshot’s hard drive and retrieve the ntds.dit file from the snapshots. This file, often considered one of the most critical files in the entire domain, contains all the users and password hashes for the domain. With this file, malicious actors can attempt to crack a large number of user passwords, which generally yields sufficient access to compromise all aspects of the network.
From a NIST CSF perspective, we want to know what went wrong here. The NIST CSF has several categories within the Protect function that directly address this attack path:
- PR.AC-4: Access permissions and authorizations are managed, incorporating the principles of least privilege and separation of duties
- PR.DS-1: Data-at-rest is protected
- PR.DS-5: Protections against data leaks are implemented
- PR.IP-4: Backups of information are conducted, maintained, and tested
We will look at each in turn.
PR.AC-4 – Access permissions and authorizations are managed, incorporating the principles of least privilege and separation of duties
In this case, the initial user who was compromised was considered a “standard” user without any specifically provided elevated permissions. Given that there is rarely a case for anyone except IT personnel to access backups or snapshots, this attack path represents a breakdown in access permissions. The overly permissive access control list(s) on the file share allowed users to access data for which they had no purpose to access.
Utilizing the principle of least privilege to minimize user access may have prevented this attack path. At the very least, proper application of permissions minimizes the attack surface and reduces the likelihood of exploitation.
To help with access control processes and technical implementation, organizations should ensure that they are using the right tool for the job. Public file shares are NOT the right place to store backups of any sort. In order to appropriately protect backups from exploitation (or perhaps even worse, ransomware) organizations should use dedicated backup platforms that support access controls, mechanisms such as write-only access so that only specific users can retrieve or view backup data, and segmentation (including off-site and/or physical) to prevent unauthorized access.
PR.DS-1 – Data-at-rest is Protected
Although this NIST CSF category is generally understood to mean that full-disk encryption is being utilized, this category also extends to protection and encryption of data at the application level as well. Full-disk encryption is ineffective in situations like this because access to the data happened digitally while the data was already accessible, not due to physical access to the device.
Had the snapshot files been encrypted with a strong key, Praetorian engineers would not have been able to access the actual data in the snapshots without expending significant and likely prohibitive resources to obtain the key material.
An alternative solution (in the case of virtual machines) might be to use the native virtual OS hard drive encryption tools to encrypt the data there. In that case, the snapshot itself would not require additional encryption. Many virtualization platforms also offer capabilities to encrypt virtual hard drives and snapshots.
PR.DS-5 – Protections against data leaks are implemented
Snapshots and backups are often fairly large files. In this particular case, the files were 23GB in total. A 23GB file transfer is not a common operation in most networks and necessary use cases can often be easily defined, baselined, and excepted from alerting. Such a large transfer of data either over a single connection or to/from a single host often indicates something nefarious is going on. Many data loss prevention (DLP) or network monitoring tools can be configured to detect large transfers, as long as sensors are placed in appropriate places within the network (both vertical and horizontal monitoring is best practice). For the purposes of this attack path, the file was initially exfiltrated to an internal host and then transferred out of the network, which makes two locations where the exfiltration could have been detected.
Sensors placed at the network boundary would have detected and potentially stopped this transfer, but generally, sensors are not placed on internal network segments. If an attacker is able to perform data extraction on an internal host, then boundary detection mechanisms may not be sufficient. If organizations choose to implement a DLP solution, they should ensure that the solution is applied both at the network boundary and between internal network segments.
PR.IP-4 – Backups of information are conducted, maintained, and tested
Although backups were being conducted and stored, those backups were not protected to the same degree as the original data, which falls under the “maintenance” aspect of PRI.IP-4. Backups are critical components to any recovery plan; without them, recovery is often impossible. Backups can become victims of ransomware, rendering them useless. Backups can also be victims of theft, as was the case in this particular situation.
As such, backups must be afforded the same protections as the primary data source. The security of backups must become a baseline cost of operation for both conducting and maintaining backups.
Conclusion
This particular attack path had at least four opportunities highlighted by the NIST CSF where the attack could have been thwarted: proper access control, encryption of backup data, data loss prevention mechanisms, and proper backup processes. The four sub-categories detailed here represent a small percentage of the 108 total sub-categories in the NIST CSF, just as a single finding represents only a small percentage of the overall risk that an organization carries with regard to its cybersecurity program.
Correct application of the NIST CSF can truly help organizations address risk in a systematic way. Each new control that an organization implements adds a layer to the Swiss Cheese Model or helps to close a hole in an existing layer. Using the NIST CSF objectives as a guide for control implementation within an organization maximizes the effectiveness of the security program. Used in an iterative manner, organizations can continually make incremental improvements to their security program to continue progress in a consistent fashion. This model points organizations in the right direction and helps to ensure the proper application of resources to primary business risks.