How to Create a Secure Authentication Scheme for IoT Systems

This article discusses some of the common authentication pitfalls that Praetorian has observed in IoT devices and address ways to fix these problems.
NIST Cybersecurity Framework Vignettes: Phishing
This article examines the application of the NIST Cybersecurity Framework for addressing phishing concerns.
Attacking and Defending OAuth 2.0 (Part 1 of 2: Introduction, Threats, and Best Practices)

First of a two-part series discussing OAuth 2.0 from the perspective of a security engineer in both an offensive and defensive role
Active Directory Computer Account SMB Relaying Attack

This article outlines a unique Active Directory attack vector that arises when a computer account has administrative access to another computer.
Solving Cybersecurity’s Hardest Problems with Machine Learning

This article provides a glimpse into some of the groundbreaking work that the experts at Praetorian are undertaking, applying Machine Learning to solve some of the industry’s most challenging problems.
Leveraging DevSecOps Practices to Secure Red Team Infrastructure
This article explores how Red Teams can leverage DevSecOps best practices, including automating policy enforcement using OPA for secure Red Team Architecture
Praetorian’s Approach to Red Team Infrastructure
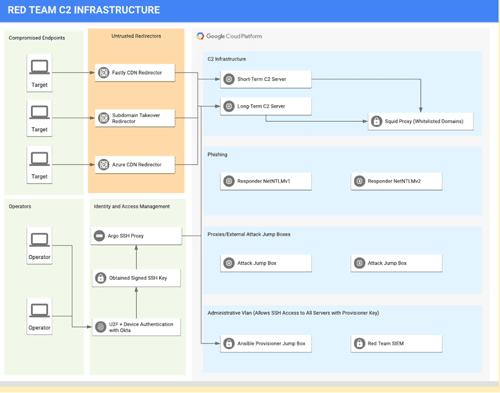
Praetorian provides a best practices approach to Red Team Infrastructure using a Google BeyondCorp architecture
Cloud Security and Architecture: The 8 Pillars

Praetorian has created a 8-pillar framework to simplify the assessment of multi-cloud environments across a broad client base. Together with proven methodologies for enterprise and product security, the framework provides a holistic approach to securing organizations from chip to cloud.
Obtaining LAPS Passwords Through LDAP Relaying Attacks

Commentary on Praetorian’s recent contribution of additional functionality to the Impacket ntlmrelayx utility.
AWS IAM Assume Role Vulnerabilities Found in Many Top Vendors

Research by Praetorian has uncovered a common misconfiguration in Amazon Web Services Identity and Access Management Assume Role process. This post outlines the issue and how it can be mitigated.