LLM Penetaration Testing
Modern AI and LLM features introduce new attack surfaces — from prompt injection and jailbreaking to data exfiltration and model poisoning. Praetorian’s AI penetration testing and LLM red-team assessments simulate real adversaries across the entire AI stack to uncover exploitable weaknesses, quantify business impact, and deliver prioritized remediation so you can deploy AI with confidence.
Helping you build secure AI ecosystems by breaking them
Modern AI and LLM features introduce new attack surfaces — from prompt injection and jailbreaking to data exfiltration and model poisoning. Praetorian’s AI penetration testing and LLM red-team assessments simulate real adversaries across the entire AI stack to uncover exploitable weaknesses, quantify business impact, and deliver prioritized remediation so you can deploy AI with confidence.
- Identify key risks linked to an organizations AI and ML use.
- Create both technical and process-based controls to solve these problems
- Test the effectiveness of security controls using our industry-leading offensive security team
- Establish a feedback loop between red team/ blue team operations for rapid iteration on security controls
Our Approach to AI Penetration Test
- Discovery & threat modeling — map every AI input/output, data source, and integration
- Attack surface mapping — identify UIs, APIs, RAG sources, agents, plugins, vector DBs.
- Adversarial prompt campaigns — manual + automated adversarial prompts and jailbreak sequences.
- Data & pipeline testing — RAG integrity, egress filtering, context origin attacks, training data poisoning simulations.
- Application & infra testing — OWASP-style checks in the AI context (SSRF, XSS, insecure output handling), plus privilege escalation.
- Impact analysis & remediation — business-risk scoring, playbookable fixes, and follow-up verification.
What we test for
- Prompt injection & jailbreak resistance
- Data leakage and RAG / retrieval pipeline evaluation
- Training/fine-tune poisoning & model backdoor checks
- Model extraction, inversion, and membership inference testing
- App & API abuse (chat UIs, function-calling, tool/plugin misuse)
- Lateral escalation and supply-chain attack scenarios
Risk Management Approach to AI Threats
Praetorian’s Governance, Risk, and Compliance experts use the NIST AI Risk Management Framework and NIST Cybersecurity Framework to analyze the organization’s current state and identify gaps that pose critical threats
Develop AI-Specific Threat Models and Customized Security Controls
Our team assists in creating security controls and enhancing models to address critical vulnerabilities
Targeted Red Team Testing
Our team of experts use the MITRE ATLAS framework to assess the efficacy of security controls and recommended improvements
Build the Most Robust AI Security Playbook
Adversarial Emulation via MITRE ATLAS
OWASP Top 10 for LLMs
Why Choose Praetorian
Praetorian has assembled a cross-functional team of expert enterprise architects, ML research scientists, DevOps engineers, and red team operators. Following the Google Secure AI Framework, we have based our approach on the principle that a team with diverse skillsets can better identify issues, improve defenses, and emulate real- world scenarios.
Identify Supply Chain Risk from Third Party AI Products
Enhanced Security Posture
Strengthen your defenses against the latest advancements in AI, ensuring your organization remains resilient in the face of relentless attacks
Address Material Risks
Identify vulnerabilities and weaknesses within your AI systems, while tailoring solutions to address and mitigate the risks
Build Trust Through Compliance
Demonstrate compliance with industry standards such as NIST AI RMF and build trust among clients and partners
Building Bridges, Breaking Pipelines: Introducing Trajan
TL;DR: Trajan is an open-source CI/CD security tool from Praetorian that unifies Read More
How AI Agents Automate CVE Vulnerability Research
The CVE Researcher is a multi-agent AI pipeline that automates vulnerability research, Read More
What’s Running on That Port? Introducing Nerva for Service Fingerprinting
Nerva is a high-performance, open-source CLI tool that identifies what services are Read More
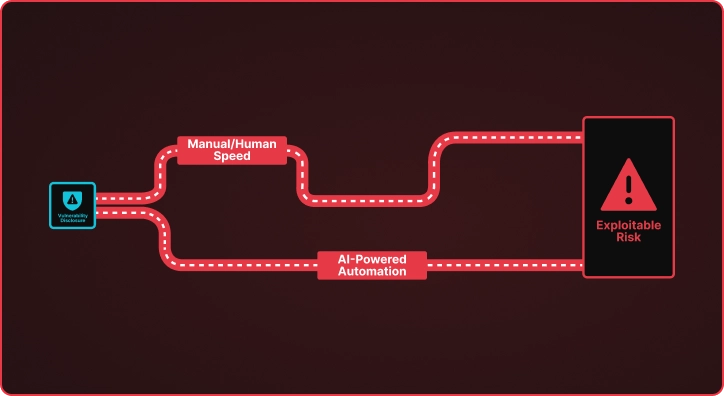
AI-Powered CVE Research: Winning the Race Against Emerging Vulnerabilities
The Vulnerability Time Gap When CISA adds a new CVE to the Read More
There’s Always Something: Secrets Detection at Engagement Scale with Titus
TL;DR: Titus is an open source secret scanner from Praetorian that detects Read More
Praetorian Guard finds critical flaws in OpenClaw – And What It Means for Your Software Supply Chain
At Praetorian, we’re constantly exploring how emerging technologies can strengthen security programs. Read More
Ready to Discuss Your AI/ML Penetrating Testing Initiative?
Praetorian’s Offense Security Experts are Ready to Answer Your Questions