GitHub Device Code Phishing: From Research to Real-World Exploitation

webinar GitHub Device Code Phishing: From Research to Real-World Exploitation While security teams have focused on defending against Azure device code phishing, a new attack vector has emerged that’s flying under the radar. GitHub’s OAuth2 device flow represents an unexplored opportunity that our Red Team has weaponized with incredible effectiveness, achieving over 90% success rates […]
Chariot System Integrations
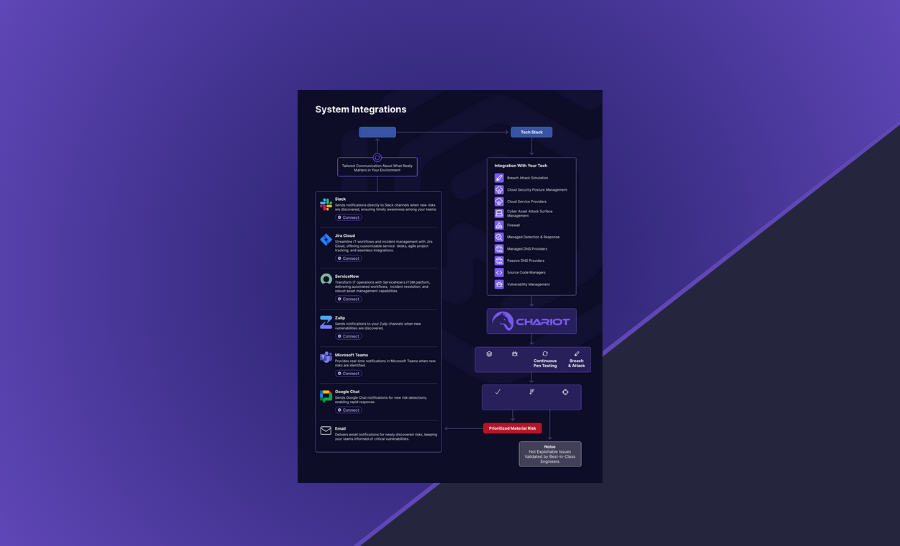
Chariot integrates with your technologies, systems, and security solutions and delivers prioritized, actionable security insights directly into your workflow.
Unpacking CodeQLEAKED: A Potential Supply Chain Attack on GitHub CodeQL
WEBINAR Unpacking CodeQLEAKED A Potential Supply Chain Attack on GitHub CodeQL Praetorian Red Team Security Engineer, John Stawinski, recently discovered a vulnerability in GitHub’s CodeQL where a token was exposed for just 1.022 seconds. In that brief window, he was able to demonstrate how an attacker could push code to the CodeQL Actions GitHub repository […]
CI/CD Security Assessment

Praetorian’s CI/CD security experts excel at discovering material risk. They turn seemingly benign vulnerabilities into real world attack paths, demonstrating how attackers or malicious insiders could execute large-scale internal or external supply chain attacks by exploiting your CI/CD pipelines.
The Hacker’s Mindset: Offensive Strategies to Enhance Defenses

webinar The Hacker’s Mindset: Offensive Strategies to Enhance Defenses In this webinar, Nathan Sportsman, CEO of Praetorian, and Howard Holton, COO of GigaOm, discuss the critical need for organizations to adopt a proactive offensive mindset to strengthen defensive security practices.
CTEM & Quantitative Risk Analysis

White Paper CTEM & Quantitative Risk Analysis Quantifying cyber risk has become a critical challenge for organizations seeking to justify their cybersecurity investments. Many struggle to translate qualitative threats into tangible metrics that resonate with decision-makers, often resulting in resource and budget allocation constraints. This eBook provides actionable insight for leaders looking to make data-driven […]
Prescribing CTEM: A Continuous Threat Exposure Management Training for Healthcare Orgs
TRAINING Prescribing CTEM Advances in Vuln Management for Healthcare Healthcare organizations have no shortage of risks to remediate. While they furiously chip away at their backlog, it winds up being busy work with no end in sight. A Continuous Threat Exposure Management (CTEM) program has incredible potential to revive struggling and inefficient risk management functions, […]
Continuous Threat Exposure Management (CTEM) and Cybersecurity Insurance

eBook Continuous Threat Exposure Management (CTEM) and Cybersecurity Insurance Securing and managing cyber insurance remains a top priority for enterprise organizations. However, the purchasing process can quickly become a minefield for businesses lacking process and security maturity. The result often leads to an excess of underwriter discretion and budget-gouging premiums. This eBook will explore some […]
A Blueprint to Continuous Threat Exposure Management

White Paper Continuous Threat Exposure Management Download PDF Start Free with ASM
Achieving PCI Compliance with Continuous Threat Exposure Management

eBook PCI Compliance and Continuous Threat Exposure Management Learn how to achieve PCI Compliance with CTEM Download PDF Start Free with ASM