Praetorian is powered by an engineering culture. If a new solution is needed to solve a unique problem, we build it.
The value we provide stems directly from our engineering culture – a relentless pursuit of efficiency and continuous improvement in all operations. Much of that value is on display during engagements through our proprietary methodologies, industry leading toolsets, and comprehensive deliverables. Examples from our custom toolsets range from proprietary payloads, to innovative penetration testing frameworks, to our iPentest Device™, which is a custom plug-and-play technology that minimizes logistics and travel costs for clients by allowing our engineers to perform onsite work remotely.
These operational efficiencies allow us to pass on cost-savings and deliver higher value to our client. Today, I’d like to share a small utility called Highlight with you that demonstrates the lengths we go in our relentless pursuit to find new efficiencies through automation and continuous innovation.
Download Code: Highlighter on GitHub →
Highlight is a simple utility that creates an image from a text stream, automatically draw boxes around user defined content and automatically blurs sensitive content.
Sometimes we have a text stream, such as the output of a configuration file, and we want to include that as an image into a document. At the same time, we might want to highlight a particular string of text that’s found and we might want to hide other details that might contain things such as passwords. We could use a screen capture utility and then proceed with marking up the image. This leads to inconsistent boxes around text and certainly does not lend itself to automation.
With this utility, the entire process can be automated.
Why Build Highlight?
When we tell our customers about problems in their network, we need to provide some proof, often in the form of screenshots of captured data. The critical item might be something simple such as allowing a 40-bit export-grade crypto key for authentication of an https session. Certainly a nice tool such as sslscan will find this without issue. There is often plenty of other data that’s in the output and is needed for context and it’s not always easy to see the data that’s important. So when we get a screenshot, we need to draw a red box around the offending content to draw our customer’s eye to it.
In reality, such a step takes only a couple of minutes, but such things add up over time. It’s drudgery. Automated scanning can find plenty of issues which need to be fixed, such as being susceptible to POODLE or even Heartbleed. Pretty soon a large chunk of the day is spent taking screenshots and marking them up. And there’s a hidden cost: By spending time doing something trivial, we aren’t doing the hyper-creative work. It’s madness and it stops today.
Announcing “highlight“, a program that will draw those boxes for you. Simply pipe in text content and what you want highlighted and the program will generate a light-green text on a black background and draw red boxes around the chosen content. Nearby boxes are combined together in a reasonable fashion.
cat types.h | highlight -o output.bmp -i trace
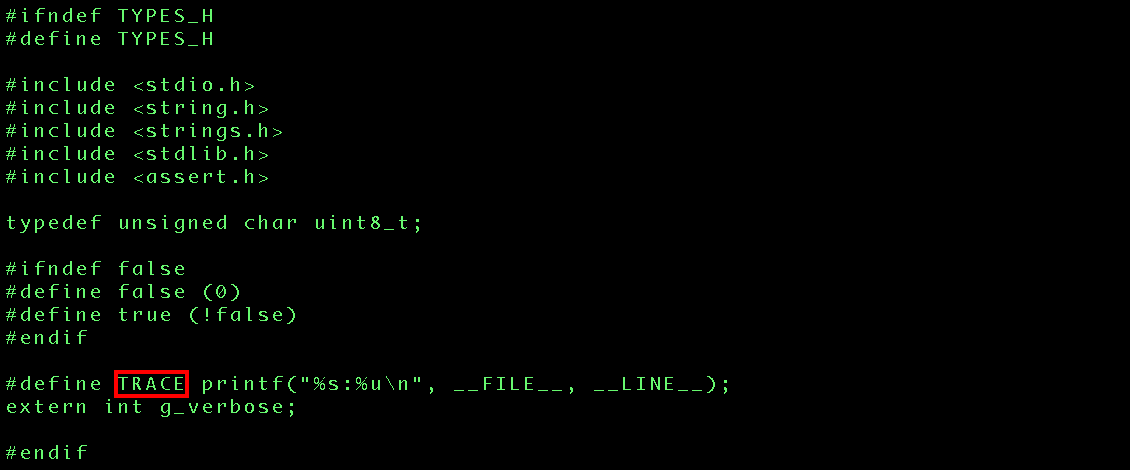
Perhaps you want to change the colors? That’s done via the command line for the foreground, background and box color. You can get fancy and specify the full RGB components. The image will have a thin black line around it as well, which is great for reports that have a white background.
With this alone, it would be a very useful utility. But there’s another really cool feature and that’s the blurring capability. When we capture a customer’s NT hashes, for example, we want to show them in the report as proof, but we don’t really want to disclose the contents. After all, we are in the business of protecting our customers from the bad guys. So, this utility has an additional ‘blur’ feature which takes all the characters below and to the right and changes them to a fuzzy character. In a report, we can show the user names in full and even the first few characters of the password hash. It’s enough that the system administrator can verify that we got the right content, but not enough for a hacker to use, even if they got the report.
ps | highlight -o output_full.bmp -d 120x30 -b white -f c0ffee -x blue -i -r CMD ttys003

Although automated scanning has been around for a while, it’s the reporting of the flaws that takes much of the time. Now, we have the ability to generate the entire content of a flaw without any human intervention. Those extra few minutes add up and allow us to spend more time for a customer on a new flaw, or to come up with new tech challenges on our website, or to provide new tools for the community.
The output image is a compressed BMP file, which can then be converted to your format of choice. It’s all written in C and you don’t need to install 3rd party packages to make it work. Simply copy it from our GitHub repo, and make install.
P.S. If your password is “Spring2016” or “Spring2016!”, you aren’t fooling anyone. Get a password manager such as 1Password or LastPass which can generate strong passwords for you.