Do you suspect some pins on your device are JTAG? There are several methods out there for identifying if pins are likely to be JTAG or not. One of those methods involves buying a $200 JTAGulator, however there is a cheaper Arduino-based alternative I will be detailing in this post. First I’ll explore the expensive way.
Learn more: Why are JTAG and UART still effective attack vectors for IoT devices?
The JTAGulator
The JTAGulator is able to quickly identify which pins are likely to be JTAG and figure out the ordering of those pins. To demonstrate this, I connected the JTAGulator to an Arduino Zero’s JTAG pins to see if it can correctly identify which pins are which. Because the Arduino Zero is open source, we can check the hardware schematic to verify our results.
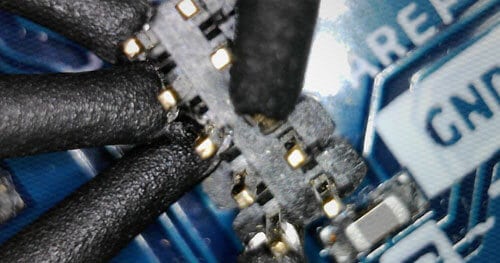
Below is an image of my probes connecting to the pins on the Arduino Zero. These pins required a smaller gauge wire than typical breadboard pins, so I used the probes instead of wire connects.
