If you are considering adopting a risk-rating framework, it is important to tailor a solution that best suits your organizational needs. The following risk rating scale was developed to satisfy the specific needs of our clients, and we hope it provides you with valuable guidance as you plan for the management of risk within your organization.
The purpose of most web application security assessments is to enumerate possible attack vectors, evaluate existing security controls, and provide recommendations for improvement. Effectively measuring the risk associated with identified vulnerabilities is one of the challenges associated with providing remediation plan recommendations to our clients. To address this challenge, our team employs a tailored risk rating framework as part of our comprehensive and methodical approach to assessing the security of web applications.
An objective risk rating framework enables our team to compare a standardized measurement of risk across an organization. It also allows our clients to prioritize steps needed in an action plan to mitigate, accept, or transfer organizational risk. Prioritization of vulnerability remediation should be organized objectively based on factors used in the risk rating framework, such as: ease of exploitation, severity of impact if exploited, and level of effort to remedy.
Praetorian’s Risk Rating Framework
Our risk rating scale is based on two widely used scales for rating security vulnerabilities, Common Vulnerability Scoring System (CVSS) 2.0 and Microsoft DREAD. We combined and tailored the best parts of these two rating scales into a new system that meets the specific needs of our clients. Our risk rating scale scores vulnerabilities and the associated risk against five independent risk factors, including:
- Access Vector (AV): The network location from which the attack originates.
- Attack Feasibility (AF): The extent to which the attack has been demonstrated or publicized.
- Authentication Requirements (Au): What credentials, if any, are needed for the attack to succeed.
- Compromise Impact (Ci): The extent to which the attacker can control the system in a successful attack.
- Business Value of Data (Bv): The type of data put at risk from the vulnerability.
If you want to learn more about these risk factors, contact us to explore our interactive sample reports.
Applying the Risk Ranking to a Vulnerability
Once a vulnerability has been discovered, we measure the five risk factors listed above and assign a value based on the risk severity definitions associated with each risk factor. If a specific measurement is not possible, our team estimates the value according to professional opinions given the specific real-world scenario. The five levels are then added with equal weight to form our complete 15-point risk rating scale. The totals for the risk factors are then used to classify a vulnerability into one of five final risk ratings, including: Critical (15), High (14), Medium (13), Low (10-12), and Informational (5-9).
For example, a web application that is found to not lock out a user who repeatedly enters the wrong password would qualify for a No Account Lockout Mechanism risk finding. This is considered a vulnerability because an attacker can mount automated dictionary and/or brute-force attacks against user and administrative accounts. When combined with a weak password policy and/or enumeration of user accounts, an attacker has a high probability of identifying a set of valid credentials. There is clear risk associated with this vulnerability, and assessing each of the five risk factors will help us better define the severity of risk associated with this vulnerability.
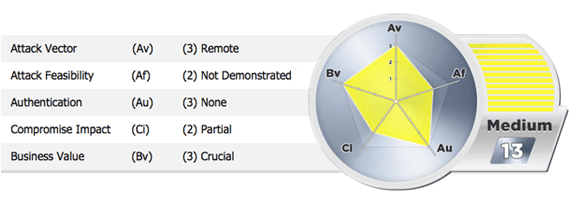
Let’s go through the process of measuring each risk factor for this specific finding:
The first risk factor, Attack Vector, would be given a value of (3) because an attack could potentially be executed from any computer, anywhere. Attack Feasibility could be assigned a score of (2) given that the attack was not carried out, but a demonstration would be possible given particular resources. The third risk factor, Authentication Requirements (Au), would qualify for a value of (2) due to the fact that credentials from any user account would be sufficient to execute the attack. Compromise Impact (Ci) could carry a score of (2) because only a partial compromise of the system’s confidentiality, integrity, and/or availability would be affected. And finally, the Business Value of Data (Bv) factor would be deemed (3) crucial because exploiting this vulnerability could have lead to a breach of personal health information (PHI), sensitive personal information (SPI), credit card information or other financial data. In this specific case, the final assessment results in a risk rating of Medium (13) for this vulnerability given the values prescribed to each of the five risk factors.
For the curious, the final recommendation for remediation is to implement an account lockout mechanism that locks after five failed authentication attempts. The lock out mechanism could either reset automatically after a period of time (soft lockout) or require administrator intervention to be unlocked (hard lockout).
You’ve Measured Risk. Now what?
When addressing risk-related issues it is important to prioritize issues with the highest level of risk and lowest cost of remediation followed by issues that are less critical, or more difficult to address. When determining “cost”, it is also important to consider other areas of the business that may be impacted during a fix. The total cost of remediation should take in to account both the costs associated with resolving the issue as well as the broader impact on your business operations and customer experience. This is best illustrated in the following example:
We would generally classify the no account lockout mechanism risk finding that was detailed above as a medium risk issue and associate a medium cost to remediate. However, the business impact of correcting the issue could potentially be very high because many applications, which implement an account lockout mechanism, will require additional support staff to deal with the user reset. In addition, the business owners could face blowback from a portion of the user-base that believes the security control is burdensome – hence this remediation would constitute a high level of business impact.
The Business Impact Matrix in our sample report provides further insight into the relationship between relative risk, remediation cost, and potential impact on business operations and customer experience.
Final Thoughts
An application security assessment provides value by enumerating possible attack vectors, evaluating existing security controls, and providing recommendations for improvement. Employing an objective risk rating framework, based on standard principles, to manage risk associated with identified vulnerabilities will provide a step-by-step roadmap for remediation. Through this, your organization will effectively manage the risk associated with security vulnerabilities, while complying with industry standards and information security best practices.
