From Self-Hosted GitHub Runner to Self-Hosted Backdoor
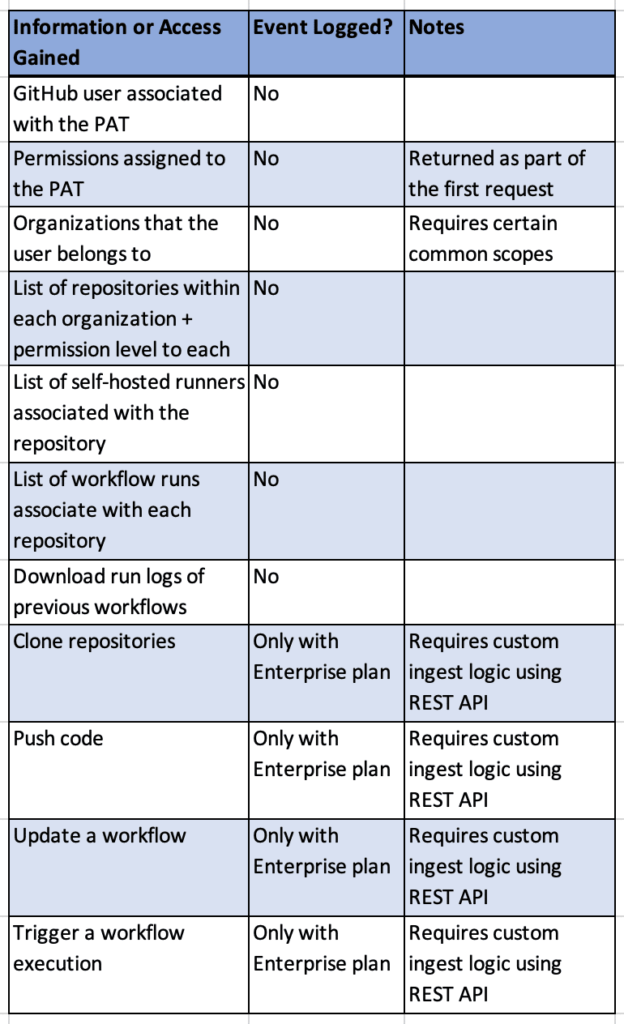
Overview Continuous Integration and Continuous Delivery (CI/CD) systems are powerful and configurable tools within modern environments. At Praetorian, we are seeing organizations migrate to SaaS solutions like GitHub (GitHub.com) as their source code management and CI/CD solution, instead of on-premises tools like BitBucket, Bamboo, and Jenkins. On our Red Team engagements , we routinely employ […]
Multi-Step Attack Vectors: When Vulnerabilities Form an Attack Chain
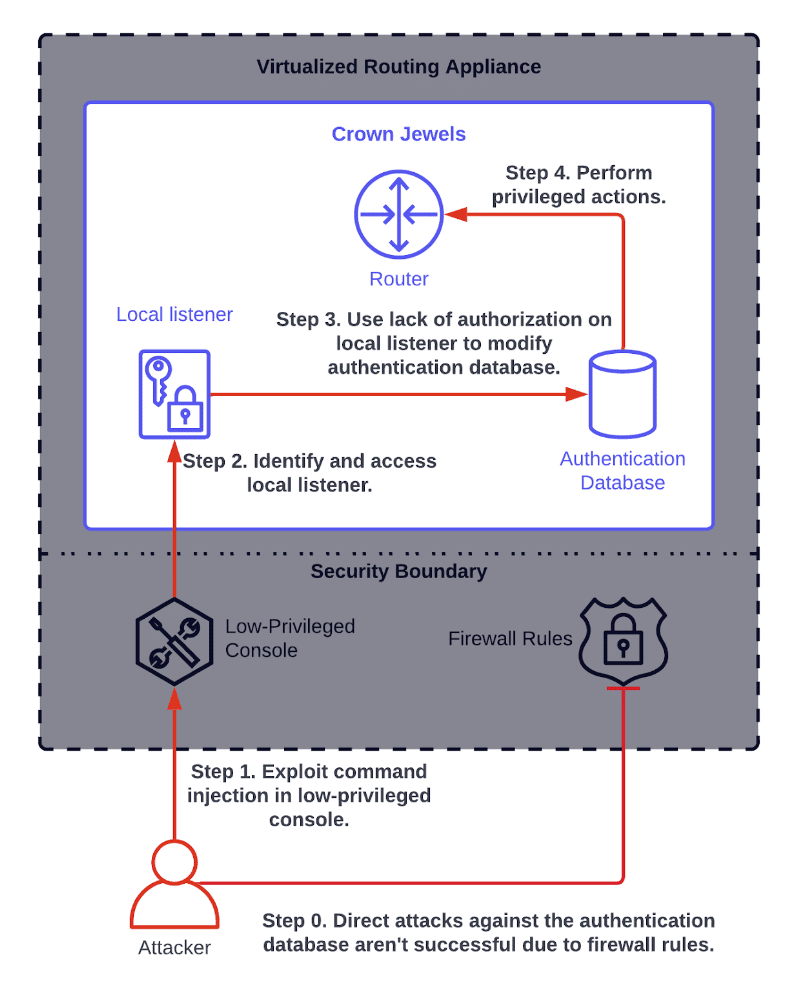
Praetorian’s approach to cybersecurity centers around a core belief that combining innovative technologies and the best people in the business leads to real results. In our experience, neither can fully solve cybersecurity challenges on its own. We therefore have designed our services organization and offerings to blend them seamlessly. We applied the same philosophy when […]
How to Detect DFSCoerce
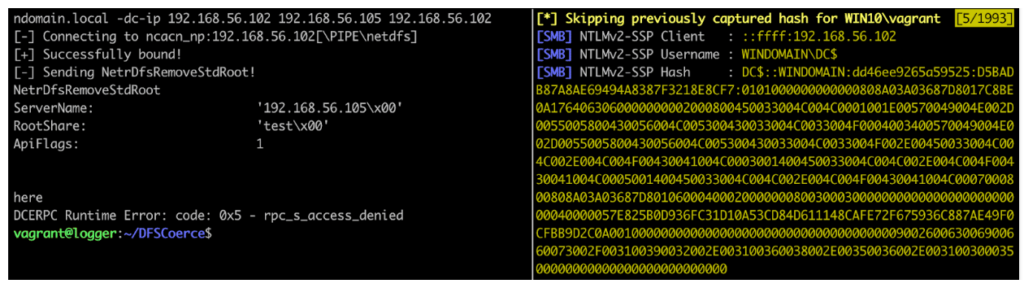
Background On 18 June 2022, security researcher Filip Dragovic published proof-of-concept code for a new forced authentication technique named DFSCoerce. This technique, inspired by other forced authentication techniques like PetitPotam and SpoolSample, often is used to force a victim Windows host to authenticate to an attacker’s machine. The attacker can then relay the credentials to […]
Chaining MFA-Enabled IAM Users with IAM Roles for Potential Privilege Escalation in AWS

Overview In AWS, sts:AssumeRole is an action within AWS’s Security Token Service that allows existing IAM principals to access AWS resources to which they may not already have access. For example, Role A can assume Role B and then use Role B’s privileges to access AWS resources. Common use cases include assuming a role within […]
Palo Alto Networks GlobalProtect Remote Code Execution Vulnerability (CVE-2022-0016)

Overview Application developers often expose functionality from a Windows login screen. The common functionality needed from a login screen includes password reset mechanisms and VPN onboarding processes. Pre-authentication functionality exposes high-value attack surfaces. An unauthenticated external attacker with network connectivity to the Remote Desktop Service (RDP) on the target host can access the components exposed […]
Log4j 2.15.0 stills allows for exfiltration of sensitive data

The Apache Software Foundation announced a new vulnerability in Log4j – CVE-2021-45046 – on December 14th. The vulnerability as described states that Log4j 2.15.0 can allow a local Denial of Service attack, but that impacts are limited. However, in our research we have demonstrated that 2.15.0 can still allow for exfiltration of sensitive data in […]
How to Prevent, Detect and Remediate ProxyLogon

Summary Our labs team’s ability to recreate a reliable end-to-end exploit underscores the severity of the ProxyLogon vulnerability. Compounding the criticality of this vulnerability, we’ve been able to use the ProxyLogon vulnerability in conjunction with a common Active Directory misconfiguration to achieve organization-wide compromise. The Active Directory and Exchange permission path issue up until now […]
Reproducing the Microsoft Exchange Proxylogon Exploit Chain

Introduction In recent weeks, Microsoft has detected multiple 0-day exploits being used to attack on-premises versions of Microsoft Exchange Server in a ubiquitous global attack. ProxyLogon is the name given to CVE-2021-26855, a vulnerability on Microsoft Exchange Server that allows an attacker to bypass authentication and impersonate users. In the attacks observed, threat actors used […]