Refresh: Compromising F5 BIG-IP With Request Smuggling | CVE-2023-46747

Overview In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities that are likely to impact the security of leading organizations. We decided to focus on the F5 BIG-IP suite, as F5 products are fairly ubiquitous among large corporations. We targeted the F5 BIG-IP Virtual Edition […]
Technical Advisory: F5 BIG-IP Unauthenticated RCE Vulnerability, CVE-2023-46747
Overview In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities that are likely to impact the security of leading organizations. Recently, we discovered a vulnerability which can lead to unauthenticated remote code execution on F5 BIG-IP instances with the Traffic Management User Interface exposed. This […]
Understanding the Recent Confluence Vulnerability (CVE-2023-22515) and Digging into Atlassian Bamboo

Overview Recently, Rapid7 disclosed a vulnerability within Confluence that allowed a remote unauthenticated attacker to create a new administrative user account by bypassing the XWork SafeParameterFilter functionality. Our vulnerability research team decided to take a look at another Atlassian product, Atlassian Bamboo, to determine if a similar vulnerability existed within that application. In this post, […]
Advisory: Qlik Original Fix for CVE 2023-41265 Vulnerable to RCE
Overview On August 29th, 2023 Qlik issued a patch for two vulnerabilities we identified in Qlik Sense Enterprise, CVE-2023-41265 and CVE-2023-41266. These vulnerabilities allowed for unauthenticated remote code execution via path traversal and HTTP request tunneling. As part of our standard operating procedure, we performed a diff of the issued patch to identify potential bypasses […]
ZeroQlik: Achieving Unauthenticated Remote Code Execution via HTTP Request Tunneling and Path Traversal
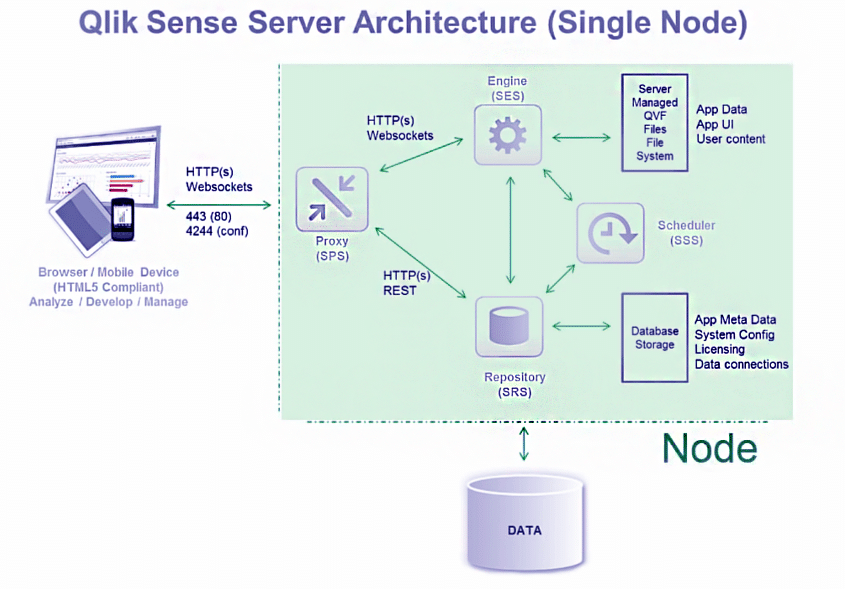
Overview In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities that are likely to impact the security of leading organizations. Recently, we decided to take a look at Qlik Sense Enterprise, a data analytics solution similar to Tableau. The recent exploitation of vulnerabilities in the […]
Advisory: Qlik Sense Enterprise for Windows Remote Code Execution Vulnerabilities
Advisory: Qlik Sense Enterprise Remote Code Execution In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities in applications that are likely to impact the security of leading organizations. Recently, we discovered two vulnerabilities which can be chained together to achieve unauthenticated remote code execution on […]