Tools for next generation phishing
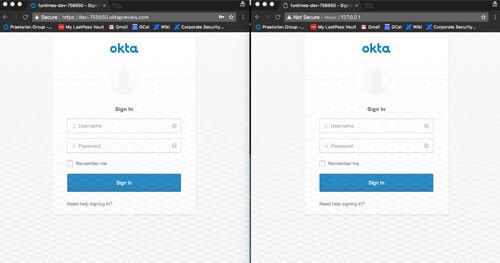
During my internship with Praetorian, I was able to create a new tool—Okta Watering Hole—that was used on some of the red team engagements. I created this tool because our team ran into the issue of not being able to get past two factor authentication on various web portals—so this is how we got around that. Okta Watering Hole sets up a carbon copy of a target Okta site and begins to capture credentials and sessions of visitors. This can be used to check how a company’s procedures and policies stand up to the “next generation” phishing attacks we are beginning to see. This new tool supports traditional phishing attacks as well as targeting two factor authentication devices—meaning perimeter security has to work double time.
My goal in creating this tool was to empower security teams to create advanced phishing exercises that can test users on a variety of possible threats. After the exercises, security teams could update policies, procedures, and training to improve the organization’s security posture against new phishing attacks. Secondly, it can be used by red teams to quickly ramp up and get access to internal environments quickly and efficiently. With these new abilities both blue and red teams will be able to spend more time preparing for actual attacks, and less time preparing for the exercise.
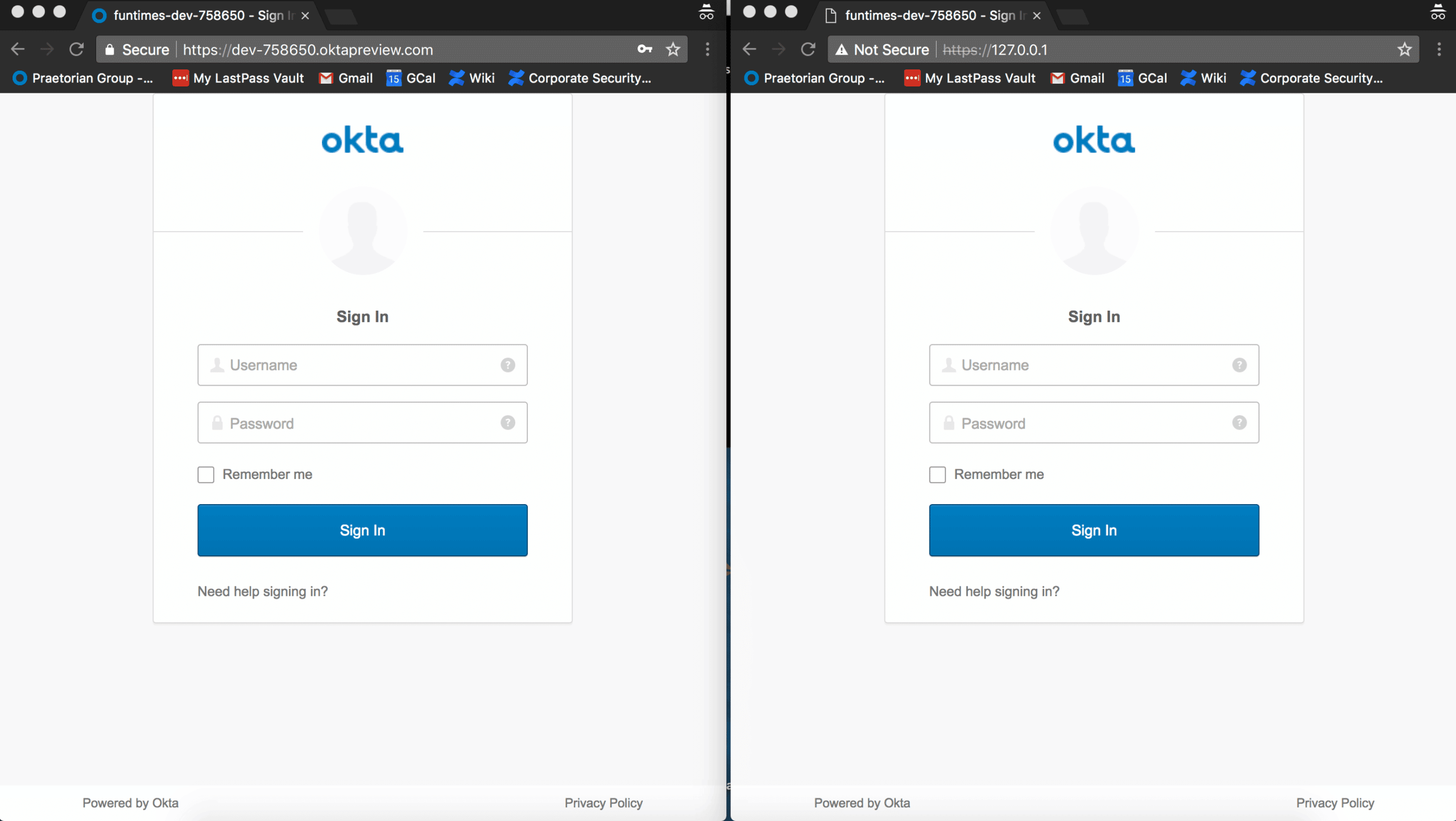
Setup
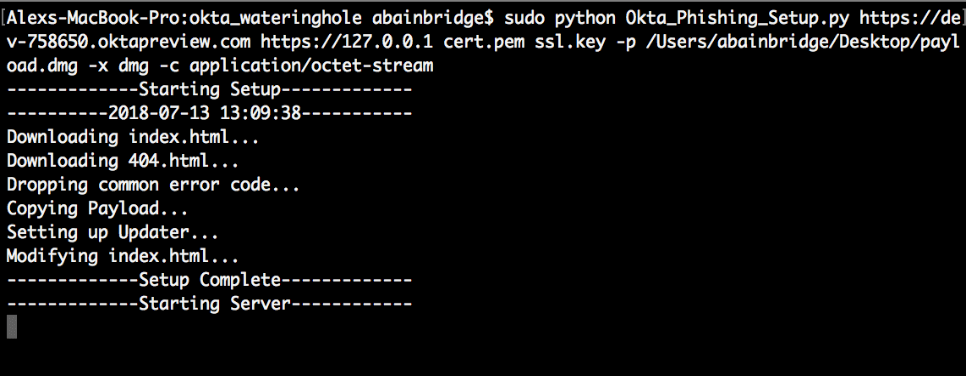
The new tool comes as a Python setup script and just requires you to select the target and host and then specify where the SSL cert is located. All of the necessary information is then downloaded/created and two servers are started—one for phishing and one for results. Additional options such as payload distribution, Gophish tracking, and logging are also available.
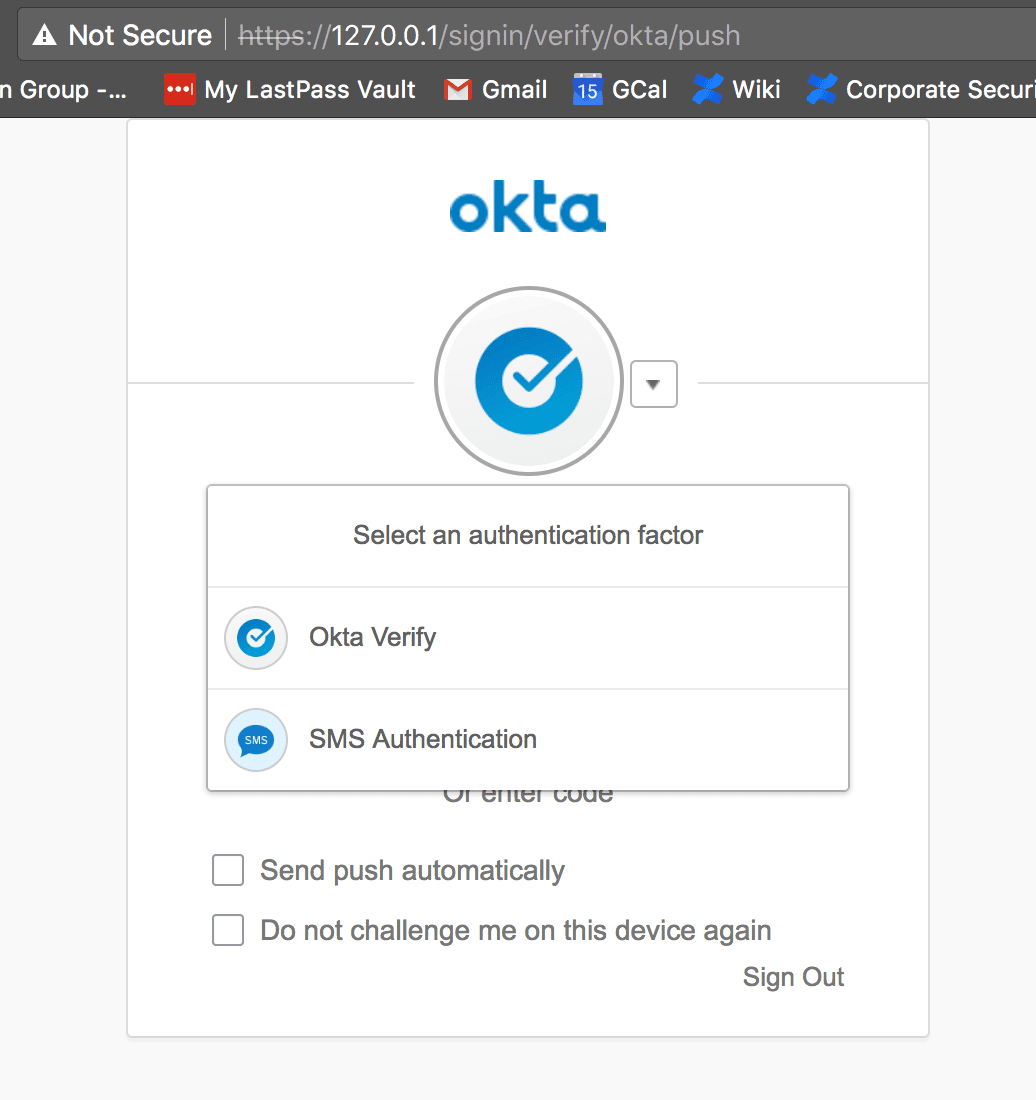
Phishing
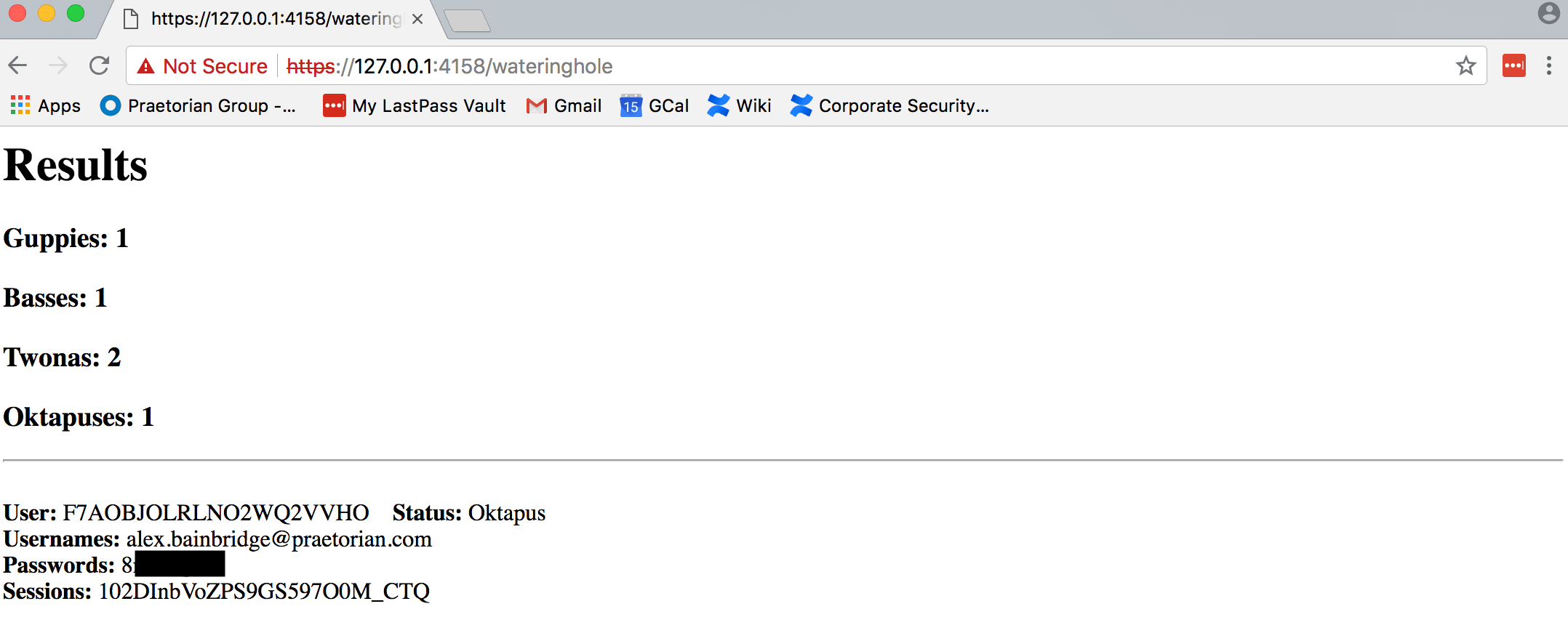
The results server receives data from the phishing server and allows security teams to identify users who were caught, valid credentials, and active Okta sessions. The phishing server acts as a man-in-the-middle to proxy all requests between the target Okta server and the phishing victims. This proxying allows the phishing site to handle almost all two factor authentication methods except for U2F factors. To avoid this issue, the GUI prevents users from selecting U2F factors. Additional options for payload distribution and drive-by download attacks are also present in the tool and can be configured to drop different payloads to visitors. This tool is available on Github and is free for use.
Mitigations
In order to protect against this attack, industry professionals should look to further increase phishing training for users and setup concrete processes for how employees can verify and or report on possible phishing campaigns they receive. Additionally, enforcing the use of U2F factors—instead of traditional two factor devices—will further reduce the risk of phishing due to the authenticity checks performed by U2F devices.
Share via: