About Praetorian
We help our customers minimize the likelihood of compromise by using an adversarial perspective to uncover material risks the same way attackers do.
Keeping Our Customers Several Steps Ahead of Attackers
Praetorian is an offensive cybersecurity company whose mission is to prevent breaches before they occur. Praetorian applies an offensive filter to help organizations optimize and prioritize their cybersecurity budget on the initiatives that yield the greatest material risk reduction for the fewest dollars spent.


Who We Are
Our Mission
Our mission is to prevent breaches before they occur.
Our Vision
Our vision is to create a future without compromise.
Our Approach
We protect customers by emulating attackers.
Our Customers
We Are United by these Core Values
Put the Customer first.
Everything else will work itself out.
Default to open.
Don't sugarcoat hard truths.
Yes, and.
Respond with yes to encourage new ideas.
Make craters.
Create impact through mission.
Be humble.
Question your opinions, convictions, and believability.
10X not 10%.
Solution in radical disruption over incremental thinking.
Performance matters.
Set the standard to match the stakes in cyber.
Follow your passion.
Do what you love and do it well.
We are bringing together the world’s security expertise
A concentration of adversarial security expertise
Highly technical engineers and developers with deep security expertise.
Driven to innovate across technology.
We're building next-generation solutions that give our customers a helping hand in protecting themselves.
Powered by an engineering culture.
Our services professionals are security engineers, not consultants. To us, that means real work, real value.
Determined to have an impact and make craters
We are trusted partners devoted to improving the security of our customers.
Expertise at our core
Our people are the top 1%—computer scientists, software engineers, and computer engineers along with the occasional physicist and mathematician that are industry recognized security researchers, open source developers, public speakers, and peer reviewed authors.
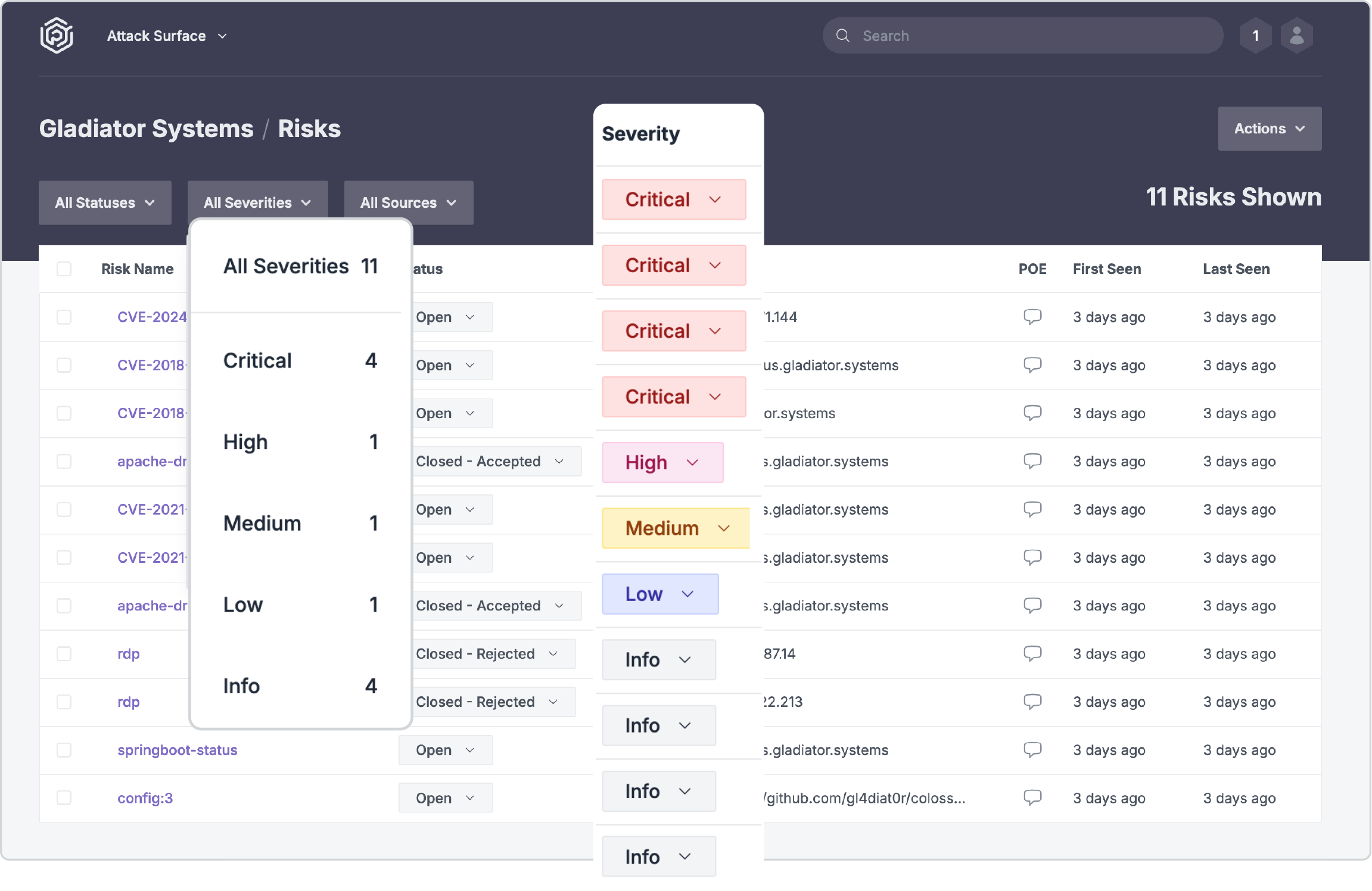
Continuous Threat Exposure Management Platform
Meet Chariot
Chariot combines powerful automation with our veteran team of customer-obsessed engineers. Together, they identify your exploitable vulnerabilities and guide their remediation before threat actors can abuse them.
Advanced Offensive Security
Continuous Threat Exposure Management
Ready to Discuss Your Next Continuous Threat Exposure Management Initiative?
Praetorian’s Offense Security Experts are Ready to Answer Your Questions