The order of these pins doesn’t matter, because the JTAGulator will figure out which is which. The one thing that does matter however, is making sure the device and the JTAGulator share a common ground. For this reason ground should be identified using a multimeter and connected before applying power to either system.
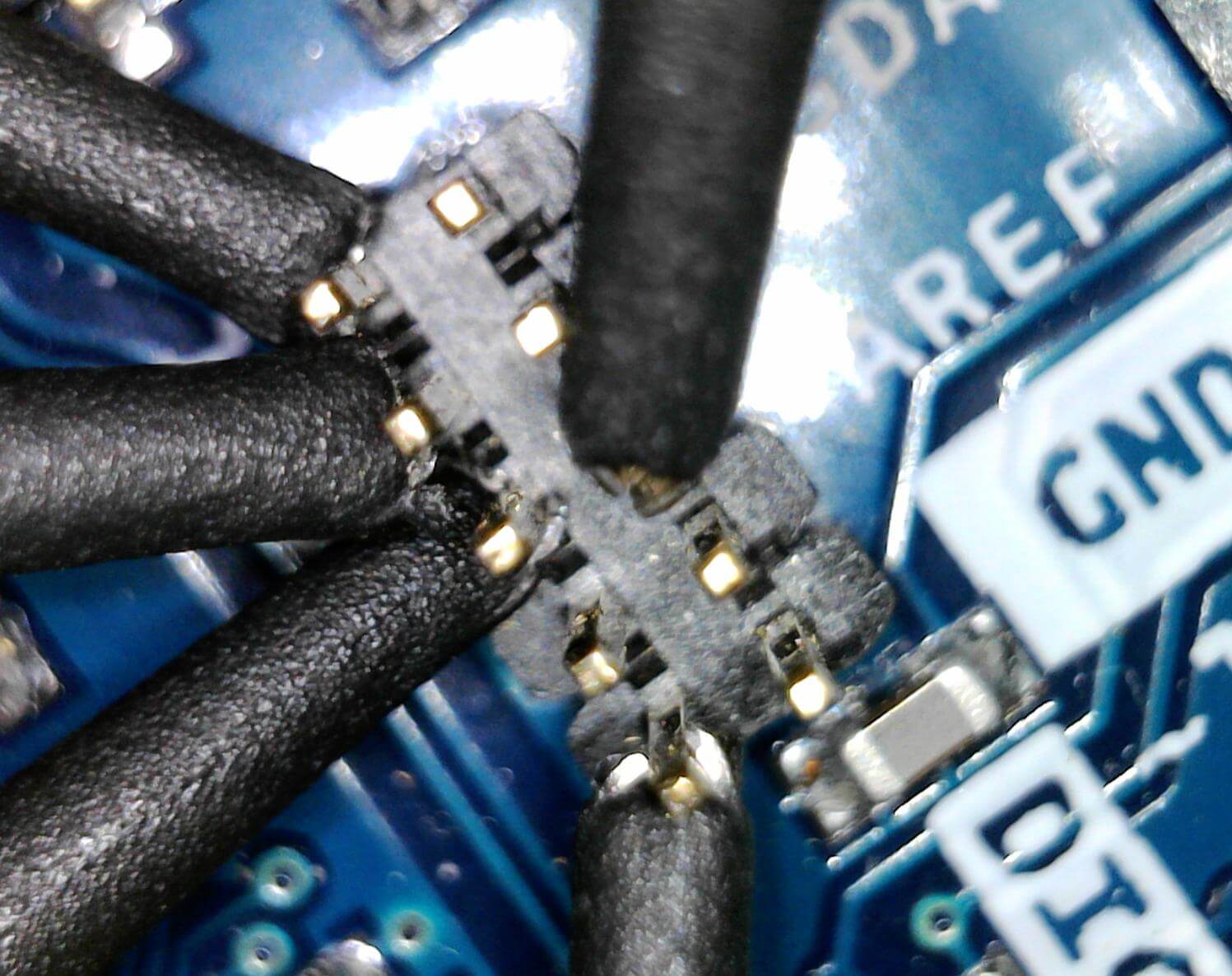
Below is an image showing all the connections from the device to the JTAGulator.
Once connected, I plugged in the JTAGulator into my USB port, and used screen to talk to it. The baud rate is 115200 and in my case the device showed up as /dev/tty.usbserial-A603WYPG. You may have to check /dev/ with the JTAGulator unplugged, and then plugged in and do a diff to identify which device is the JTAGulator.
The full command is shown below:
$ screen /dev/tty.usbserial-A603WYPG 115200
