How AI Agents Automate CVE Vulnerability Research
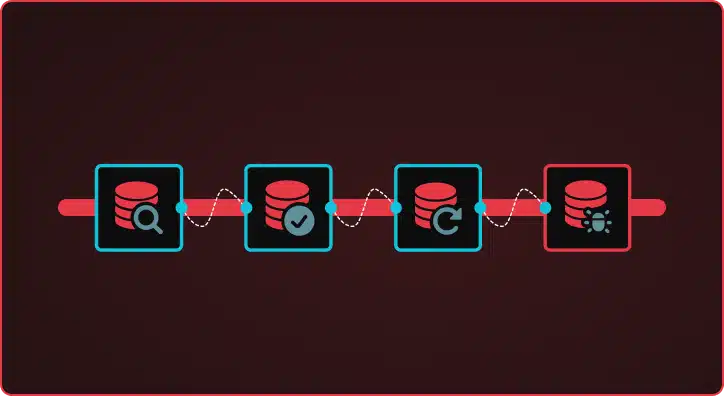
The CVE Researcher is a multi-agent AI pipeline that automates vulnerability research, detection template generation, and exploitation analysis. Built on Google’s Agent Development Kit (ADK), it coordinates specialized AI models through four phases — deep research, technology reconnaissance, actor-critic template generation, and exploitation analysis — to produce production-ready Nuclei detection templates overnight. Beyond Simple Automation […]
AI-Powered CVE Research: Winning the Race Against Emerging Vulnerabilities
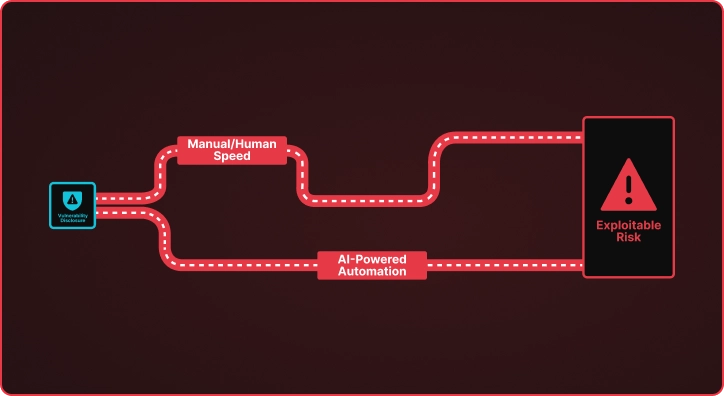
The Vulnerability Time Gap When CISA adds a new CVE to the Known Exploited Vulnerabilities catalog, a clock starts ticking. Security teams must understand the vulnerability, determine if they are exposed, and deploy detection mechanisms before adversaries weaponize the flaw. This process traditionally takes days or weeks of manual research by skilled security engineers who […]
Gone Phishing, Got a Token: When Separate Flaws Combine

TL;DR: Two medium-severity flaws, an unsecured email API endpoint and verbose error messages exposing OAuth tokens, chain together to enable authenticated phishing that bypasses all email security controls, persistent access to Microsoft 365 environments, and full infrastructure compromise. Neither flaw alone would be critical; combined, they’re devastating. Modern web applications increasingly create attack surfaces through […]
Corrupting the Hive Mind: Persistence Through Forgotten Windows Internals
