The current SQLmap plugin release for Burp Suite of has one major shortcoming — it was not written with the intent of being run in a Windows environment.
Burp Suite provides a very basic SDK known as Burp Extender. Burp Extender allows third parties to extend the features of an already powerful web application testing suite. In March of this year, Daniel Garcia (cr0hn) created a SQLmap plugin for Burp using the Burp Extender SDK. With Daniel’s SQLmap plugin, automated SQL injection discovery and exploitation is now seamless between two of our favorite web application pentesting tools.
The current SQLmap plugin release for Burp Suite of has one major shortcoming — it was not written with the intent of being run in a Windows environment. While people have come up with workarounds, nobody to date has modified the SQLmap plugin code to work seamlessly with Windows — until now.
The Problem:
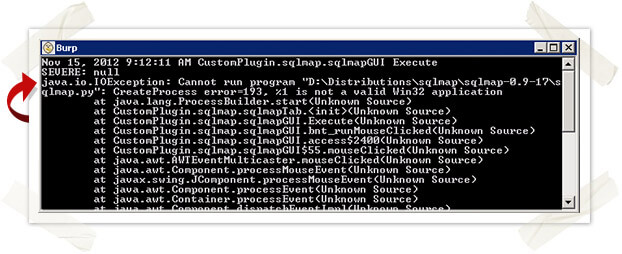
Given that Linux is the preferred platform of most penetration testers, default path and script execution values assume the tool will be run in Linux. Unfortunately, attempting to directly execute sqlmap.py without invoking the interpreter will result in an exception on Windows. The screenshot below shows the I/O exception that will be thrown when the Windows CreateProcess() function attempts to execute the python script.
The Solution:
The Windows portability issue has been known for several months and the original bug submission can be found here. To date, this is the only outstanding defect for the plugin and it is currently rated a medium. While the person reporting the issue was not able to modify the code to fix the problem, they did come up with a workaround. In Windows, rather than calling the python script directly, you can call the python script indirectly through a Windows bat file. Although this works, it is not the cleanest solution. Since our services organization leverages both Linux and Windows, I decided to spend a few minutes (this post took longer to write than it took to update the code) porting the code to Windows. I also made a few cosmetic tweaks to field and label sizes while making the updates.
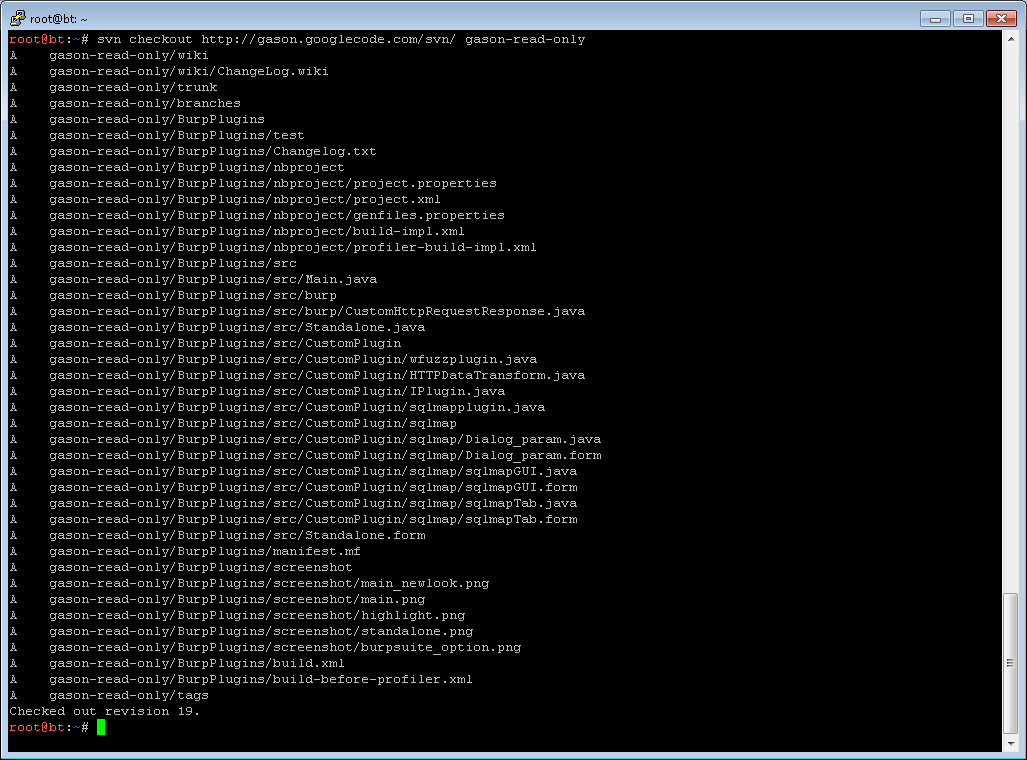
The code base is relatively small, but the SVN repository the author created does not appear to include all the java files necessary to build and run the integrated plugin. The graphic to the right shows the files retrieved from the googlecode SVN repository.
