Introducing: GitHub Device Code Phishing

What if all it took to compromise a GitHub organization–and thus, the organization’s supply chain–was an eight-digit code and a phone call? Introducing: GitHub Device Code Phishing. While security teams have been battling Azure Active Directory device code phishing attacks for years, threat actors have overlooked GitHub’s OAuth2 device flow as an attack vector. At […]
Long Live the Pwn Request: Hacking Microsoft GitHub Repositories and More
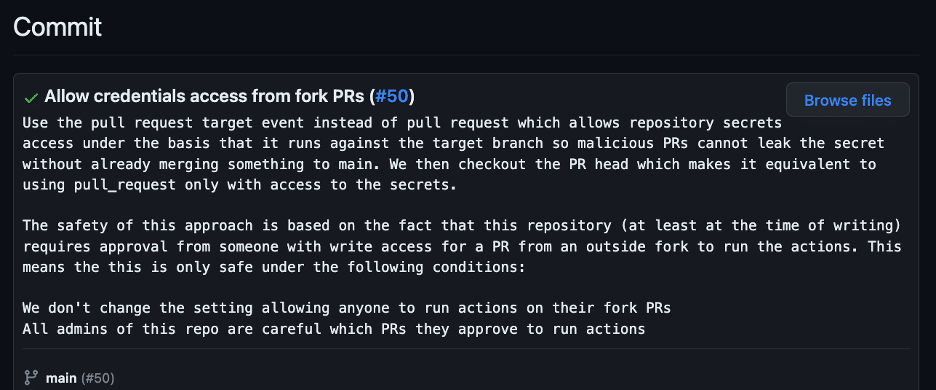
Software supply chain attacks have been increasing both in frequency and severity in recent months. In response to these attacks, the CISA has even released a cybersecurity information sheet (CSI) on how organizations can secure their CI/CD pipelines. The introduction to the CSI states: “(The) CSI explains how to integrate security best practices into typical […]
Announcing Gato Version 1.5!

On January 21, 2023 at ShmooCon 2023, Praetorian open-sourced Gato (Github Attack Toolkit), a first of its kind tool that focuses on abusing offensive TTPs targeting self-hosted GitHub Actions Runners. Since then, Praetorian and other offensive security practitioners across the information security community have leveraged Gato for so much more than just self-hosted runner attacks. […]
Phantom of the Pipeline: Abusing Self-Hosted CI/CD Runners

Introduction Throughout numerous Red Teams in 2022, a common theme of Source Control Supply Chain attacks in GitHub repositories has emerged. After many hours manually hunting for and exploiting these attack paths, we’ve built an all-in-one toolkit called Gato (Github Attack Toolkit) for finding and attacking repositories where these misconfigurations are present. We released the […]