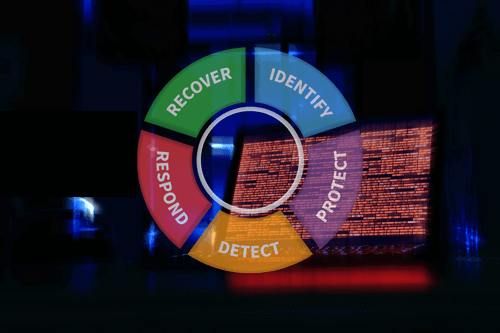
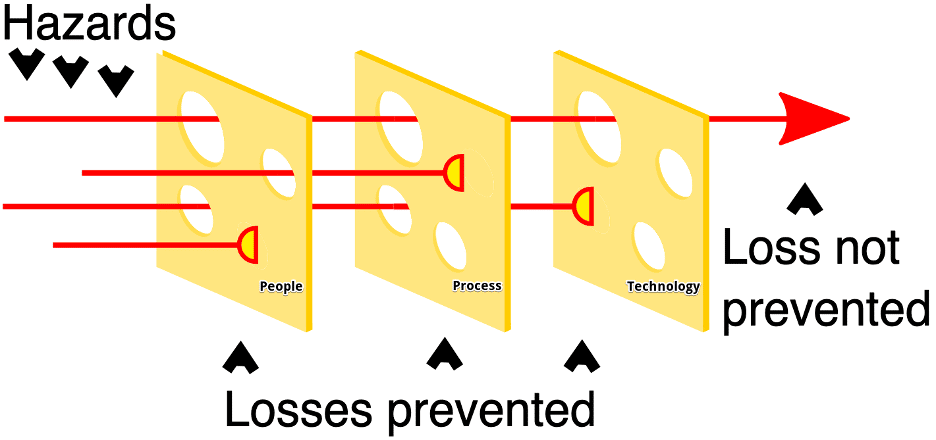
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) Vignettes series focuses on findings from recent security assessments that highlight the importance of different NIST CSF objectives. The NIST CSF provides a comprehensive framework for complex organizations to close gaps and add layers to the “Swiss Cheese Model.” The series seeks to demonstrate how the correct application of NIST CSF can prioritize and mitigate real risks to your organization. In our first post of the series, we examine how organizations apply resources to better combat phishing. In this article, we discuss how NIST CSF can be applied to combat Broadcast Name Resolution Poisoning.
A common tactic on many internal penetration tests and situations where Praetorian engineers gain physical access to a network is Broadcast Name Resolution Poisoning (BNRP). Recovery of hashed user credentials or relay of those credentials is often the intended goal of BNRP. On more than one occasion, engineers have successfully captured and cracked or relayed elevated user credentials (including domain administrators), ultimately resulting in a full network compromise. Broadcast Name Resolution protocols are not necessary in most modern and well-configured networks.
Windows networks tend to be especially susceptible to BNRP. Windows workstations utilize multiple legacy name resolution protocols by default. The protocols operate as fallbacks when modern DNS is either unavailable or is not able to properly resolve hostnames. An odd but intended behavior of several of these legacy name resolution protocols in Windows networks is that attackers and penetration testers can induce them to perform an authentication handshake that results in the delivery of hashed credentials to the attacking system. Without additional protections in place such as strong passwords or request signing mechanisms, attackers can easily crack and/or relay the captured credentials using publicly available tools to gain additional access on the network.
The NIST CSF has several sub-categories to address how an organization might start to mitigate this style of attack.
- TID.AM-3: Organizational communication and data flows are mapped
- ID.GV-1: Organizational cybersecurity policy is established and communicated
- PR.AC-2: Physical access to assets is managed and protected
- PR.AC-5: Network integrity is protected (e.g., network segregation, network segmentation)
- PR.IP-1: A baseline configuration of information technology/industrial control systems is created and maintained incorporating security principles (e.g. concept of least functionality)
- PR.PT-3: The principle of least functionality is incorporated by configuring systems to provide only essential capabilities
- DE.AE-1: A baseline of network operations and expected data flows for users and systems is established and managed
- DE.CM-3: Personnel activity is monitored to detect potential cybersecurity events
ID.AM-3, DE.AE-1 – Data flow and network baseline
As mentioned in the attack narrative, broadcast name resolution protocols such as Link-Local Multicast Name Resolution (LLMNR), NetBIOS Name Service (NBNS), Web Proxy Autodiscovery (WPAD), Multicast DNS (mDNS), and others are often enabled by default in many networks. The industry regards these protocols as “legacy,” though in many enterprises these protocols are still necessary components, or at the very least, still have an impact on network function.
