Special thanks to Kesten Broughton (Lead Security Engineer) and Vikul Khosla (Cloud Architect) for their significant contributions to this article. See Kesten’s recent talk at fwd:cloudsec 2020 here.
Overview
In today’s multi-cloud world, finding the best resources to secure your environment can be difficult. Popular security frameworks and benchmarks such as the Center for Internet Security (CIS) Cloud Benchmarks, the AWS Well-Architected Framework, and the Azure Security Benchmarks (ASB) all have various applicability to different cloud environments. To simplify assessment of multi-cloud environments across a broad client base, Praetorian created an 8-pillar framework (see graphic below) that guides our work. Coupling these pillars with Praetorian’s proven methodologies for enterprise and product security provides a holistic approach to securing organizations from chip to cloud.
This article examines five of the eight pillars, identified in color below, to highlight the unique assessment aspects that the pillars bring to cloud security architecture assessments.
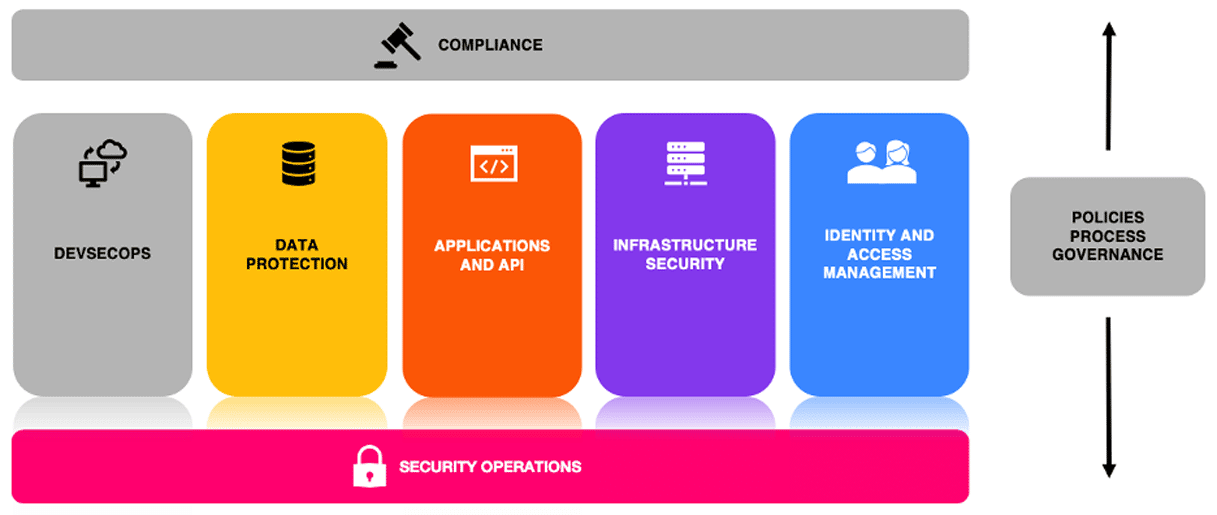
Development of the Pillars
Following industry trends, Praetorian chose CIS, Well-Architected, and ASB to guide the assessment pillars due to the combined breadth of their coverage and their industry adoption. Breaking down the constituent components of each framework and benchmark, we were able to establish patterns and themes that we were further able to distill into the pillars pictured above.
The result of this process is a mapping of Praetorian’s Pillars (and subsequent tracks described below) to these frameworks and benchmarks that ensures broad coverage of security controls and best practices across various cloud providers, implementations, and services. Adding in the considerations of DevSecOps and Compliance, Policies, Process, and Governance as tangential considerations rounds out the model to ensure an end-to-end picture of an organization’s cloud ecosystem and cloud security architecture. The resultant Pillars and Tracks are outlined below:
Data Protection
- Protect Data
- Key Management
- Policy and Governance
Applications and Application Programming Interfaces (APIs)
- APIs
- Micro-Services
- Containers
- Serverless
- Mobile
- Email and Web Browser
Infrastructure Security
- Virtual Private Cloud (VPC)
- Compute
- Inventory Management
- Policy and Governance
Identity and Access Management
- Identity
- Authentication
- Authorization
- Policy and Governance
Security Operations
- Controls
- Logging Monitoring Alerts
- Incident Response
- Policy and Governance
Pillar Definitions
Data Protection
This pillar focuses on the security of data at rest and data in transit. With various data storage capabilities within cloud environments with support for file, block, log, and other storage, the security of these stores is of utmost importance. The variance in mechanisms to transmit data within and through the cloud environment necessitates specific analysis of the security utilized for these transmissions and the handoff between different service types (micro and macro services). Key management can also be a significant part of the security landscape; even more so in areas that cannot make use of built-in mechanisms due to regulatory requirements.