Once connected successfully, the following output will show the JTAGulator correctly identifying the pinout of the JTAG pins using a method called “bypass enumeration”.
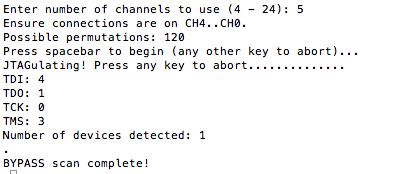
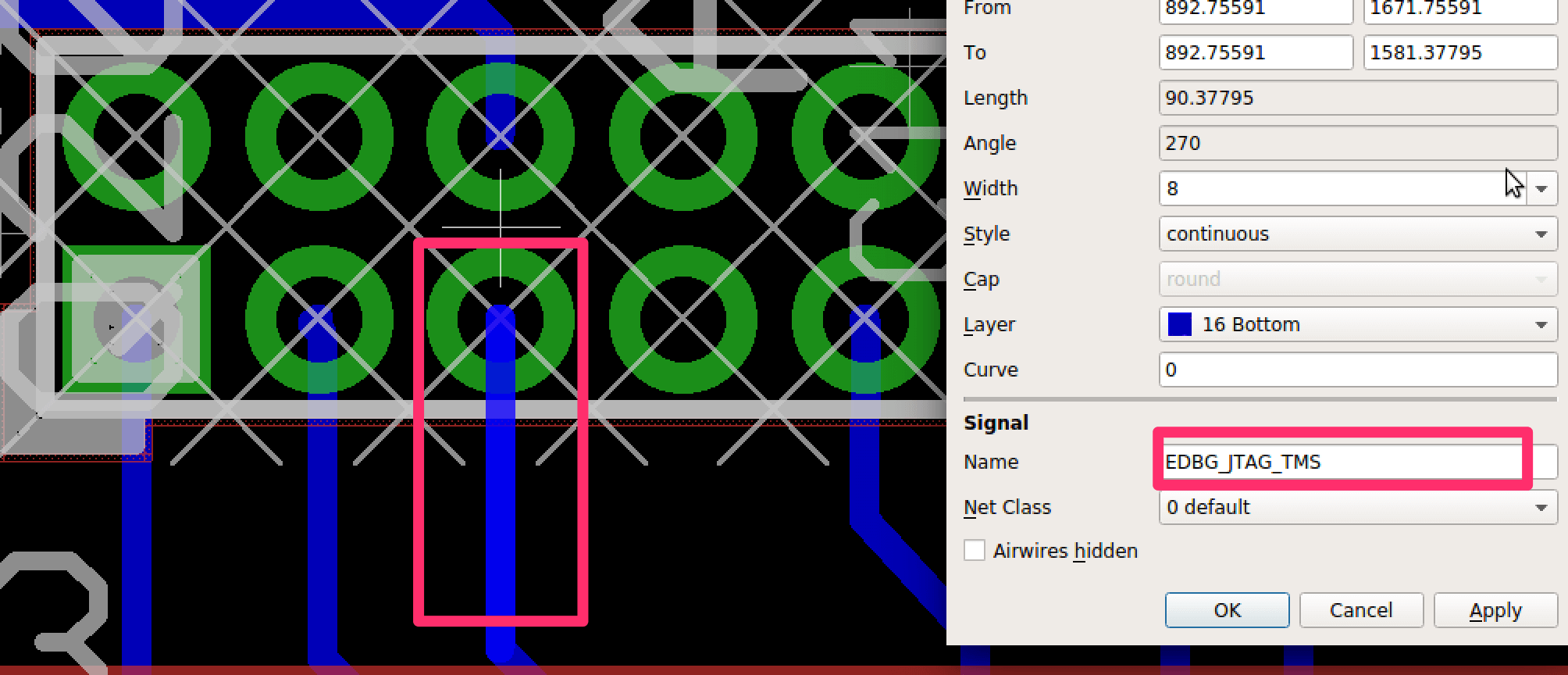
These pins where then verified against the board design shown below:
From this I was able to confirm the JTAGulator did in fact correctly identify the JTAG pinout.
But what if you don’t have $200 to spend on a JTAGulator? When going through the JTAGulator source code it became clear some of the functionality was borrowed from an Arduino project. Let’s explore that next.
JTAGenum
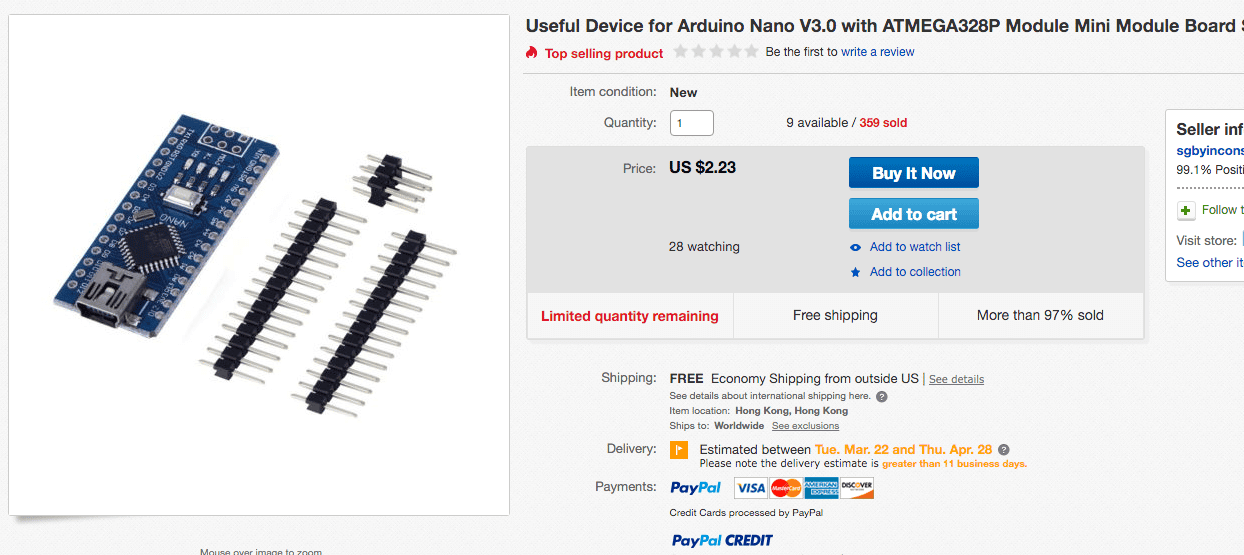
JTAGenum is an Arduino based project which can identify JTAG pins and correctly order them. Arduinos have gotten cheaper and cheaper over time to the point where at the time of writing this blog post the cost to ship one to my door is less than $3.
