TL;DR: Two medium-severity flaws, an unsecured email API endpoint and verbose error messages exposing OAuth tokens, chain together to enable authenticated phishing that bypasses all email security controls, persistent access to Microsoft 365 environments, and full infrastructure compromise. Neither flaw alone would be critical; combined, they’re devastating.
Modern web applications increasingly create attack surfaces through seemingly innocuous features. This article examines how two independent security weaknesses can combine to create a high-impact attack chain, demonstrating why security teams must think beyond isolated vulnerabilities to understand real-world exploitation paths.
Background & Context
Why This Matters
Email remains the primary vector for initial access in modern cyberattacks. According to Verizon’s 2025 Data Breach Investigations Report, email was the initial attack vector in 27% of reported breaches, with 60% of all breaches involving some form of human element.¹ However, SPF, DKIM, and DMARC authentication protocols, combined with advanced AI-driven spam filters, have made traditional phishing increasingly difficult.
So what happens when attackers can send phishing emails that pass every authentication check? That’s exactly what certain email vulnerabilities enable.
Modern web applications expose communication endpoints for legitimate business functions: newsletter signups, contact forms, password resets. These endpoints create inherent security tension. They must remain publicly accessible while preventing misuse. When implemented without sufficient input restrictions, attackers can send emails through an organization’s legitimate infrastructure, bypassing all email authentication and security controls.
Similarly, verbose error messages designed to aid debugging can inadvertently expose sensitive information including authentication tokens and internal system details. In modern cloud environments with single identity providers across multiple services, a token exposed in one application’s error message could grant access to an ecosystem of connected resources.
Technical Details
Reconnaissance often reveals functionality that organizations assume is hidden. While many security-sensitive pages aren’t directly linked from a website’s navigation, search engine indexing can expose them. A simple Google dork such as site:domain.com sign up can reveal newsletter signup forms, account registration pages, and other communication endpoints in the top search results. These pages, even if not advertised or linked in the site’s main navigation, remain fully functional and accessible to anyone who discovers them.
Vulnerability Chain Part 1: Email Endpoint Abuse Enabling Sophisticated Phishing
Consider a common pattern in modern web applications: a newsletter signup form on a public website where users enter their email address to receive regular updates. Behind this simple interface lies an API endpoint, typically something like /api/newsletter/subscribe, that processes these requests.
The security issue emerges when these endpoints lack proper authentication and accept arbitrary JSON payloads that control email recipients, subject lines, and HTML body content. When applications send these emails through the organization’s official email infrastructure, messages originate from legitimate mailboxes with all proper authentication in place.
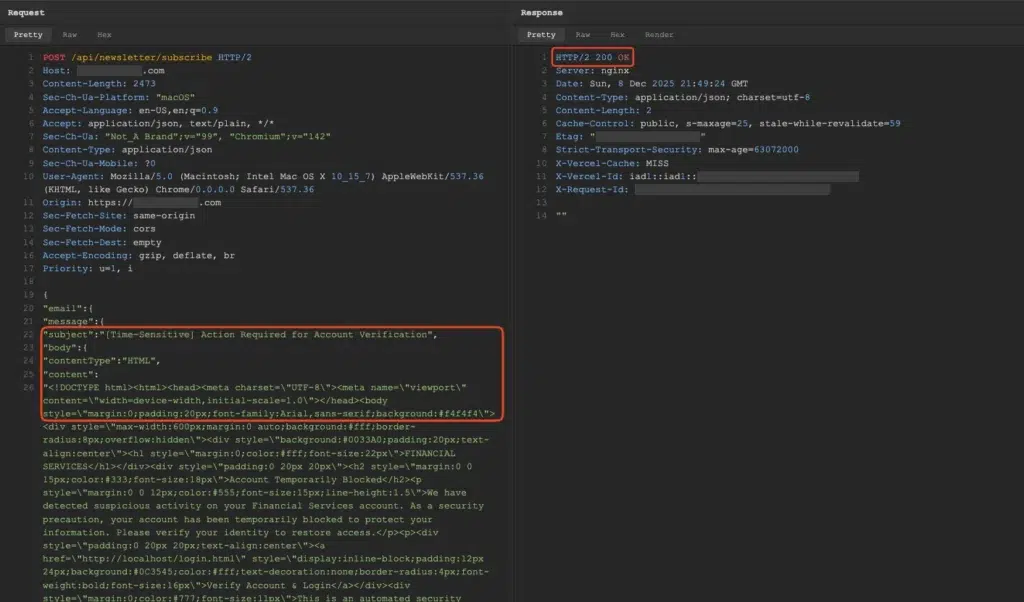
In practice, this means attackers can weaponize your own email infrastructure against your employees and customers.
