A simple and effective way to detect Broadcast Name Resolution Poisoning (BNRP)

A natural question that arises after an organization experiences a BNRP attack is “How can this be prevented?” The answer is simple on paper. To completely mitigate the risk, legacy Broadcast Name Resolution protocols should be disabled by policy. This is easier said than done, especially on large networks where the necessary data flows of […]
Alibaba Cloud Cross Account Trust: The Confused Deputy Problem

In this second blog post in our series on cross-account trust, we explore Alibaba Cloud and the security implications of their trust model.
Google Cloud Platform (GCP) Service Account-based Privilege Escalation paths

This article examines a Google Cloud Platform (GCP) risk scenario, in which a malicious user can use their privileges in a compromised service to further escalate their privileges.
NIST Cybersecurity Framework Vignettes: Broadcast Name Resolution Poisoning
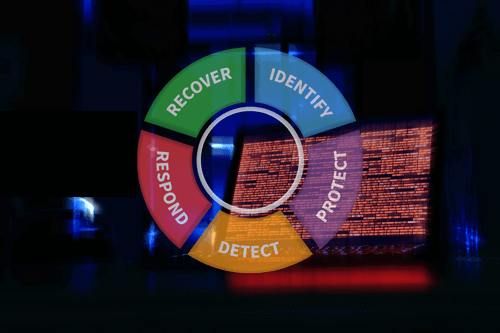
Our NIST Cybersecurity Framework Vignettes series focuses on the best applications of NIST CSF for your organization. This article addresses the tactic of Broadcast Name Resolution Poisoning.
Building a Domain Specific Language for Red Team Payload Generation

This article shares how Praetorian developed a customer YAML-based domain-specific language (DSL) to specify red team dropper behavior.
Inside the Mimikatz Pass-the-Hash Command (Part 2)

Second in a two-part series providing an overview of how the Mimikatz pass-the-hash command works.
Inside the Mimikatz Pass-the-Hash Command (Part 1)

First in a two-part series providing an overview of how the Mimikatz pass-the-hash command works.
A New Tool for Password Spraying Emulation

This article introduces Trident, an open-source cybersecurity tool for emulating password spraying.
Threat Hunting: How to Detect PsExec

This article profiles the use of the PsExec command-line tool as a cyber-attack technique, and how threat hunters can detect it.
Red Team Infrastructure Tooling: Command Line Utilities and U2F
This article shares observations and best practices for red team infrastructure tooling, with a focus on command-line applications to manage server infrastructure.