Eventually after you write a tool, the time comes to make it public. That time has come for Swarmer, a tool for stealthy modification of the Windows Registry as a low privilege user. It’s been almost a year since we first deployed this technique in the wild, and given enough time has passed, it seems appropriate […]
CVE-2025-52493: When Password FieldsAren’t Enough – Client-Side SecretExposure in PagerDuty Cloud Runbook
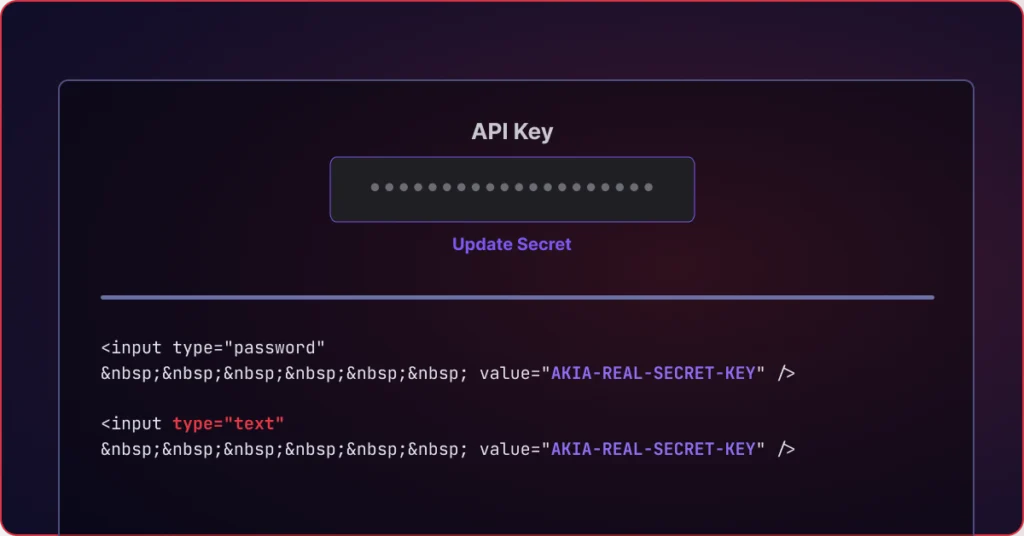
By Mario Bartolome & Carter Ross During a recent Red Team engagement, our team at Praetorian discovered a vulnerability in PagerDuty Cloud Runbook that highlights a fundamental security principle: never trust the client with secrets. In this blog, we share details about CVE-2025-52493, a medium-severity vulnerability that exposed stored secrets to authenticated administrators through simple […]
How I Found the Worst ASP.NET Vulnerability — A $10K Bug (CVE-2025-55315)
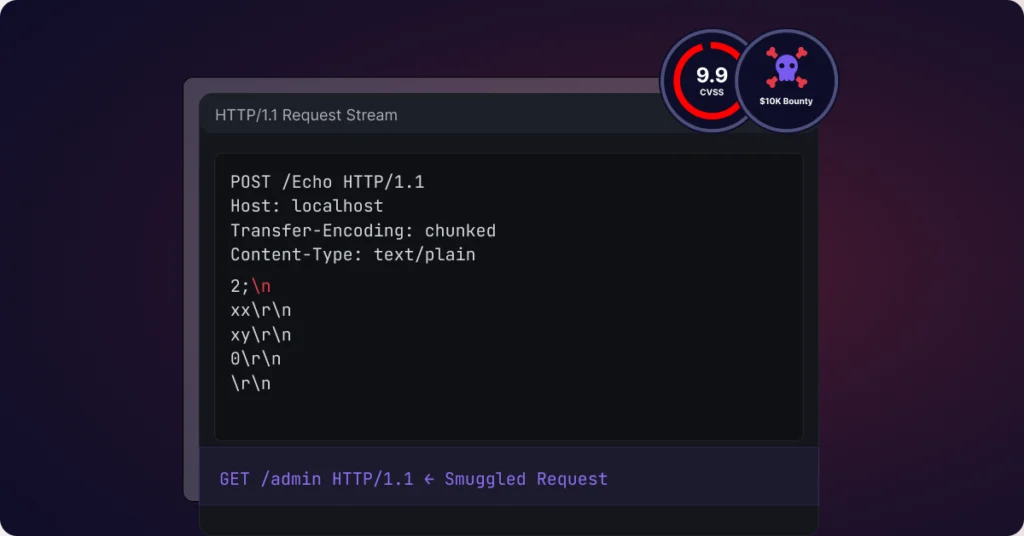
Introduction Earlier this year, I earned a $10,000 bounty from Microsoft after discovering a critical HTTP request smuggling vulnerability in ASP.NET Core’s Kestrel server (CVE-2025-55315). The vulnerability garnered significant media attention after Microsoft assigned it a CVSS score of 9.9, the highest severity rating ever assigned to an ASP.NET Core vulnerability. This post walks through […]
Your Vulnerability Scanner Might Be Your Weakest Link
Overview Vulnerability scanners are a cornerstone of modern security programs, helping teams identify weaknesses before attackers do. But when these tools are configured with privileged credentials, they can themselves become high-value targets. In one case, while running continuous testing through our Chariot platform for a Fortune 500 financial services company, we compromised a server and […]
Domain Fronting is Dead. Long Live Domain Fronting!
