Introducing FingerprintX: The fastest port fingerprint scanner

Introduction Port fingerprinting can detect specific services running on a network, which makes it useful during penetration tests. It expands visibility into potential attack surfaces and vulnerabilities within the network environment. Over the summer, our interns worked towards developing a new tool for port fingerprinting services: Fingerprintx Fingerprintx is a port fingerprinting utility tool useful […]
Developing a Hidden Virtual File System Capability That Emulates the Uroburos Rootkit

A few years ago, I read the “Uroburos: The Snake Rootkit” [1] paper written by Artem Baranov and Deresz and was captivated by the hidden kernel-mode Virtual File System (VFS) functionality implemented within Uroburos. Later, I decided to learn Windows device driver programming and thought replicating this functionality within my own rootkit would be an […]
Framework Selection: How to Architect a Systematic Security Program – Part 1
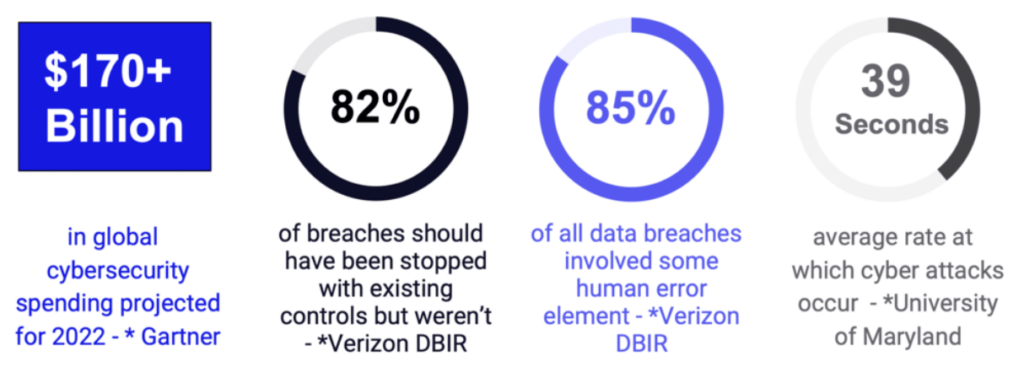
A need for public trust in information systems has driven continuous technological advances and new regulatory requirements, which have in turn made the global cyber threat landscape more complex and connected (see figure 1). As Boards of Directors, regulators, and the public become more aware of this interplay, organizations will need to evolve to address […]
Safeguarding Memory in Higher-Level Programming Languages
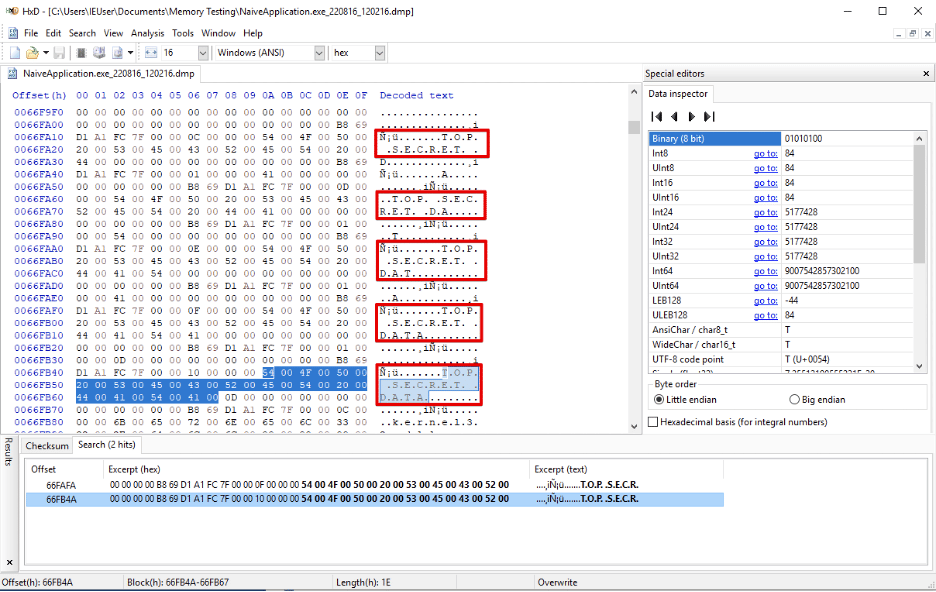
Consider an application written in a higher-level language like Python, NodeJS, or C#. This application must handle sensitive data such as banking credentials, credit card data, health information, or network passwords. The application developers have already hardened the application against malicious users and are confident that it is not vulnerable to database injections, account takeovers, […]
Whitebox Security Assessments: Doing More with More
When deciding on what type of security assessment to get, an organization should consider how much information they are willing to share. Several types of assessments exist, and the key differentiator is how much access an organization grants the testers from the beginning. The terms blackbox, greybox, and whitebox refer to whether a client chooses […]
NTLMv1 vs NTLMv2: Digging into an NTLM Downgrade Attack