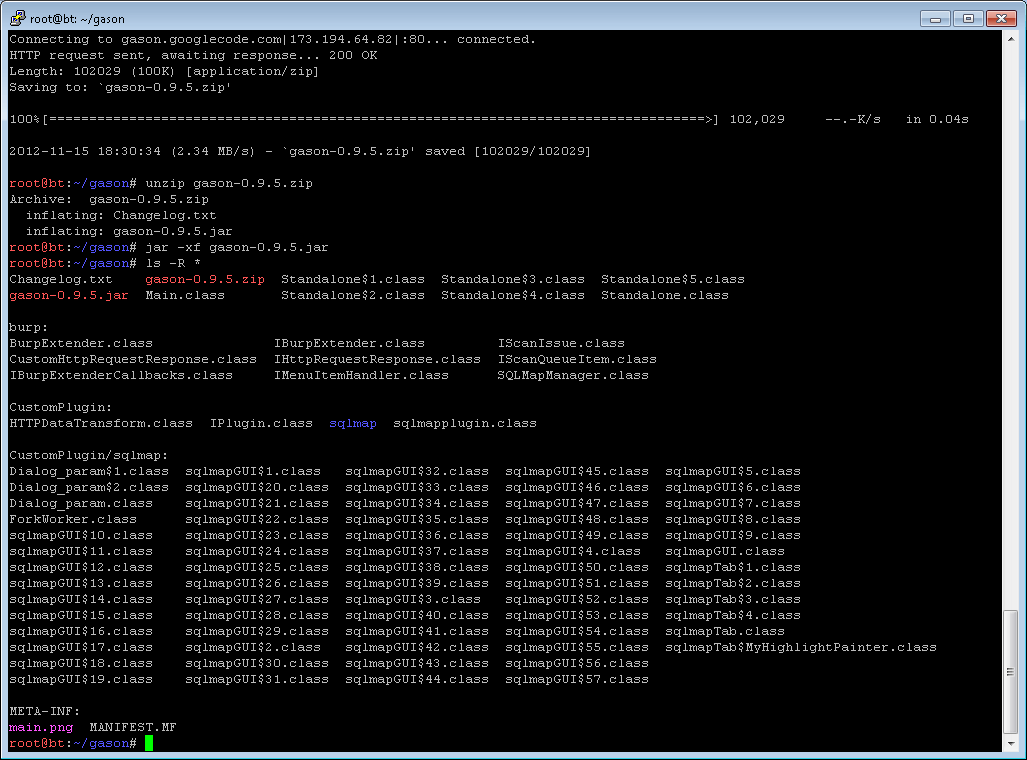
The missing java/class file became apparent when comparing our jar file size to the size of the current jar file available for download (and the fact our integrated plugin did not work).
We obtained the omitted code by extracting the missing classes from the plugin’s latest jar file that is available for download. We did not need the associated java files because our updates were being made elsewhere in the code.
Code Modification:
After a few minor tweaks to sqlmapGUI.java, file paths and execution decisions are now determined by the underlying OS. Relevant code changes are shown below.
Code changes tagged with “nathan sportsman” in comments
private ArrayList tabs = new ArrayList(20);/* default sqlmap path value for Unix */private static String command = "/usr/bin/sqlmap";/* Obtain operating system info for multi platform support - nathan sportsman */private static String OS = System.getProperty("os.name");public sqlmapGUI(){initComponents();this.getRootPane().setDefaultButton(this.bnt_run);this.setLocationRelativeTo(null);this.setVisible(false);// Adjust the default sqlmap path if underlying OS is Windows - nathan sportsmanif(sqlmapGUI.OS.startsWith("Windows"))sqlmapGUI.command = "C:sqlmapsqlmap.py";}public void AddURL(IHttpRequestResponse URLs_) throws Exception{if(URLs_ != null && URLs_.getUrl().toString() != null){
/* Windows CreateProcess() cannot call the python script directly. For Windows, we need to append python.exe to the command string - nathan sportsman */if(sqlmapGUI.OS.startsWith("Windows"))l_params.add("python.exe");l_params.add(txt_bin.getText());String m_url = url;l_params.add(l_action[cmb_action.getSelectedIndex()]);