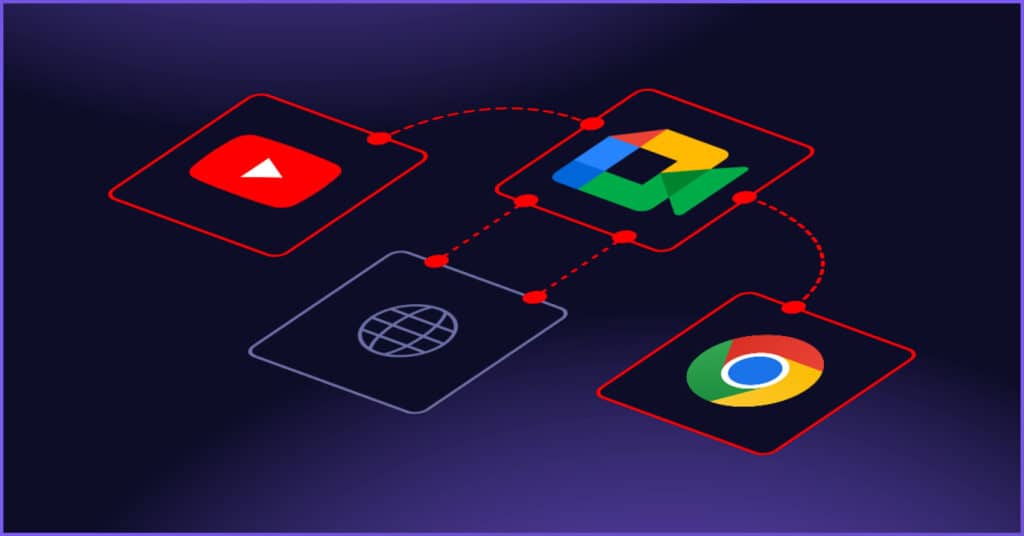
Overview At Black Hat and DEF CON, we demonstrated how red teams could tunnel traffic through everyday collaboration platforms like Zoom and Microsoft Teams, effectively transforming them into covert communication channels for command-and-control. That research highlighted a critical blind spot: defenders rarely block traffic to core business services because doing so would disrupt legitimate operations. […]
OAuthSeeker: Leveraging OAuth Phishing for Initial Access and Lateral Movement on Red Team Engagements
Overview The Praetorian Labs team recently conducted research into potential initial access vectors for red team engagements, focusing on attack techniques leveraging malicious applications distributed through platforms like the Microsoft Store. This included OAuth applications, malicious Outlook extensions, and other types of applications that could be delivered via the Windows Store. As part of this […]
ELFDICOM: PoC Malware Polyglot Exploiting Linux-Based Medical Devices
A high severity vulnerability in DICOM, the healthcare industry’s standard file protocol for medical imaging, has remained exploitable years after its initial disclosure. The flaw enables attackers to embed malicious code within legitimate medical image files. While previous research demonstrated this vulnerability’s impact on Windows-based medical systems, Praetorian’s new proof of concept, ELFDICOM, extends the […]