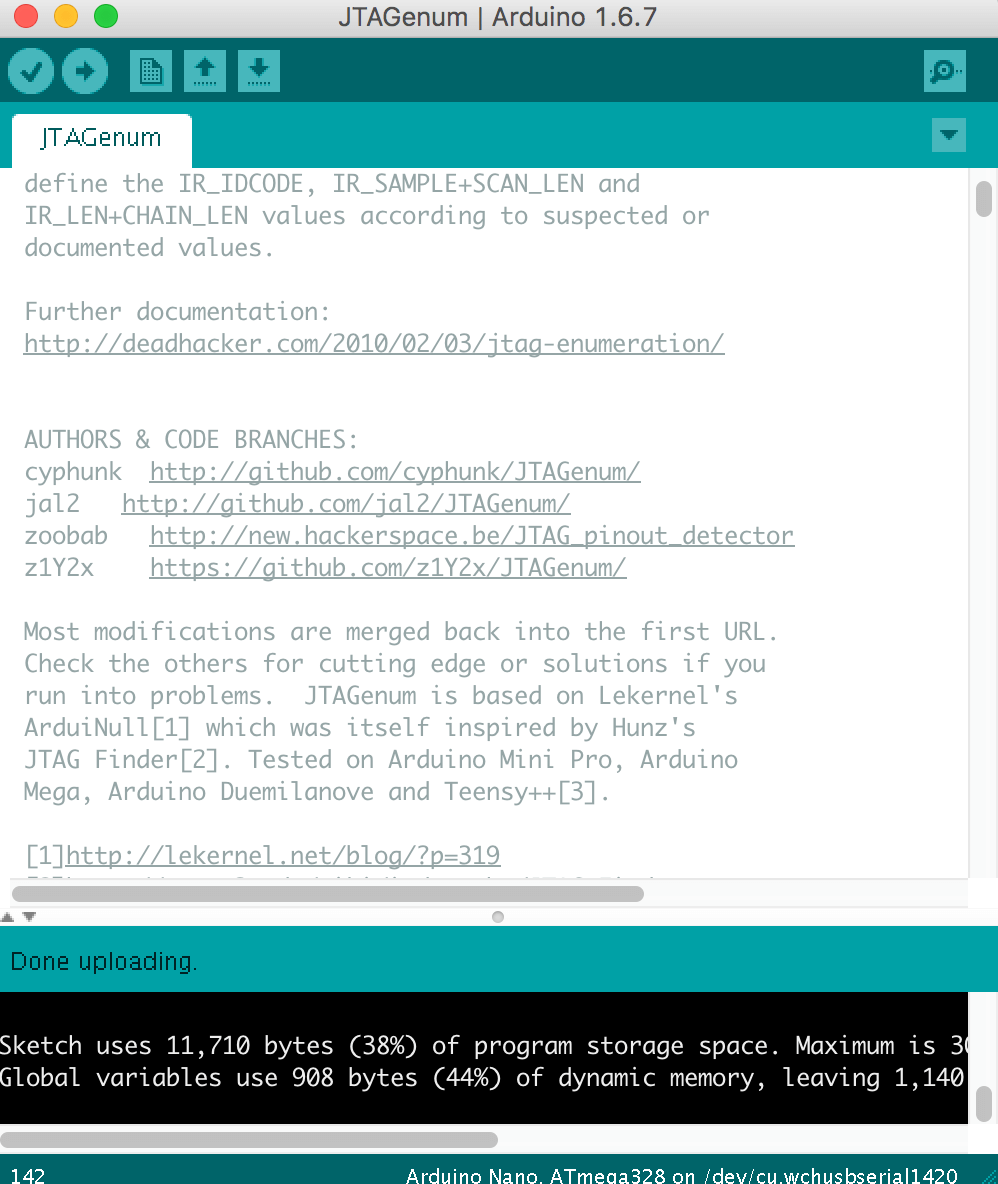
I was able to successfully load up the INO code from JTAGenum in the Arduino IDE and push it to the Arduino Nano.
