CI/CD Security Assessment
An offensive approach to securing your Continuous Integration and Continuous Delivery (CI/CD) pipeline against advanced threats
Proactively Identify and Mitigate Vulnerabilities in your CI/CD Pipelines
By simulating advanced attack scenarios, we uncover hidden vulnerabilities and offer actionable insights to strengthen your development and deployment processes against real-world threats. By seamlessly integrating into your DevOps practices, security becomes a core component of your software development lifecycle, not merely an afterthought.
Early Detection and Mitigation
Identify vulnerabilities early in development lifecycle to reduce risk, time lost, and costs associated with late security issues.
Comprehensive View of Your CI/CD Attack Chain
Gain complete understanding of your CI/CD pipeline's security. This includes assessing the security of code repositories and deployment environments to eliminate any vulnerabilities in your pipeline.
Enhanced DevSecOps Collaboration
Fostering collaboration between developers and security teams to build inherently secure applications from the start.
CI/CD Pipeline Vulnerability Assessment
Comprehensive evaluation of your pipeline to identify vulnerabilities, misconfigurations, and potential attack vectors.
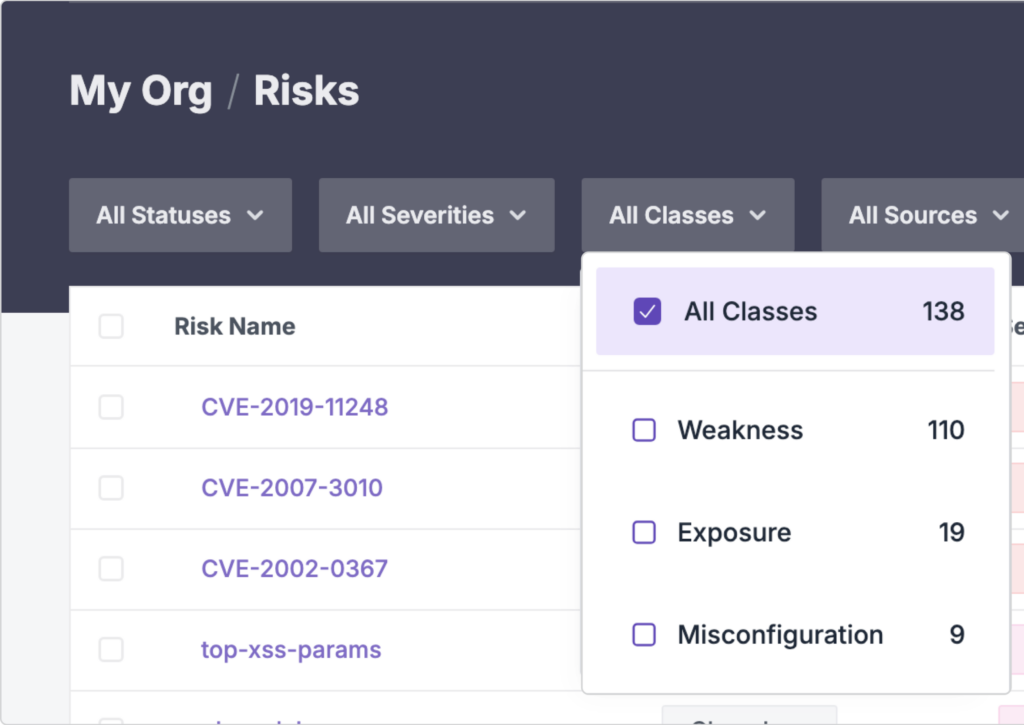
Attack Simulation and Penetration Testing
Remediation Guidance and Support
Get a Comprehensive Analysis of What Can Go Wrong at Each Layer of Your Supply Chain
Increased Security Confidence
Gain peace of mind knowing your CI/CD pipelines are protected against the latest threats with our cutting-edge security measures and expert guidance.
Reduced Risk of Data Breaches
Minimize the risk of costly data breaches and reputational damage by securing your software delivery pipeline from end to end.
Faster, Safe, Software Releases
Accelerate your software release cycle with the confidence that security has been integrated at every stage of your CI/CD pipeline, from development to deployment.
Compliance and Industry Standards Adherence
Ensure your CI/CD practices comply with relevant industry standards and regulations, protecting your organization from potential legal and financial penalties.
Ready to Discuss Your CI/CD Security Assessment?
Praetorian’s Offense Security Experts are Ready to Answer Your Questions