Inter-Chip Communication: Design Considerations to Mitigate Commonly Overlooked Attack Paths
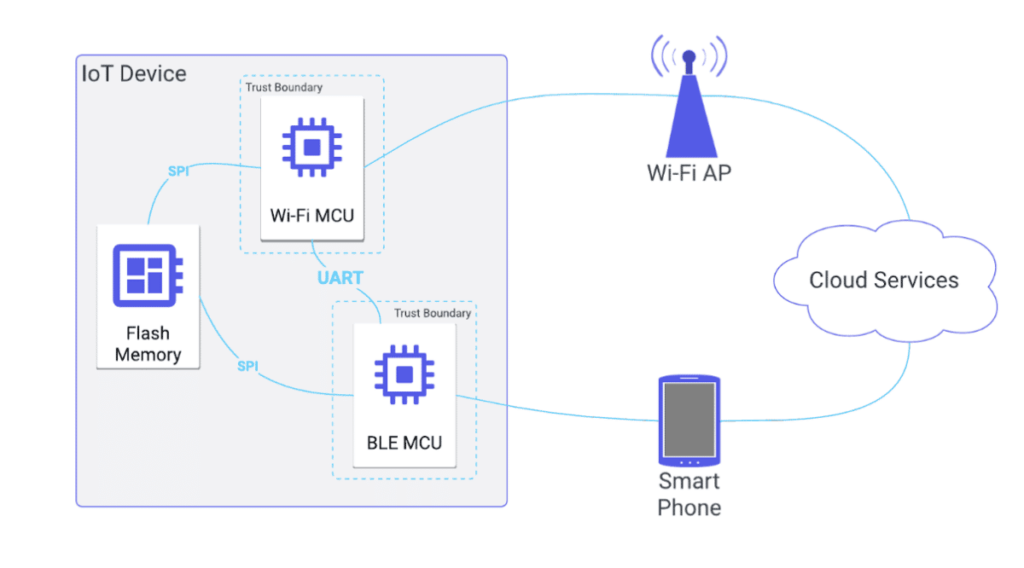
Introduction At Praetorian, we perform security assessments on a variety of Internet of Things (IoT) devices ranging from commodity home “smart” devices, medical devices, critical infrastructure, and autonomous vehicles. While previous blog posts have discussed a general methodology we’ve followed for a complete assessment, the nature of our “chip-to-cloud” security has led us to one […]
Always Be Modeling: How to Threat Model Effectively
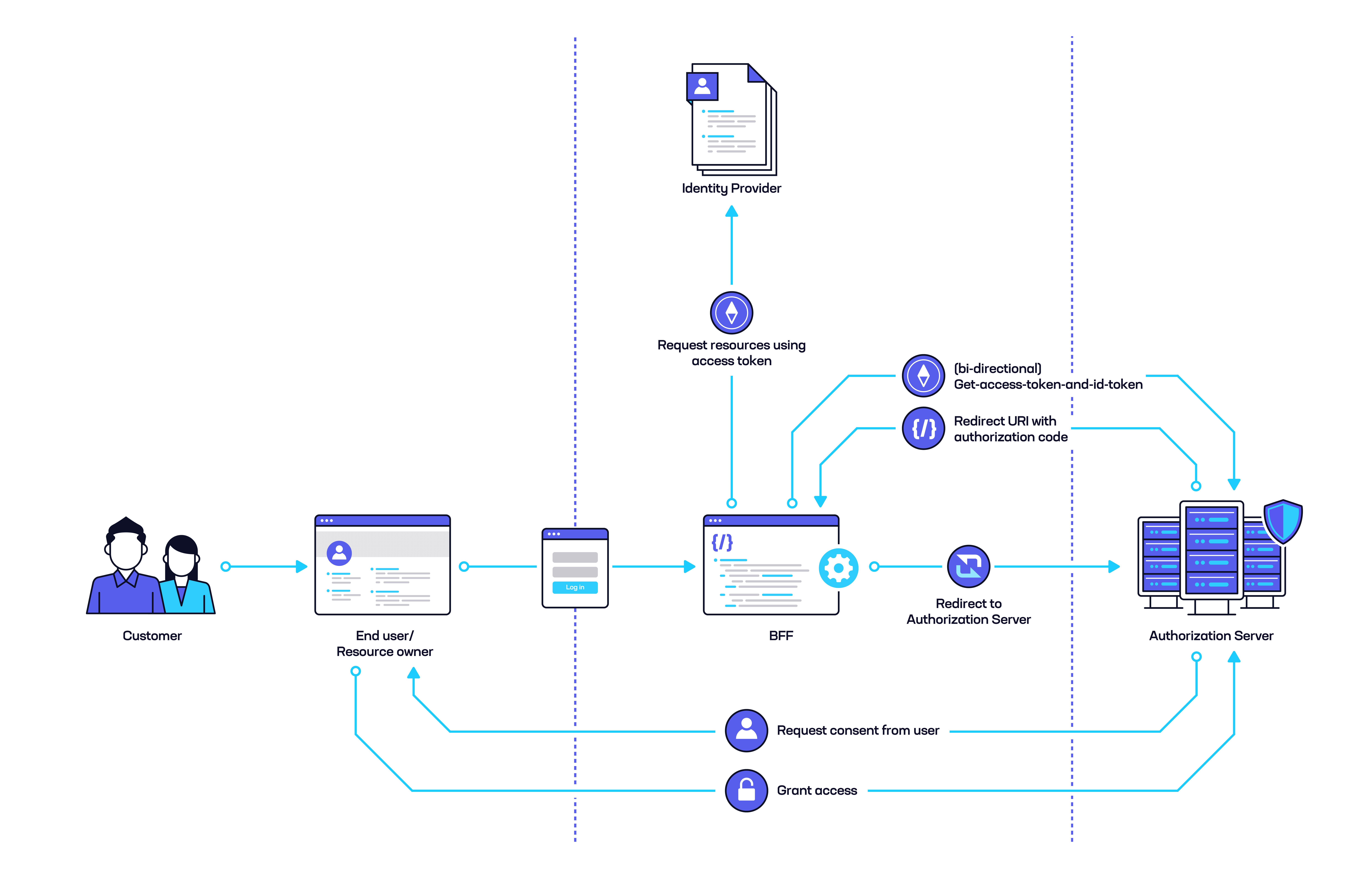
Introduction At Praetorian, we believe that good security advisors always dedicate the start of a security assessment toward understanding your product’s threat landscape. This is why we perform a baseline threat model before every engagement, including those that do not explicitly contain an in-depth threat model analysis. A baseline threat model ensures that we have […]