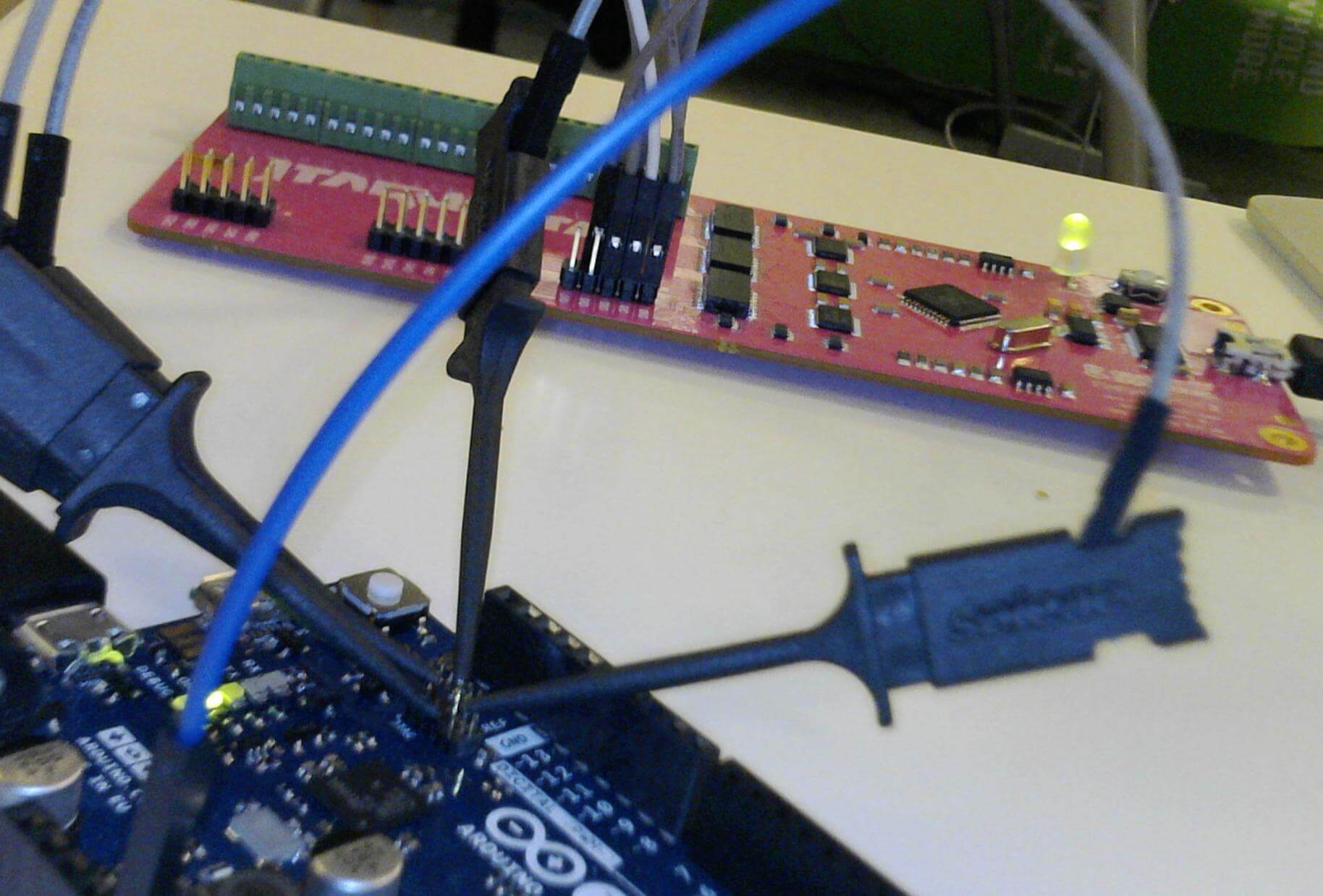
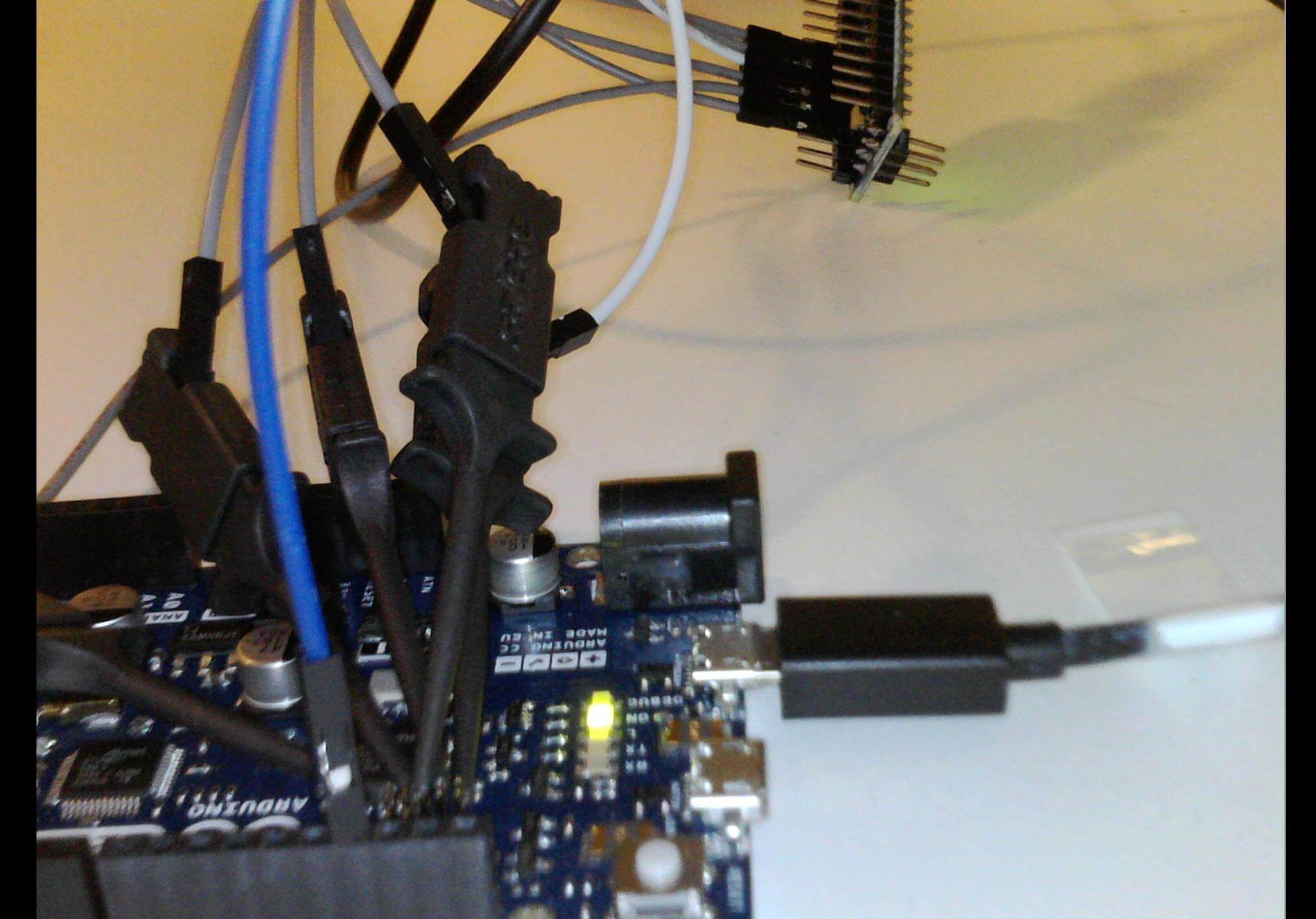
and after connecting ground on the Arduino and the test device, and hooking up digital pins 2-6…
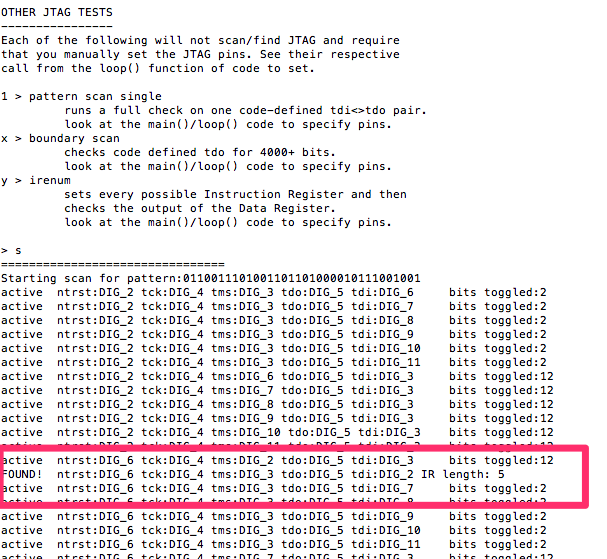
I was able to open up a serial window in Arduino (though screen would also work again) and run JTAGenum. Again, I could correctly verify the pins where correct, using the open hardware schematics.
