Capturing Exposed AWS Keys During Dynamic Web Application Tests
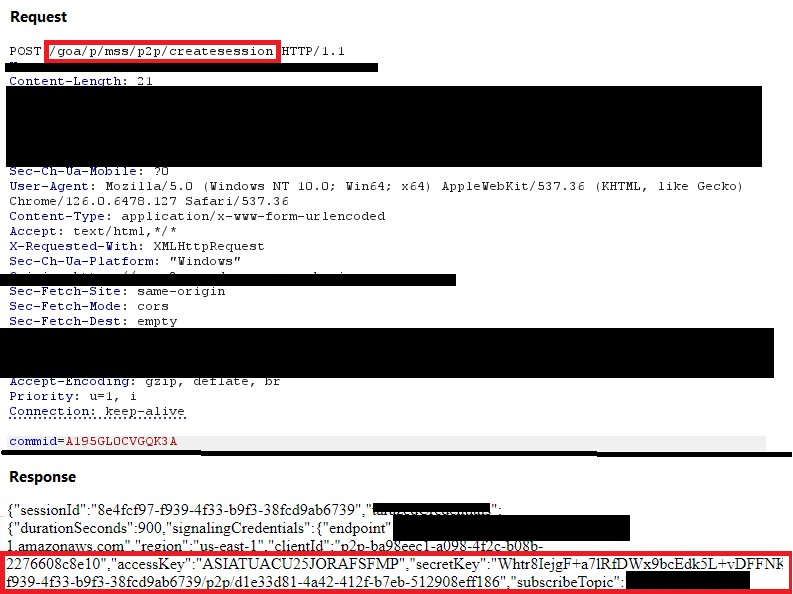
Overview We have recently identified several vulnerable HTTP requests that allow attackers to capture access keys and session tokens for a web application’s AWS infrastructure. Attackers could use these keys and tokens to access back-end IOT endpoints and CloudWatch instances to execute commands. This blog was developed to raise awareness on common design flaws in […]