Applications and APIs
Often the core of a cloud environment is the application or service that it provides. APIs, web applications, and mobile applications all have common assessment
models in traditional contexts, but layering on micro-services and serverless technologies can introduce security considerations that may not be identified during normal application penetration tests. A common sales platitude is that micro-services and serverless architectures are immune to security issues. Although the security issues are vastly different than what we have become accustomed to, they still exist nonetheless.
Infrastructure Security
The most traditional of the pillars, Infrastructure Security is akin to traditional network security. This pillar assesses the technical controls that secure the VPC, the actual cloud computing resources, and the accounting of what assets are actually included in the cloud environment. While the scope of this pillar is much more traditional, the assessment is anything but traditional. The security controls for VPCs and compute resources and the concept of an “asset” in a cloud environment are nebulous concepts that require unique considerations in order to be assessed effectively. In one case, Praetorian worked with a customer who had strong IAM policies and implementations including a hub-and-spoke architecture and separate accounts for distinct workloads. However, due to their implementation of VPC peering, they had effectively joined their entire cloud environments into a flat network. Praetorian worked with the customer to develop a plan to sample traffic, develop NACLs, improve artifact and data publishing, and implemented VPC Transit Gateways to avoid the need for VPC peering everywhere.
Identity and Access Management
Web interface, command line, inter-service, intra-service, third-party access…the list goes on. IAM in cloud environments is complicated to say the least. Gone are the days of simply having user groups with specific access to tools and platforms. The adoption of cloud services has ushered in a new era of fine-grained access control with hundreds of potential access considerations across many different organizational units. Develops, administrators, networking, infrastructure, automation, security…all will have different access requirements. Managing hundreds of potential access options, across a large organization, while integrating third party tools, and deploying product on schedule is a recipe for chaos. Proper management of the IAM ecosystem requires a thorough understanding of the technologies and deployments at play. An example case where Praetorian was able to utilize this pillar for significant impact when a customer had just completed a major migration to Okta for SSO access to AWS for UI access. They were left with no good way to offer CLI access to developers which slowed efforts to implement an infrastructure-as-code (IaC) rollout. Praetorian worked with the customer to vet solutions to deliver a smooth SSO to CLI users and enable the IaC rollout.
Security Operations
While the assessment of the pillars above can help to improve the security posture of an organization’s cloud environment, those improvements only address “current state.” To achieve continuous security, proper controls, monitoring, and response actions must be in place. These considerations can be very similar between on-prem and cloud-based resources, but anecdotal evidence suggests that this is rarely the case. Proper ingestion of logs, consistent application of controls, and defined incident response procedures often break down
in cloud environments due to either technical limitations or lack of planning or consideration. This pillar assesses whether security operations for cloud environments are adequate given the organization’s risk tolerance.
By aggregating and distilling the various security architecture benchmarks and frameworks, we ensure comprehensive coverage of security principles in a manner that is agnostic to cloud provider or implementation. This broad applicability and coverage goes beyond traditional scanning tools that only check for vulnerabilities in software or weak configuration settings within the cloud management plane. Many severe weaknesses arise from issues that a scanner cannot detect, such as:
- Architectural decisions
- Gaps in defense-in-depth
- Insufficient privileged access management (specifically for third-parties)
- Insufficient authentication between microservices
- Shortcomings in PKI implementations
- Gaps in logging of security-relevant events
- Identity management including authoritative IdP
- Authentication and Authorization mechanisms including role delegation
- IAM policies, access controls, and governance
- Cross account access policies, third party access, ABAC and Organizational policies if applicable
- Detailed assessment of all VPC resources including their configuration and protection mechanisms
- Network segmentation architecture
- High availability, Elasticity and Network Resiliency
- Multi account, VPC sharing architecture and protection mechanisms
- Detailed assessment of compute resources including hardening, configuration, attack surface and protection mechanisms
- Cloud inventory management and gitops if applicable
- Data protection mechanisms
- Key management
- Backup and recovery mechanisms
- Detailed assessment of Security Operations: Anomaly IDS, Vulnerability management, SIEM, SOAR, Logging, Alerting, Cross account strategies, Policies and Governance
- Architectural patterns, API Management and Protection, Telemetry mechanisms
- Detailed assessment of Kubernetes deployment if applicable
Often architectural and design deficiencies have far reaching implications that make remediation difficult or costly. Praetorian seeks to identify these issues early in the environment’s lifecycle and provide recommendations that will pay dividends in reduced technical debt down the road.

