Getting Started with Praetorian’s ATT&CK Automation
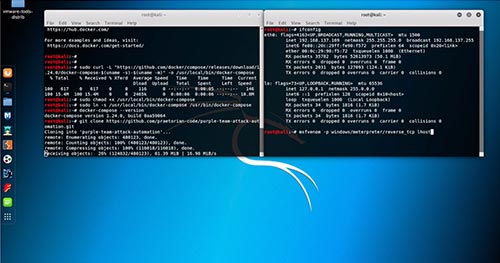
Earlier this month, Praetorian released its automation for emulating adversary tactics, techniques, and procedures (TTPs) based on the MITRE ATT&CK framework. We’ve gotten a number of requests from users asking for more detailed instructions on how to get started with the tool. This blog post accompanies the recently released video tutorial.
Why Praetorian Benchmarks to MITRE ATT&CK™ and Why You Should Too

When it came to improving our Purple Team service line, which maps to “Detect” and “Respond” in the NIST CSF, we wanted to provide a similar high quality of data and metrics to our clients. In our experience, it is hard to drive change in any organization unless those changes can be tied to measurable results. After conducting a survey of known frameworks, we settled on the ATT&CK™ framework from MITRE.
Summary of April MITRE ATT&CK RELEASE

MITRE’s Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK™) is a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s lifecycle and the platforms they are known to target. ATT&CK is useful for understanding security risk against known adversary behavior, for planning security improvements, and verifying defenses work as expected.