How do you protect the confidentiality, integrity, and availability of systems and data in your organization’s growing cloud environments?
It starts by understanding your responsibility. Addressing security in a public cloud environment is slightly different than in your on-premises data centers. When you move systems and data to the cloud, security responsibilities become shared between your organization and the cloud service provider. Infrastructure as a Service (IaaS) providers, such as Amazon Web Services (AWS), are responsible for securing the underlying infrastructure that supports the cloud, and you are responsible for anything you put on the cloud or connect to the cloud.
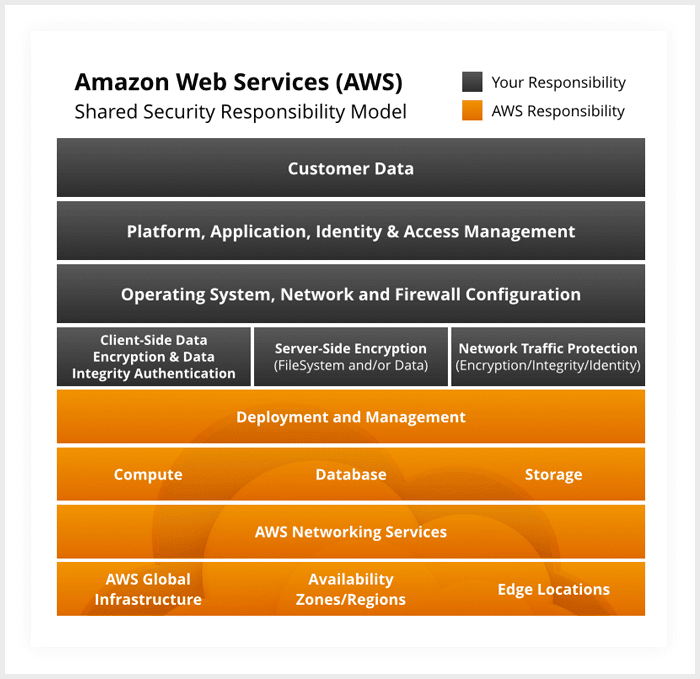
The following diagram outlines AWS’s shared security responsibility model. As you can see, there is a significant amount of responsibility that falls on the customer when it comes to ensuring the confidentiality, integrity, and availability of systems and data hosted within the cloud environment.
When operating in cloud environments, your organization assumes responsibility and management of all guest operating systems (including updates and security patches) and other associated application software, as well as the configuration of security group firewalls offered by cloud solution providers such as AWS.
Care must be taken when choosing which services you adopt within cloud environments, because your responsibilities vary depending on the services in use, the integration of those services into IT environments, and applicable laws and regulations. Enhancing security and/or meeting more stringent compliance requirements is possible by leveraging technology such as host-based firewalls, host-based intrusion detection/prevention, and encryption.
Managing Security in the Cloud
Understanding the separation of responsibility and control is needed to effectively direct your organization’s internal security, risk and compliance teams and external auditors. It’s still important to bring in independent third parties to conduct a comprehensive cloud security assessment on business critical applications and services hosted in any cloud environment. Cloud security assessments are designed to help your organization navigate through the unique security responsibilities associated with operating in today’s public cloud environments.
There are a number of motivations that drive organizations to conduct cloud security assessments, including internal due diligence, client requests, regulatory compliance, competitive advantages, or recent data breaches. The following are examples of specific areas of focus that may be included in a cloud security assessment.
CLOUD APPLICATION ASSESSMENTS
The overall goal of an application security assessment is to uncover software vulnerabilities, demonstrate the impact of weaknesses, and provide recommendations for mitigation. Our security engineers will provide a detailed and in-depth security analysis of your organization’s critical applications.
CLOUD INFRASTRUCTURE ASSESSMENTS
Praetorian engineers will remotely identify the networks, hosts, and services that comprise your cloud’s external and internal environments. Vulnerabilities are identified and if desired, exploited during a penetration test.
HOST/OS CONFIGURATION REVIEWS
Host reviews comprehensively identify security issues within your cloud environment. Praetorian engineers remotely review the configuration of key applications, servers, databases, and network components to identify vulnerabilities that may go unnoticed during network testing.
CLOUD ARCHITECTURE REVIEWS
A network architecture review will evaluate the function, placement, and gaps of existing security controls and compare their alignment with the organization’s security goals and objectives.
VPN SECURITY REVIEWS
The VPN review compares your current configuration against recommended best practices and identifies any areas of concern. The assessment includes a remote configuration review as well as an architecture review.
HOST-BASED FIREWALL REVIEWS
Analyze both the configuration of the host-based firewalls (accounts, logging, patch management, etc.) as well as the implementation of network security controls (ACLs) via the firewall.
It’s More than Cloud Security Best Practices
Organizational leaders responsible for managing cloud infrastructures need an accurate understanding of their security and risk posture, while ensuring compliance with industry regulators. It’s important to work with a trusted partner to help you navigate today’s shared security responsibility model in the cloud and help protect the confidentiality, integrity, and availability of systems and data in your organization’s growing cloud environments.
Is your cloud environment secure? Praetorian offers services designed to help protect the confidentiality, integrity, and availability of your organization’s systems and data in the cloud under a shared security responsibility model.
Learn more about Praetorian’s Cloud Security Services »