The DIG in the output stands for digital pin, which correlates to the digital pin numbers printed on the Arduino. These pin numbers are different from the JTAGulator’s output because when I connected the wires, the order I connected them was not the same.
So there it is, identifying pins as JTAG and determining their pin order, for less than $3.
Comparing options
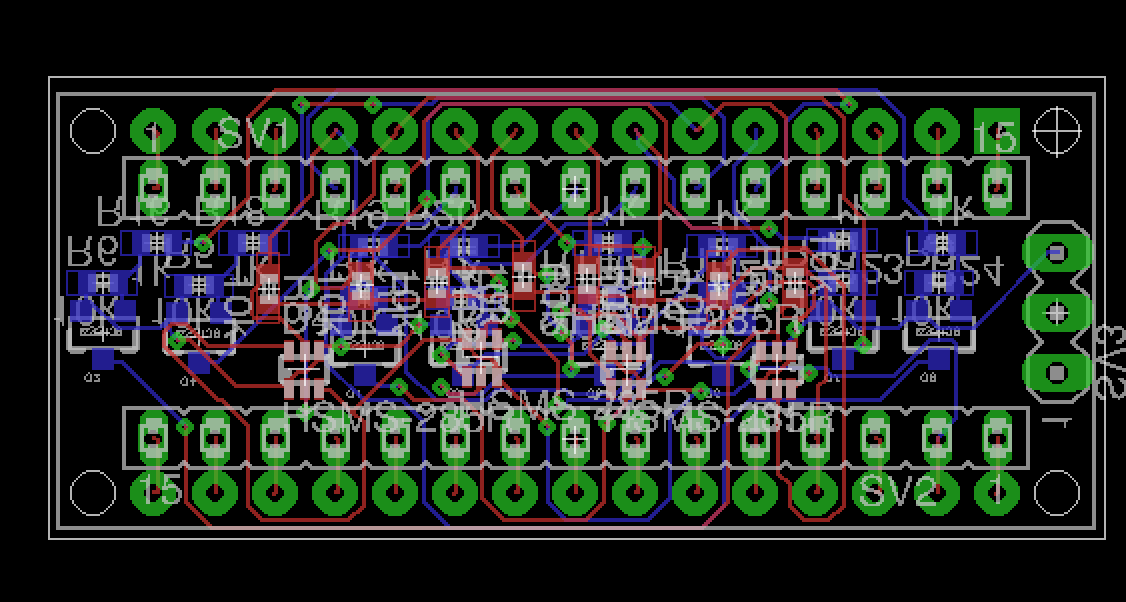
What are some other differences between the two options? As far as hardware differences go the JTAGulator has built in level conversion and input protection. This is why I am releasing a shield for the Arduino which provides the exact same capabilities. The open hardware designs for the shield are available here: https://github.com/dxa4481/inputProtectionShield
As far as software goes, the JTAGulator offers UART scanning capabilities as well, which currently the JTAGenum library does not. The JTAGenum library does however offer functionality to scan for undocumented JTAG functions, which is something the JTAGulator platform does not currently offer.