Use the new plugin:
The source code was rebuilt and archived into a new jar file (contact Praetorian if you are interested in a copy). We kept the same naming convention as the original author who revved the minor release. To use the plugin, you will need to run a command similar to the following:
C:WINDOWSsystem32java.exe -Xmx500m -classpath "C:Burpburpsuite_pro_v1.5.jar;C:Burpgason-0.9.6.jar" burp.StartBurp
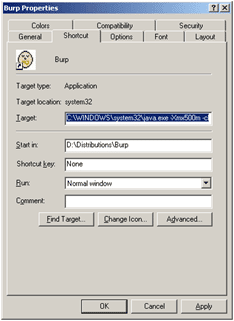
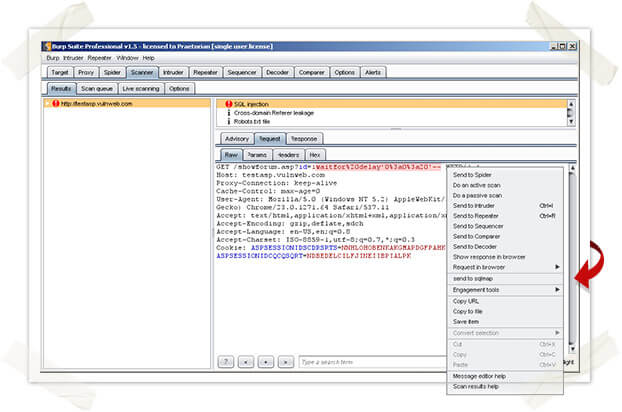
You can also edit the properties of your Burp shortcut and modify the Target variable as shown in the picture to the right. The plugin code will be called when Burp is launched. When Burp identifies that a parameter is vulnerable to SQL injection, send the specific request that triggered the result to the SQLmap plugin. This can be performed by right clicking in the request area and selecting the “send to sqlmap” action as shown in the screenshot below.
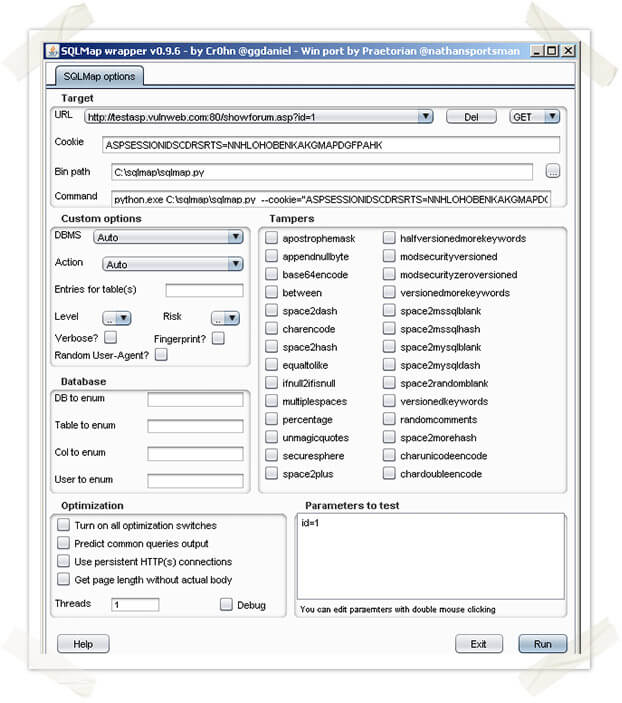
Daniel has created a GUI interface for sqlmap’s command lines options. As before, set the appropriate SQLmap options and click “Run”.
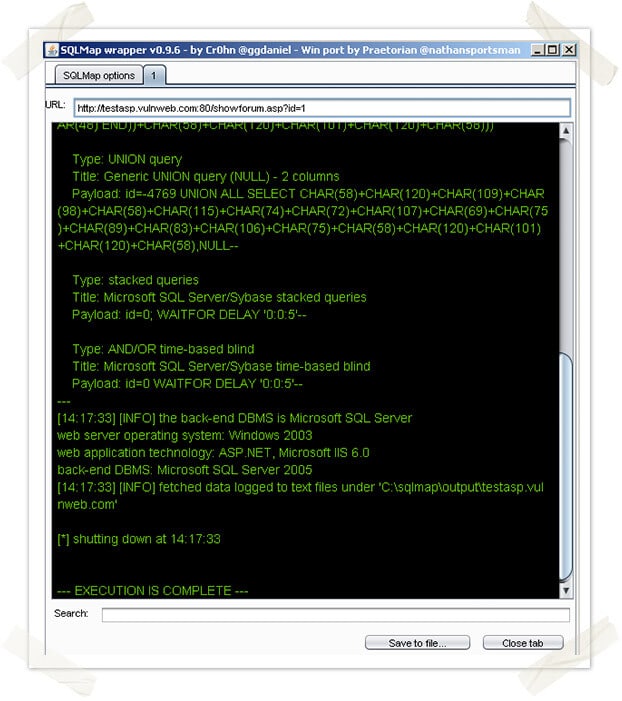
A child process for SQLmap will be created and run in a new tab as shown in the screenshot above. The script will output its execution in the new tab window. In the screenshot below, the plugin is used to enumerate the underlying database technology. Contact Praetorian for the ported plugin.