Compromising ByteDance’s Rspack using GitHub Actions Vulnerabilities
Recently, we identified several critical Pwn Request vulnerabilities within GitHub Actions used by the Rspack repository. These vulnerabilities could allow an external attacker to submit a malicious pull request, without the requirement of being a prior contributor to the repository, and compromise the following secrets…
Local Privilege Escalation Vulnerability in Ant Media Server (CVE-2024-32656)
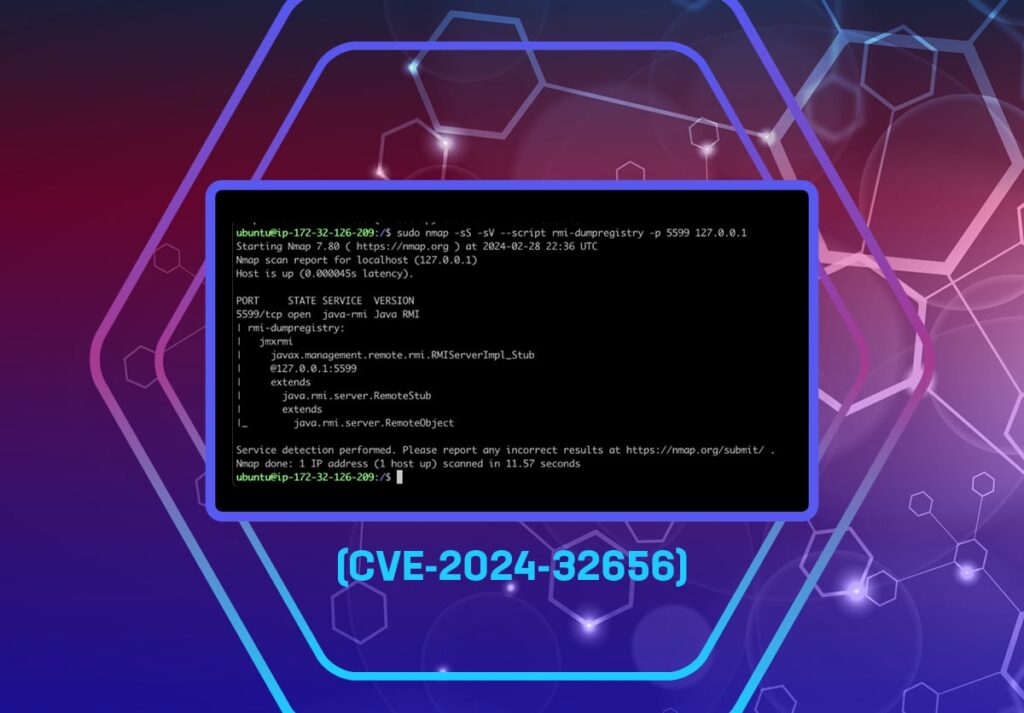
Overview In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities that are likely to impact the security of leading organizations. Recently, we decided to take a look at Ant Media Server with the goal of identifying any vulnerabilities within the application. We performed testing against […]
MeshCentral Cross-Site Websocket Hijacking Vulnerability (CVE-2024-26135)

Overview In this article we discuss a recent cross-site websocket hijacking (CSWSH) vulnerability that we identified in MeshCentral, a web-based remote monitoring and endpoint management solution. MITRE assigned the CVE identifier CVE-2024-26135. End users can use MeshCentral to install agents that communicate with a centralized server. The centralized server then allows users to perform remote […]
Exploiting Kubernetes through Operator Injection
Introduction The Kubernetes documentation describes operators as “software extensions to Kubernetes that use custom resources to manage applications and their components.” These operators automate application resource deployment and management with custom controllers tied to one or more custom resource definitions. Custom controllers create bespoke attack surfaces that attackers can target when they can control custom resource data. […]
Relution Remote Code Execution via Java Deserialization Vulnerability
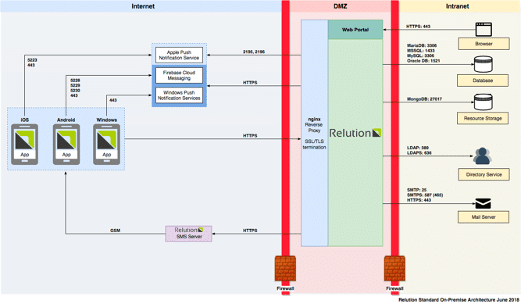
Overview In this article we discuss a recent deserialization vulnerability we found in Relution (CVE-2023-48178), a mobile device management product that is popular among multinational German corporations. CVE-2023-48178 can potentially lead to remote code execution and complete compromise of the MDM application and clients managed by the solution. The deserialization vulnerability exists in a component […]
Understanding the Impact of the new Apache Struts File Upload Vulnerability

Introduction Recently researcher Steven Seeley discovered a way to abuse the popular Apache Struts frameworks’ file upload functionality to achieve remote code execution. This bug, known as CVE-2023-50164, has been assigned a 9.8 CVSS score. No doubt this is causing some security practitioners to have flashbacks of the “good times” that a serious Struts bug […]
SonicWall WXA – Authentication Bypass and Remote Code Execution Vulnerability
Overview In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities that are likely to impact the security of leading organizations. Recently, we were looking at the list of available OVA appliances from SonicWall and identified the WXA appliance image was available for download. We decided […]
Analyzing the SonicWall Custom Grub LUKS Encryption Modifications
Overview Recently, we decided to perform some reverse engineering of the SonicWall NSv appliance to identify any potential remote code execution vulnerabilities within the appliance. During our initial analysis of a virtual machine image for the application, we discovered a customized LUKS encryption mechanism meant to hinder reverse engineering of the application. We were able […]
Technical Advisory: F5 BIG-IP Unauthenticated RCE Vulnerability, CVE-2023-46747
Overview In an effort to safeguard our customers, we perform proactive vulnerability research with the goal of identifying zero-day vulnerabilities that are likely to impact the security of leading organizations. Recently, we discovered a vulnerability which can lead to unauthenticated remote code execution on F5 BIG-IP instances with the Traffic Management User Interface exposed. This […]