For many organizations, cybersecurity is measured more by feelings and emotions than it is by any objective measure of reduced risk. Without a framework or standard, cybersecurity programs struggle to assess their own maturity and effectiveness. Most recognize that mere “checklist compliance” is not enough to thwart modern adversaries. It is also common to have a disconnect between senior leadership and security engineers who are attempting to solve complex cybersecurity problems in the frontlines. At Praetorian, we have helped a number of organizations address these complexities, misconceptions, and misalignments by using the NIST Cyber Security Framework.
What is the NIST CSF?
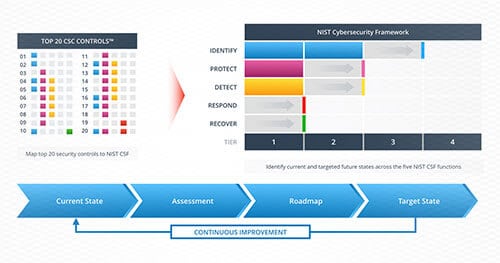
The Cyber Security Framework (CSF) is a set of security controls developed by the National Institute of Standards and Technology (NIST) and industry partners to help organizations mature their cybersecurity program. The CSF is partitioned into five function areas: Identify, Protect, Detect, Respond, and Recover. Each of these functional areas are broken down into categories and sub-categories, and, as of version 1.1 of the NIST CSF, there are a total of 108 cyber security controls. These controls within the CSF map directly to well-known security frameworks such as ISO 27001, COBIT 5, CIS CSC and NIST 800-53. A sample of the controls include logging and monitoring, security awareness, vulnerability management, and incident response. Assessing the effectiveness of the controls allows organizations to measure how its cybersecurity program is operating.
Leveraging the NIST CSF to address risk
Reporting the state of cybersecurity programs to executives has always been a difficult problem for IT security teams. Using the NIST CSF allows organizations to objectively measure and identify areas where gaps in coverage may exist. It allows senior leadership to get a 10,000-foot view of the state of their cybersecurity program, and it allows front line practitioners to have a voice in the state of security controls. Creating this alignment from senior leadership to frontline engineers can focus resources to address cybersecurity problems.
How does Praetorian do NIST CSF assessments differently?
There are many reasons why Praetorian stands apart from others in the way we conduct NIST CSF assessments. Chief among them is our ability to think like an attacker. When Praetorian engineers engage a NIST CSF assessment, we utilize and leverage our attacker mindset, which is not commonly found in assessors reviewing security controls for organizations. Praetorians refer to this offensive mindset internally as our “Adversarial DNA”, which allows the security engineers to mimic how an attacker would attempt to circumvent security controls. Most NIST CSF security assessors will not have this attacker mindset, and that sets Praetorian engineers apart from the rest. The Praetorian engineers conducting the NIST CSF assessments have each had first-hand experience conducting various security assessments for clients, including Red Teams, Penetration Tests, and Application Security Assessments.
The Cyber Security Roadmap
After conducting the in-depth CSF assessment, Praetorian creates a custom Cyber Security Roadmap to help organizations address their pressing cybersecurity issues. This roadmap includes prioritized recommendations and detailed next steps to address security concerns, focusing on people, process, and technology. Utilizing this roadmap can allow organizations to prioritize allocation of resources to best reduce risk. The unbiased opinions from Praetorian engineers allows organizations to have a true benchmark of their security program and a path forward to building a stronger security posture.