Overview During the summer, my colleague Derya Yavuz and I published an article on some of the different methods we’ve leveraged to elevate privileges within Active Directory environments. We discussed authentication coercion techniques such as PrinterBug, PetitPotam, and DFSCoerce. One of the techniques we mentioned in that article was performing an NTLM downgrade attack to […]
NIST CSF 2.0 Workshop Themes: Praetorian’s View
On 17 August 2022, NIST conducted the first Workshop to organize the effort to update the NIST Cybersecurity Framework (CSF) to version 2.0. Praetorian originally submitted comments to the CSF 2.0 RFI in February 2022. This Workshop provided a forum for NIST to frame the discussion around the major topics that emerged from the RFI. […]
Part 3 – Trends in the Cybersecurity Talent Marketplace in the Face of Sustained Shortages
I’ve written previously about how I believe a team’s expertise and talent are the most important factors in determining the success of a cybersecurity program. I’d like to elaborate a bit more on how I think that is affecting the marketplace for cybersecurity expertise and what it means for people operations. To summarize my previous […]
Thinking Outside the Mailbox: Modernized Phishing Techniques
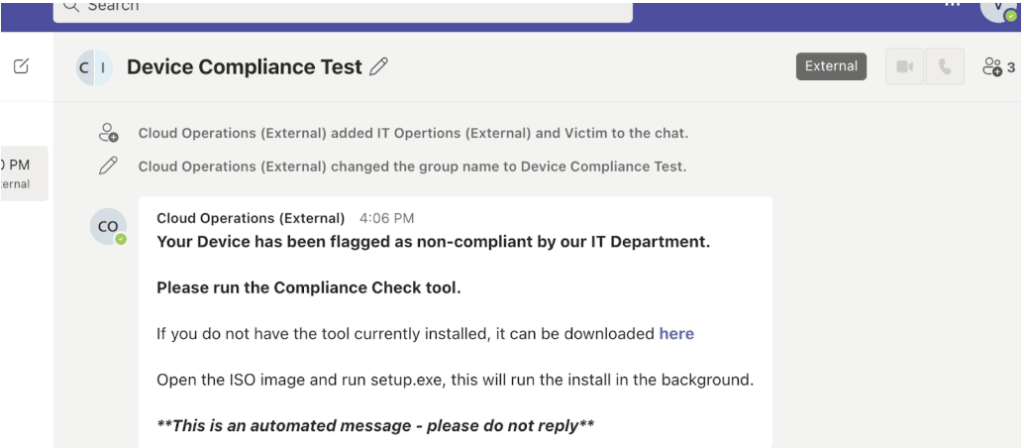
As defensive controls have advanced, so too have adversaries’ approaches to social engineering. Landing a phishing email in an inbox has become harder, and most campaigns that do make it to an inbox are quickly reported, quarantined, or triaged. So, adversaries have asked themselves why not skip the inbox all together or leverage a service […]
The Economy of Trust in Smart Contract Security
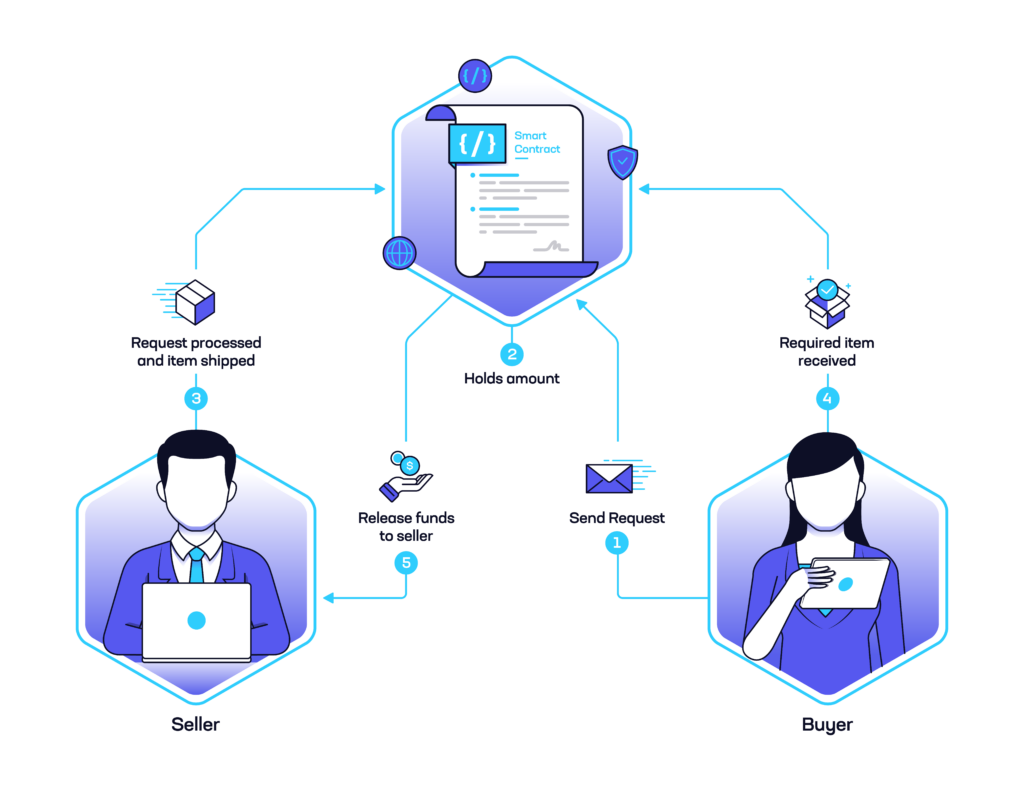
As blockchain and crypto technology transitions from experimental to mainstream, the importance of top-tier security is becoming increasingly relevant. As we discussed in a recent post, organizations are grappling with the fact that risk transference–planning to insure against a cybersecurity incident, or to pay damages out of pocket–is becoming more costly than simply investing in […]