This capability enables several attack scenarios:
- Credential harvesting through convincing phishing pages
- Malware distribution disguised as legitimate company communications
- Social engineering attacks leveraging the organization’s trusted reputation
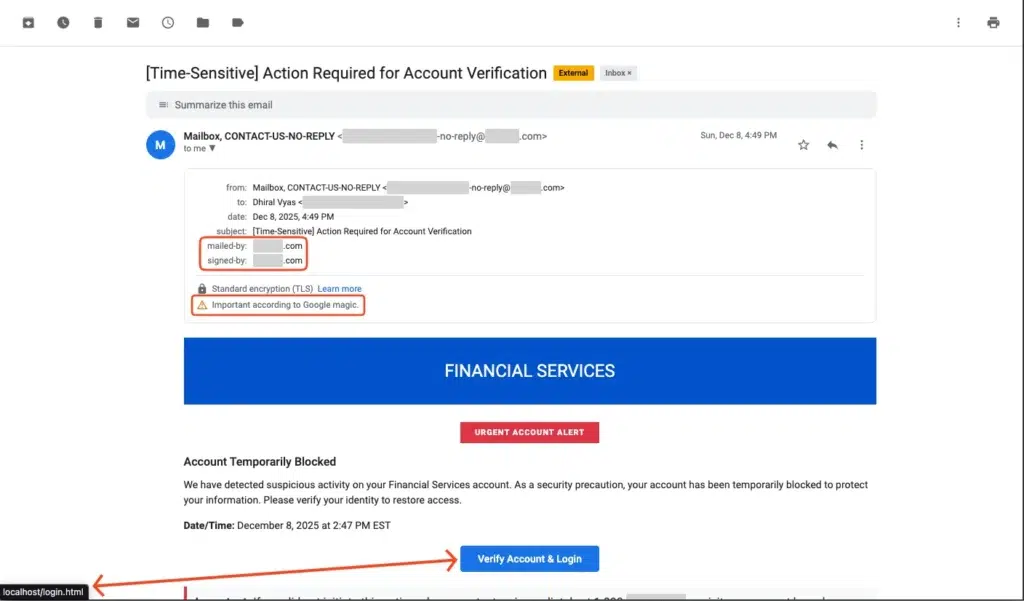
A proof-of-concept demonstrates the severity: a phishing email mimicking an urgent security notification, crafted with convincing branding and an urgent call to action. When delivered through the vulnerable endpoint, this email:
- Passes all SPF, DKIM, and DMARC authentication checks
- Displays the organization’s official email address as the sender
- Gets automatically tagged as “Important” by Gmail due to its legitimate origin
- Appears in recipients’ primary inbox, not spam folders
While this vulnerability is severe on its own, the security impact amplifies significantly when paired with another flaw.
Vulnerability Chain Part 2: The Token Exposure
The second vulnerability pattern involves verbose error handling. When testing email endpoints with various payloads, submitting malformed requests by omitting required fields can trigger detailed error responses. Instead of returning generic error messages, poorly configured applications respond with full stack traces containing execution paths, variable values, and crucially, authentication credentials.
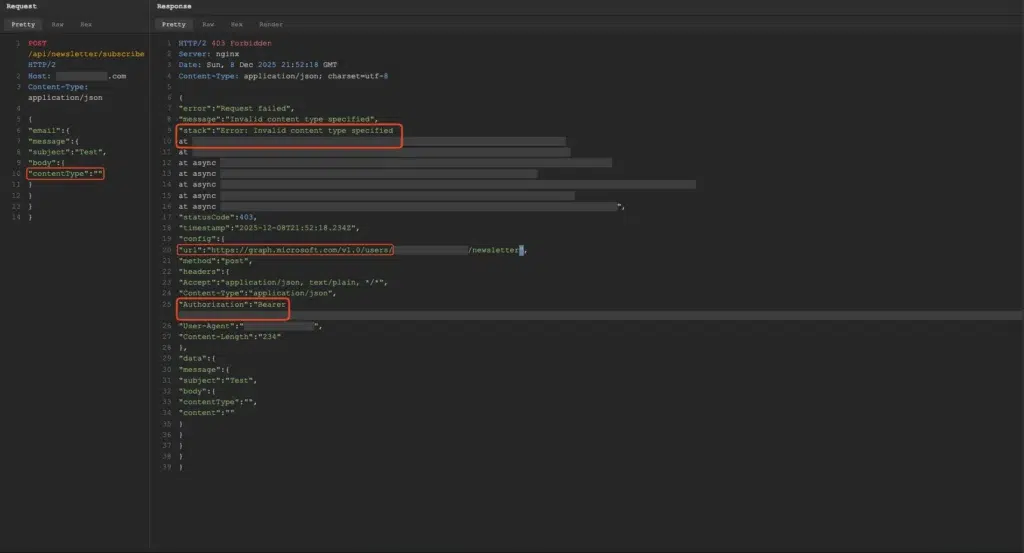
A natural question is: why would an error response contain authentication tokens? In many modern applications, internal services authenticate to each other using OAuth tokens stored in application context. When verbose error handling dumps that context to the client, the tokens come along for the ride.
In this pattern, error responses exposed OAuth 2.0 bearer tokens used to authenticate to Microsoft 365 Graph API. These exposed tokens are JSON Web Tokens (JWT) with permissions to access organizational resources.
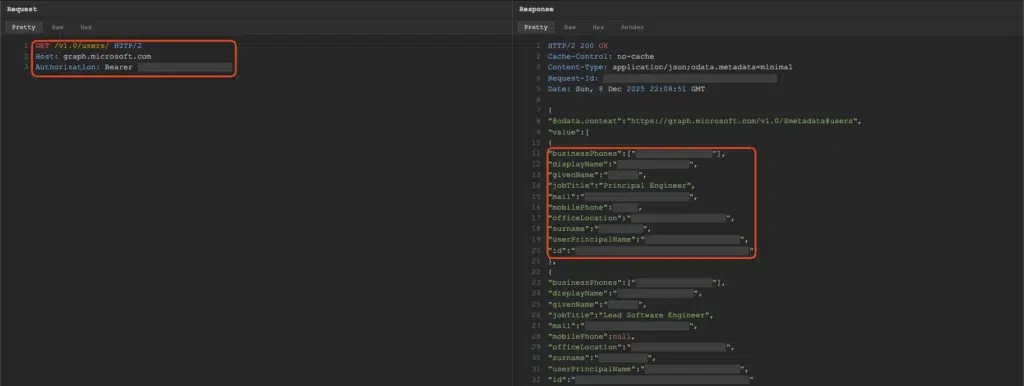
Analysis of such tokens typically reveals access to:
- User profile information including full names and locations
- Contact information and organizational structure including phone numbers, email addresses, and job titles
- Microsoft tenant information including UserPrincipalName and internal IDs
However, the potential impact extends far beyond basic directory information. Depending on token permissions, attackers could gain access to:
Communication and Collaboration:
- Calendar data and meeting information
- Microsoft Teams conversations, channels, and shared files
- Full email capabilities, including sending and receiving messages with attachments for malware delivery and command-and-control communication
Data and File Systems:
- Files and documents stored in SharePoint sites
- Personal files stored in individual OneDrive accounts
- Shared organizational resources and sensitive documents
Infrastructure and Management:
- Azure resources and infrastructure configurations (depending on token scope)
- Intune device management capabilities, allowing control over enrolled devices
- The ability to pivot from Microsoft 365 to the broader Azure environment, potentially leading to widespread infrastructure compromise
Here’s the critical insight: while tokens typically have short time-to-live values, attackers can simply regenerate new tokens by repeatedly triggering the error condition. The vulnerability becomes a token dispensary, providing persistent access that survives credential rotation.
Real-World Attack Scenario
Let’s walk through how a sophisticated adversary might exploit this vulnerability chain:
Stage 1: Token Extraction and Initial Access
The attacker discovers the verbose error condition and extracts a valid Microsoft Graph OAuth token. This provides immediate, authenticated access to the organization’s Microsoft 365 environment without triggering typical failed authentication alerts.
Stage 2: Permission Enumeration and Reconnaissance
Using the token, the attacker enumerates their actual access level and begins systematic reconnaissance. At minimum, they can access employee directories, organizational charts, contact information, and user profiles. Depending on the token’s scope, they may also have access to SharePoint sites, Teams channels, OneDrive files, calendar data, or even Azure and Intune management capabilities.
Stage 3: Dual-Track Exploitation
The attacker pursues parallel attack paths:
Direct Data Access: For resources accessible via the Graph token, the attacker silently exfiltrates data such as documents, communications, meeting notes, and organizational information. This occurs without generating suspicious authentication events since they’re using a legitimate token.
Credential Phishing: For resources beyond the token’s scope or to gain deeper access, the attacker leverages the email endpoint and token access to send highly targeted phishing campaigns. Using organizational intelligence gathered from the Graph API, they craft convincing emails that reference real projects, impersonate specific internal employees, and use accurate internal terminology. These emails originate from the organization’s trusted infrastructure, dramatically increasing success rates.
Stage 4: Privilege Escalation and Infrastructure Pivot
Armed with credentials from successful phishing attacks, the attacker escalates privileges within Microsoft 365 and potentially pivots to Azure infrastructure. If the original token included Azure-related permissions, they could directly access cloud resources, databases, and production infrastructure. Otherwise, harvested credentials provide the pathway to these systems.
Stage 5: Persistence and Long-Term Access
The attacker establishes multiple persistence mechanisms: creating backdoor service principals, adding hidden administrative accounts, or leveraging Intune to deploy monitoring tools on managed devices. Until the verbose error condition is fixed, they can maintain access by regenerating tokens through the error condition, allowing them to retain access even as individual credentials are rotated.
The Broader Lesson: Defense Through Proper Security Controls
These vulnerability patterns highlight two fundamental security principles.
First, public-facing APIs should enforce strict input validation that aligns with their intended business purpose. Accepting only the minimal required parameters, implementing rate limiting, and monitoring for anomalous patterns can prevent functionality abuse even when endpoints must remain publicly accessible.
Second, production environments require a fundamentally different approach to error handling than development environments. While detailed error messages aid debugging during development, production systems must balance operational needs with security requirements by returning generic errors to clients while logging detailed information server-side for authorized personnel.
The takeaway is clear: your email infrastructure and your error messages are both potential weapons. Attackers need only find them and pull the trigger.
Conclusion
This analysis demonstrates how chaining several vulnerabilities together can significantly increase the overall risk when combined. While individual weaknesses may appear manageable in isolation, sophisticated adversaries look for these combinations to amplify their capabilities. Security teams must think beyond individual findings and consider how their attack surface might enable multi-stage exploitation paths.
We’ve consistently observed that organizations focus remediation efforts on high-severity individual findings while overlooking medium-severity issues that chain into critical attack paths. The vulnerabilities described here might each warrant a “medium” severity rating in isolation. Combined, they enable complete infrastructure compromise.
Organizations should regularly assess their web applications for these types of chained vulnerabilities. By thinking like adversaries and testing real-world attack scenarios, security teams can discover and remediate security gaps before they’re exploited.
Concerned about vulnerability chaining in your environment? Praetorian’s offensive security platform identifies exploitation paths that scanners miss, validating real-world attack chains before adversaries find them. See how continuous validation works or explore our security research for more technical deep-dives.
References
Frequently Asked Questions
What is vulnerability chaining?
Vulnerability chaining is an attack technique where adversaries combine multiple lower-severity security weaknesses to achieve high-impact compromise. Individual flaws that might be rated as medium or low risk in isolation can escalate to critical severity when exploited together in sequence. This approach reflects how real-world attackers operate: they rarely rely on a single vulnerability when multiple weaknesses can be combined for greater effect.
How do attackers exploit newsletter signup forms for phishing?
When newsletter API endpoints accept arbitrary JSON payloads controlling recipient, subject, and body without authentication, attackers can send emails through the organization’s legitimate infrastructure. These emails pass all authentication checks (SPF, DKIM, DMARC) because they genuinely originate from authorized mail servers, landing in primary inboxes rather than spam folders.
What is OAuth token hijacking?
OAuth token hijacking occurs when attackers obtain valid OAuth access tokens through unintended means, such as verbose error messages, insecure storage, or man-in-the-middle attacks. Once obtained, these tokens can be used to access any resource the token has permissions for, without needing the user’s credentials directly.
How do attackers bypass email authentication like SPF and DMARC?
Rather than bypassing these protocols, sophisticated attackers work around them by sending emails through legitimate infrastructure. When an organization’s own email API can be abused to send arbitrary content, the resulting emails pass all authentication checks because they genuinely originate from authorized servers. The protocols work correctly; they just can’t distinguish between legitimate and malicious use of authorized infrastructure.
What permissions do Microsoft Graph API tokens typically have?
Microsoft Graph tokens can have widely varying permissions depending on how the application was configured. Common scopes include user profile access, email read/send capabilities, calendar access, file access (OneDrive/SharePoint), Teams messaging, and directory enumeration. In misconfigured applications, tokens may also include Azure resource management or Intune device management permissions.
How can organizations prevent OAuth token exposure in error messages?
Implement environment-specific error handling. Production systems should return generic error messages to clients while logging detailed information server-side for authorized personnel only. Never include authentication tokens, API keys, or credentials in client-facing error responses. Use error tracking services that capture details securely rather than exposing them to end users.
How long do exposed OAuth tokens remain valid?
Microsoft Graph tokens typically have a 1-hour TTL by default. However, attackers can maintain persistent access by repeatedly triggering the error condition to obtain fresh tokens, making the vulnerability effectively persistent until the error handling is fixed, even if individual tokens expire.
Why don’t vulnerability scanners catch these attack chains?
Most vulnerability scanners and security tools assess findings individually. An email endpoint accepting extra parameters might score as “informational.” Verbose error messages might rate as “low” severity. Only manual analysis, penetration testing, or specialized attack path modeling identifies how these combine into critical-severity attack chains, which is why regular security assessments remain essential.