IT administrators and defenders should map and define data flows and baseline network operations to determine if such protocols are even necessary. A mapping of required data flows can help to determine if such protocols are in use, their purpose, and where in the network there is a requirement for such protocols. With this information, administrators can have the necessary evidence to determine if these protocols are in use and what the best mitigation actions may be (disabling, segmenting, firewalling, etc.).
PR.AC-2 – Physical Access
One of the most common ways that attackers can conduct BNRP to gain additional access to a network is through unauthenticated access to the network, such as plugging in a rogue device or bypassing Network Access Controls (NAC) by compromising a device that is already on the network. Utilizing BNRP from an internal network position is a highly successful method to escalate from very little network access to potentially broad network access.
Protecting physical access to assets and to the network is always important. In this case, preventing physical access to assets may be enough to thwart this style of attack.
PR.AC-5 – Network Segmentation
In cases where organizations have legitimate and documented purposes for the use of broadcast name resolution protocols, disabling the services across the enterprise is simply not a reasonable mitigation strategy. Instead, administrators and security personnel should strive to collocate and segment the assets and services that require the use of these legacy protocols.
Collocating and segmenting the use of these broadcast name resolution services greatly reduces the attack surface, as attackers would need a fair amount of luck to land on the specific network segment where such services are present. Segmentation could further reduce the blast radius in the event that an attacker is successful at conducting a BNRP attack.
This level of segmentation allows administrators and security teams to continue work on securing the remainder of the network, while allowing critical business processes to continue.
PR.IP-1, PR.PT-3 – Configuration Baselines and Least Privilege
Several settings in current operating systems define whether legacy name resolution protocols are enabled or not. Many industry standard configuration benchmarks such as the CIS Benchmarks or DISA STIGs provide guidance on disabling these services. Organizations should define a baseline configuration standard. Both DISA STIGs and CIS Benchmarks exist for all modern operating systems. Configuring systems in accordance with these standards can mitigate several common vulnerabilities, and the use of a standard ensures that administrators have a guide to follow when configuring systems.
These configuration standards also incorporate least privilege practices. While access control is the most common way to address least privilege, least privilege can also mean “least functionality.” System configurations should allow only required services, so as to reduce attack surface. Ensuring that system configurations implement best practices and the principle of least functionality can aid in mitigating entire classes of attacks. The linked article at the top of this page demonstrates how improper application of least functionality can lead to exposure of Microsoft LAPS passwords in Active Directory domains.
ID.GV-1 – Cybersecurity Policy
Cybersecurity policy is generally a catch-all category; policy can encompass any security mechanism. In this specific instance though, policy plays an even stronger role. Often, our engineers encounter organizations that claim to utilize a configuration baseline or benchmark and that the network utilizes segmentation. Technical validation of these claims generally proves them to be false or inaccurate.
While IT administrators and security teams are very likely working diligently to do what they are saying, without a policy driving their actions, they will continually be at odds. Organizational cybersecurity policies should define what configuration baseline to use and the strategy for segmenting networks. By defining these items, the teams responsible for implementation can more easily focus their work, and when issues or confusion do arise, they have a guiding standard to use for resolution.
Conclusion
Most networks have several opportunities, as highlighted by the NIST CSF, to thwart BNRP attacks: physical access control, secure baseline configurations, network segmentation, and strong cybersecurity policy each could play a role in mitigating this style of attack. The seven sub-categories detailed here represent a small percentage of the 108 total sub-categories in the NIST CSF, just as a single finding represents only a small percentage of the overall risk that an organization carries with regard to its cybersecurity program.
Correct application of the NIST CSF can truly help organizations address risk in a systematic way. Each new control that an organization implements adds a layer to the Swiss Cheese Model or helps to close a hole in an existing layer. Using NIST CSF objectives as a guide for control implementation within an organization maximizes the effectiveness of the security program. Used in an iterative manner, organizations can continually make incremental improvements to their security program to continue progress in a consistent fashion. This model points organizations in the right direction and helps to ensure proper application of resources to primary business risks.
Share via: